Application Control
This page refers to an older version of the product.View the current version of the online Help.
Signature HashingIn this section:
About Signature Hashing
To uniquely identify application files, a hash is taken of the file and stored in the configuration file. A hash is a unique digital signature for a configured application file and is generated using one of the following algorithms.
There are three supported algorithms:
- SHA-1 - The default hashing algorithm applied to each signature item in the configuration.
- SHA-256 - A more complex, but slower hashing algorithm when compared with SHA-1.
- Adler-32 - A lighter weight hashing algorithm when compared to SHA-1.
The hashing algorithm is a global option; this means only one can be set per configuration. This minimizes the amount of hashing that takes place on an endpoint running the configuration. If the hashing algorithm changes, or a file is updated, a rescan is required to generate a new hash code.
As it is a global setting, when Configuration Merging is being used, the algorithm in the base configuration is the one that takes precedent. For further information on Configuration Merging, see Endpoint Configuration Merging.
Rescan File Signatures
When files are updated, for example after a Windows Update, you need to perform a rescan to align the hashing algorithm with the existing hash code.
-
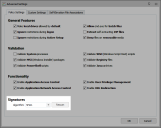
On the Manage ribbon, in the General group, select Advanced Settings.
The Advanced Setting dialog displays.
- To rescan all the updated files in a configuration, under Signatures, select the required algorithm and click Rescan.
-
The Signature Rescan dialog displays when the scan is complete.
The dialog contains three tabs:
-
Actions Required - This tab displays when the signature rescan fails to find a previously hashed file or when a file path does not match the file stored in the configuration.
All missing files must be removed or manually located before the Signature Rescan dialog is closed.
- Changed - This tab contains an overview of all the application files that the new hashing algorithm has been applied to and their associated paths.
- Unchanged - This tab contains an overview of all the application files that already have the selected algorithm and have therefore not been changed.
-
- If the rescan finds
missing files, do one of the following:
- To delete the missing file from the configuration, select the filename from the Actions Required tab and click Remove from configuration.
To locate the missing file manually, click the ellipsis, adjacent to the missing file and navigate to the file location.
Click Export List to produce a full report, in CSV format, that provides details of any files that are missing, changed or remain unchanged. The report provides details of the associated Rule Name, File, Hash and Status of all the hashed signature items. The exported report file can be opened in a spreadsheet so the data can be examined and queries run.
-
Click OK.
Any missing files must be removed or manually located before clicking OK.
The new hashing algorithm is applied and saved to all updated files in the Application Control configuration.
Apply a New Hashing Algorithm
Hashing algorithms can be applied to all files listed in an Application Control Configuration to help improve performance or to comply with localized rules and regulations. The following procedure shows you how to apply a new algorithm.
-
In the Manage ribbon, in the General group, select Advanced Settings.
The Advanced Setting dialog displays.
-
To change the hashing algorithm for all files in a configuration, select the algorithm type from the Algorithm drop-down. When a new algorithm is selected from the drop-down, a rescan of all files in the configuration is automatically triggered.
The Signature Rescan dialog displays when the rehashing is complete. This may take a few minutes, depending on the number of items being processed and the type of algorithm being applied.
The dialog contains three tabs:
-
Actions Required - This tab displays when the signature rescan fails to find a previously hashed file or when a file path does not match the file stored in the configuration.
All missing files must be removed or manually located before the Signature Rescan dialog is closed.
- Changed - This tab contains an overview of all the application files that the new hashing algorithm has been applied to and their associated paths.
- Unchanged - This tab contains an overview of all the application files that already have the selected algorithm and have therefore not been changed.
-
- If the rescan finds
missing files, do one of the following:
- To delete the missing file from the configuration, select the filename from the Actions Required tab and click Remove from configuration.
To locate the missing file manually, click the ellipsis, adjacent to the missing file and navigate to the file location.
Click Export List to produce a full report, in CSV format, that provides details of any files that are missing, changed or remain unchanged.
The report provides details of the associated Rule Name, File, Hash and Status of all the hashed signature items. The exported report file can be opened in a spreadsheet so the data can be examined and queries run. -
Click OK.
Any missing files must be removed or manually located before clicking OK.
The new hashing algorithm is applied and saved to the Application Control configuration.
Related topics
This page refers to an older version of the product.View the current version of the online Help.
The topic was:
Inaccurate
Incomplete
Not what I expected
Other
Copyright © 2019, Ivanti. All rights reserved.