Trusted Owners
In this Section:
About Trusted Owners
During the rule matching process, Trusted Ownership checking is performed on files and folders to ensure that ownership of the items is matched with the list of trusted owners specified in the default rule configuration.
For example, if a match is made between the file you want to run and an allowed item, an additional security check ensures that the file ownership is also matched with the Trusted Owners list. If a genuine file has been tampered with or a file that is a security threat has been renamed to resemble an allowed file, trusted ownership checking identifies the irregularity and prevents the file execution.
Network folders/shares are denied by default. So, if the file resides on a network folder, the file or folder must be added to the rule as an allowed item. Otherwise, even if the file passes Trusted Ownership checking, the rule will not allow access.
Trusted ownership checking is not necessary for items with digital signatures because these cannot be imitated.
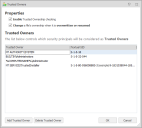
The list of Trusted Owners is maintained in the Trusted Owners dialog available from the Global Settings ribbon. Application Control trusts the following by default:
- SYSTEM
- BUILTIN/Administrators
- %ComputerName%\Administrator
- NT Service\TrustedInstaller
This means that, by default, Application Control trusts files owned by the BULTIN\Administrators group and the local administrator. Application Control does not do group lookups for Trusted Owners – users who are members of the BUILTIN\Administrators are NOT trusted by default. Other users, even if they are members of the Administrators group, must be explicitly added to become Trusted Owners. You can extend the list above to include other users or groups.
When using Application Control for the first time, we recommend you use the default settings. To avoid complex customizations do not extend the Trusted Owners list or change any default settings.
The dialog contains the following options:
-
File Overwrite and Rename - When the option Change a file's ownership when it is overwritten or renamed is selected, Application Control selectively changes the NTFS file ownership of executable files when they are overwritten or renamed.
Attempts by a user who is not a Trusted Owner to overwrite a file that is allowed due to Trusted Ownership or an Allowed Item rule, could constitute a security threat if the file contents have changed. Application Control changes the ownership of an overwritten file to the user performing the action, making the file untrusted and ensuring that the system is secure.
Likewise, attempts to rename a denied file to the name of an allowed item could also constitute a security threat. Application Control also changes the ownership of these files to the user who performs the rename action and ensures the file remains untrusted.
Overwrite and rename actions are both audited.
- File Overwrite and Rename - To ignore Trusted Ownership for individual files do one of the following:
- Clear the Trust Ownership check box in the Allowed Items sub-nodes.
- Assign self-authorization status to users and devices to allow the user to decide whether or not to allow a file to run.
- Set the Self-Authorizing security level for a rule in the Group, User, Device, Custom, Scripted, and Process rule nodes.
- Trusted Applications override restrictions resulting from matches with Denied Items.
- Trusted Vendors override restrictions resulting from Trusted Ownership checking.
Allowlists
If you prefer to use a white list approach where nothing is allowed to run by default, clear the Make local drives allowed by default check box in the Policy Settings dialog available from Advanced Settings in the Global Settings ribbon. To make items allowed, add them to the Allowed Items folder of a configuration node.
If you use a allowlist approach, ensure that you allow important system files to run by adding a Group rule for the Everyone group in which all of the relevant files or folders have been added to Allowed Items. Otherwise, many crucial executable files and DLLs, such as those that are stored in the system32 directory can be prevented from running and adversely affect correct system functioning.
The following video provides an introduction to the concepts used in Trusted Ownership:
Trusted Ownership Why? What? How
Enable Trusted Ownership
To enable this feature, select Trusted Owners from the Global Settings ribbon and configure the required settings:
- Enable Trusted Ownership checking - Select to switch on Trusted Ownership checking. Selected by default.
-
Change a file's ownership when it is overwritten or renamed - Select to change the ownership of any trusted allowed file which is overwritten by an untrusted user, who is not in the Trusted Owners list.
When a denied file is renamed by an untrusted user, in an attempt to bypass a denied item rule, the ownership is changed to the untrusted user. Once the ownership has changed, Trusted Ownership checking then prevents the file from being executed.
- Trusted Owner - The Trusted Owner details.
- Textual SID - The Textual Security Identifier of the Trusted Owner. For example, S-1-5-32-544.
- Add Trusted Owner button - Launches the Add Trusted Owners dialog. Enter or browse to select an account to add to the Trusted Owner list.
- Delete Trusted Owner button - Deletes the selected Trusted Owner.
Test Trusted Ownership
- Introduce one or more applications using a test user account.
- Copy one or more applications to the user’s home drive or another suitable location, such as calc.exe from the System32 folder or copy a file from a CD.
- Attempt to run a copied file. The application is denied because the files are owned by the test user and not a member of the Trusted Owners list.
You can verify the ownership of a file by viewing the Properties using Windows Explorer.