Policy Change Requests
In this section:
- About Policy Change Requests
- Configure Change Requests for a Rule
- Configure Request Types
- Management Services
- Endpoint User - Create a Policy Change Request
About Policy Change Requests
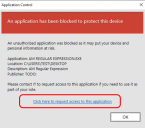
Desktop and mobile users can use the Policy Change Request feature to request an update to an Application Control configuration via email or telephone. Application Control also offers endpoint users the ability to submit requests directly to Ivanti Neurons for ITSM and ServiceNow. The requests can be made from a link on the Application Control Access Denied dialog or by using the Application Control Policy Change Request executable installed on their desktop.
Policy Change Request settings are configured per rule and are evaluated at session connect and when a configuration changes. The email address, telephone number, and text for change requests is set globally and used for all groups with the appropriate settings applied.
The legacy Policy Change Request feature is compatible with 32-bit and 64-bit versions of Chrome, Edge and Internet Explorer 9, 10 and 11 .
Ivanti Service Manager (Ivanti Neurons for ITSM) Integration (for 2021.3 and later versions)
For organizations with licenses for Ivanti Neurons for ITSM (or Ivanti Service Manager), Application Control 2021.3 introduces the ability to integrate Policy Change Requests directly into your service desk system. This enables optimization of your service desk processes and auditing of the complete change request workflow. Refer to Policy Change Request - Ivanti Service Manager (Ivanti Neurons for ITSM).
ServiceNow Integration (for 2022.1 and later versions)
For organizations with licenses for ServiceNow, 2022.1 introduces the ability to integrate Policy Change Requests directly into the ServiceNow desk system. Refer to Policy Change Request - ServiceNow Integration.
Localization for Ivanti Neurons for ITSM and ServiceNow
The device end-user dialog is localized and will be displayed in the language the user has selected in their system account. The options that are retrieved from Ivanti Neurons for ITSM\ServiceNow (Duration, Request Type (Action), Components) for the device end-user will be translated from the English language of the admin side into the appropriate language for the device end-user. Please note that these must be in English on the server otherwise they will not be displayed correctly.
Upgrading Policy Change Request settings
Policy Change Request behavior changed from being a global setting to being applied for each rule in Application Control 10.1. This change prevents agents from current software from processing change requests created from endpoints with pre-10.1 configurations.
To ensure the Policy Change Request feature continues to function correctly in the 10.1 release, you will need to upgrade all configurations within the 10.1 Application Control console and redeploy.
The Application Control Agent and the Application Control Web Services must be at the same version.
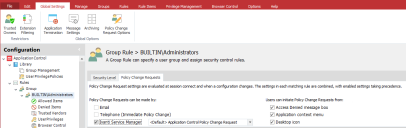
Configure Change Requests for a Rule
Configure which request types and features are available to users for each rule. Policy Change Request settings are available for all rule types, apart from Process rules.
- Select a rule in the navigation pane.
- Select the Policy Change Requests tab.
- Select how Policy Change Requests can be made:
- Telephone (Immediate Policy Change)
- ITSM
The ITSM is populated with catalog items picked in the Ivanti Neurons for ITSM or ServiceNow tab. The console will not select both, so as far as this option, it is either in ServiceNow mode or Ivanti Neurons for ITSM mode, but not both.
- Select the methods by which users can initiate Policy Change Requests:
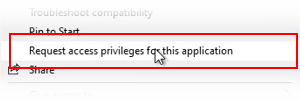
- Access Denied message box - Users click a link in the message box that displays when a user attempts to access a prohibited application.
- Application context menu - Users select an option from the context menu of prohibited applications.
- Desktop icon - Users use a desktop shortcut icon to raise change requests from the Policy Request dialog.
Note, it is possible to select both the Email and Telephone option, or one of the ITSM options.
Details for each setting are configured using the Policy Change Requests dialog, accessed from the Global Settings ribbon.
Configure Request Types and Methods
To configure request types and methods, select Policy Change Request Options from the Global Settings ribbon.
Request Types
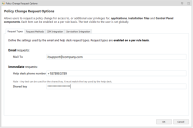
Configure email and immediate policy change requests in the Request Types tab on the Policy Change Requests dialog.
Email Requests
When a user is prompted to elevate their privileges to run an application, they can click a link in the Access Denied message box to request a permanent configuration change. When the user clicks the link, they are prompted to enter the reason for the change request, which is sent to the email address configured in the Application Control console.
The Email Request function uses Messaging Application Programming Interface (MAPI) to send emails. An Application Control administrator reviews the request, and if the request is granted, updates the configuration and deploys the AAMP file.
To set up email change requests, enter the email address to which change requests are sent in the Mail To field.
You can only add one email address. To send the request to multiple email addresses you can configure a group email (distribution list).
Immediate Requests
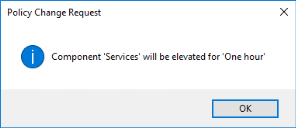
Immediate requests allow users, typically mobile users, to request a permanent or temporary configuration change. When users click the immediate request link, they are provided with a phone number to call and issued with details of the request and a request code. The request code and the configuration change request are relayed to IT Support, who enter the details in the Help Desk Portal. IT Support generate a response code and send it to the user to enter in the Policy Change Request dialog.
Users get three attempts to enter a response code. After three incorrect attempts the dialog closes and the changes are not applied. If configured, when the dialog closes, a 9091 event is raised. If the user requires further configuration changes, they must restart the process. If the code is entered correctly, users have elevated access to the application. Upon confirmation, users are presented with details of the elevation.
Configure the following fields in the Request Types tab:
- Helpdesk Phone Number - The number users are prompted to call to request the immediate configuration change.
-
Shared Key - The shared key is an integral part in processing Immediate requests and is embedded and encrypted in the configuration. The shared key must match in both the Application Control Console and the Help Desk Portal. If the shared keys do not match, a response code cannot be created and configuration change will not be authorized for deployment to the user's endpoint.
The shared key can be changed using the Help Desk Portal, however if the shared key is amended in the Portal, the same key must also be entered in the Application Control Console.
Once you have configured the Immediate Request settings in a configuration file, deploy it to your endpoints. Before the feature is fully activated, the Help Desk Administrator and Help Desk Operator roles must be assigned to members of your Support Team. Once you have deployed the configuration and assigned Help Desk Administrator role, the Help Desk Administrator can assign or remove additional Help Desk Operators and/or Administrators.
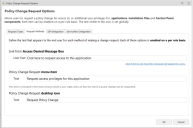
Request Methods
In the Request Methods tab, configure the text for policy change request items:
- Link from Access Denied Message Box
Link Text - Text for the request link displayed in the Access Denied Message Box presented to the end user. The default text is Click here to request access to this application. - Policy Change Request
Text - Text for the context menu displayed when a user right-clicks an item eligible for a policy change requests - Policy Change Request desktop icon
Text - The name of the policy change request desktop icon. Users can click or select the icon to open the Application Control Policy Change Request dialog and create change requests.
Management Services
Application Control integrates with two services:
-
See Ivanti Service Manager for further details for the Ivanti Neurons for ITSM integration.
-
See ServiceNow for further details for the ServiceNow integration.
Endpoint User - Create a Policy Change Request
When integration is enabled, endpoint users can initiate and create Policy Change Requests according to the methods configured in the template (refer to step 4 in Configure Change Requests for a Rule).
Initiate a Request
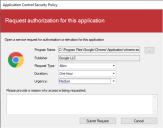
Program Name: Depending upon how the request was initiated, this field may be pre-populated. Ensure the required item is specified.
If required, click the ellipses icon and browse to select the application required.
Publisher: If the selected application is signed the software publisher name is displayed. The field will remain blank for unsigned executables.
Request Type: Users select the permission required. The options available are determined by the request configuration but will typically include: Allow or Allow and Elevate for example.
Duration: Users select the duration required for the change in policy. The options available are determined by the request configuration.
Urgency: Users provide an understanding of how quickly this authorization needs to occur.
Please provide a reason why access is being requested:Optionally, the user can enter a reason for the request.
Click Submit Request or Cancel
Endpoint User - Challenge Response dialog
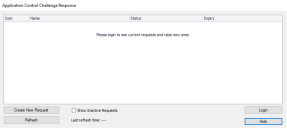
The Application Control Challenge Response dialog lists Policy Change Requests submitted by the individual user. It shows the request status and date of expiry.
Users can right-click a request and select options from the context menu:
-
DetailsThe Service Request Details window is displayed. It lists attributes of the request. Depending upon the request status, the Owner of the request is included and this can assist with any required progress chasing or querying of specific requests.
-
Resubmit The availability of this option depends upon the request status.
The dialog is automatically displayed when a poll to the Ivanti Neurons for ITSM server returns a change to the status of a user's request. A toast notification is also displayed and a taskbar icon indicates that Ivanti Neurons for ITSM is active. The user can open the dialog at any time via the following methods:
-
Double-click the Policy Change Request desktop icon
-
Select Create New Request within Application Control
-
Double-click the taskbar icon (
 ).
).
The different status names (or states), and the number of them, is configured within the Ivanti Neurons for ITSM system. Typically this includes: Submitted, Active, Approved and Expired.
Approved status signals that the change request has been fulfilled. In the case of requesting access to a specific application for example, Approved means user has access with immediate effect.
Note, Policy Change Requests processed via Ivanti Neurons for ITSM enable Administrators to revoke request approval if required. For example, if a risk or question emerges relating to an Approved change the Ivanti Neurons for ITSM Administrator may change the request status to Active and request advice. With the status returned to Active, the permission is withheld.