This page refers to an older version of the product.View the current version of the online Help.
Managing Configurations
Policy Configurations are built using the framework provided in the Policy Configuration tree within the Environment Manager console.
At the top level, the hierarchy consists of three fixed nodes:
- Library - Contains reusable nodes and conditions referenced in the configuration
- Computer Triggers - Contains triggers relating specifically to the endpoint
- User - Contains triggers relating specifically to user actions
- Configurations are created within the Computer and User nodes by using a combination of the following elements:
- Triggers are static elements found within the Computer and User nodes which represent the events which ultimately trigger actions. Examples of triggers are Computer Startup and Process Stopped.
- Nodes are essentially containers that allow conditions and actions to be associated with triggers. Nodes act as the placeholders to create the hierarchy of the configuration, controlling dependencies and defining processing order.
- Conditions define the rules which specify when actions are carried out. For example, a condition might be created which applies to certain computers or user names. They allow actions to be targeted allowing greater flexibility and customization.
- Actions are applied when conditions are met after a trigger is fired. For example, mapping drives and printers, creating shortcuts and registry keys.
- Lockdown actions are also available. These are provided to disable or remove application items and functionality. For example, disabling a menu option or button in an application or prohibiting the use of certain keyboard shortcuts.
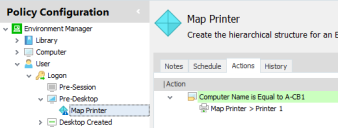
By building up these elements, a configuration is created which controls endpoint usage and user access. For example:
| Fixed Node | Trigger | Node | Condition | Action |
|---|---|---|---|---|
| User | Logon | Map Printer | Computer Name is Equal to Endpoint 1 | Map to Printer 1 |
The simple configuration above maps Printer 1 at logon for the computer Endpoint 1. During logon, the Environment Manager agent checks the managed computer against that specified in the condition, Endpoint 1. If the condition is met, the action to map the printer to Printer 1 runs. If the managed computer is anything other than Endpoint 1, the action is ignored.
In the Environment Manager console, the example would be as follows: