Auditing
In this section:
About Auditing
The Application Control Auditing feature allows you to define rules for the capture of auditing information and to raise events, and includes a filter for specifying the events you wish to capture in the log. Auditing is accessed from the Manage ribbon.
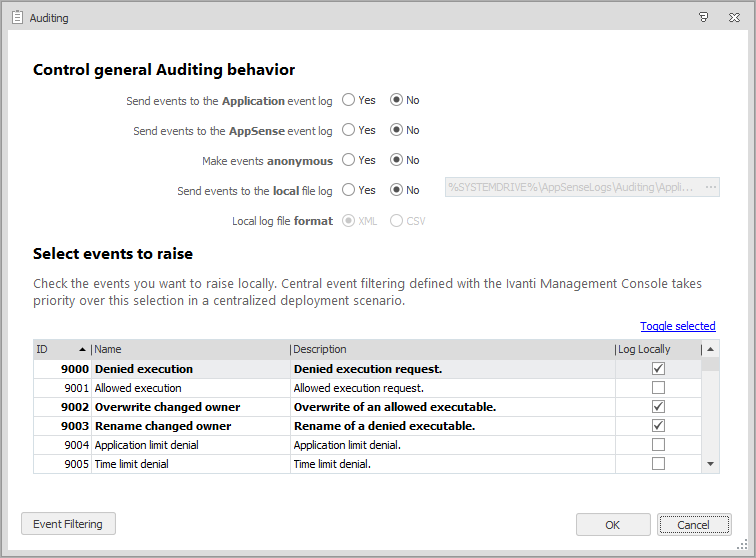
Control General Auditing Behavior
Use the following options to control the general auditing behavior and select the events to be raised:
- Send events to the Application Event Log - Select whether to send events to the Application Event Log.
- Send events to the AppSense Event Log - Select whether to send events to the AppSense Event Log. You can only send the events to the Application Event Log or the AppSense Event Log.
- Make events anonymous - Specify whether events are to be anonymous. If, Yes, the computer name and user name is omitted from all events. Anonymous logging also searches the file path for any instances where a directory matches the username and replaces the directory name with the string
- Send events to local file log - Select whether to send events to the local file log. If Yes, the events are sent to the local log file specified in the Text box. The default location is: %SYSTEMDRIVE%\AppSenseLogs\Auditing\ApplicationManagerEvents_%COMPUTERNAME%
- Local file log format- Specify whether the event log is to be saved in XML format or CSV format.
In Enterprise installations, events can be forwarded to the Management Center via the Deployment Agent (CCA). When using this method for auditing, event data storage and filtering is configured through the Management Center console.
For more information, refer to the Management Center Help.
Select Events to Raise
This section of the dialog lists all Application Control events. Select the Log Locally checkbox for the events you want to raise locally, in accordance with the selected auditing behavior options.
Note that some events are subject to event filtering, so in addition to enabling them via the Log Locally checkbox, you will need to ensure Event Filtering is also configured as required.
Available Events
| Event ID | Event Name | Event Description |
|---|---|---|
| 9000 | Denied Execution | Denied execution request. |
| 9001 | Allowed Execution | Allowed execution request. A single request for an application can generate multiple 9001 events due to the way in which Windows responds to execution requests. So it's good practice to use event 9015 to accurately audit how many times a user has run an application. |
| 9002 | Overwrite Changed Owner | Overwrite of an allowed executable. |
| 9003 | Rename Changed Owner | Rename of a denied executable. |
| 9004 | Application Limit Denial | Application limit denial. |
| 9005 | Time Limit Denial | Time limit denial. |
| 9006 | Self-Authorization | Self-authorization decision by user. |
| 9007 | Self-Authorized allow | Self-authorization execution request. |
| 9009 | Scripted Rule Timeout | Script execution timed out. |
| 9010 | Scripted Rule Fail | Script failed to complete. This event is only raised for VB script failures. |
| 9011 | Scripted Rule Success | Script completed successfully. |
| 9012 | Trusted Vendor Denial | Digital Certificate failed Trusted Vendor check. |
| 9013 | Network Item denied | Denied Network Item request. |
| 9014 | Network Item allowed | Allowed Network Item request. |
| 9015 | Application Started | An allowed application started running. A single request for an application can generate multiple 9001 events due to the way in which Windows responds to execution requests. So it's good practice to use event 9015 to accurately audit how many times a user has run an application. |
| 9016 | Unable to change ownership | The file's ownership could not be changed. |
| 9017 | Application Termination | A denied application has been terminated by Application Control. |
| 9018 | Application User Privileges Changed | The application's user privileges have changed. See also 9023. |
| 9019 | Web Installation allowed | Allowed Web Installation request. |
| 9020 | Web Installation restricted | Restricted Web Installation request. |
| 9021 | Web Installation restricted | Windows Restricted Web Installation request. |
| 9022 | Web Installation fail | Web Installation failed to complete. |
| 9023 | Self-Elevation allowed | Self-Elevation requests. Also used in lieu of the 9018 event where Rule Item User Privilege Applications have been configured to prompt the user before elevation. |
| 9024 | URL Redirection | URL Redirection has occurred. |
| 9051 | Policy Change granted | A Policy Change Request has been granted. |
| 9052 | Policy Change invalid response code | An invalid response code has been entered for a Policy Change Request. |
| 9053 | User-requested allow | An allowed Policy Change application has started. |
| 9054 | User-requested elevate | An elevated Policy Change application has started. |
| 9055 | Service start/stop | A service has been started or stopped. |
| 9056 | Untrusted file with metadata match | Failed to verify the certificate of a signed file when matching metadata. |
| 9060 | Denied execution (Trusted Ownership) | Denied execution request (Trusted Ownership) |
| 9061 | Denied execution (Rule Policy) | Denied execution request (Rule Policy) |
| 9062 | Application started elevated | An application started with elevated (full administrator) rights. |
| 9063 | UAC Replacement - Auditing | User-supplied reason for the requirement of elevated privileges. |
| 9064 | Windows Component started elevated | A Windows Component started with elevated (full administrator) rights. |
| 9096 | Configuration merge success | The configuration merge has completed successfully. |
| 9097 | Configuration merge fail | The configuration merge has failed. |
| 9098 | Configuration merge timeout | The configuration merge has timed out waiting for expected files. |
| 9099 | Agent not licensed | Application Control is not licensed. |
Notes
-
A single request for an application can generate multiple 9001 events due to the way in which Windows responds to execution requests. So it's good practice to use event 9015 to accurately audit how many times a user has run an application.
9001, 9007, 9014 and 9015 events are disabled by default as they can generate excessive event data on busy endpoints. We recommend these events are only used for troubleshooting purposes, and only for short periods of time.
-
The 2020.2 release of Application Control introduced event IDs: 9060 and 9061. By default both events are disabled. If required, they enable organizations to differentiate execution requests blocked by Trusted Ownership from those blocked explicitly by a Rule Policy.
To achieve this distinction, enable event IDs 9060 and / or 9061 as required. To prevent duplicate notifications if you enable either (or both) of these settings, you should disable event ID 9000.
-
The 2020.2 release also introduced event ID 9062. It identifies processes started using full admin rights and can be valuable in assessing what elevated rights are required. Note, that when Windows UAC is disabled, or when the built-in admin account is in use, all processes will run using full admin rights resulting in many notifications.
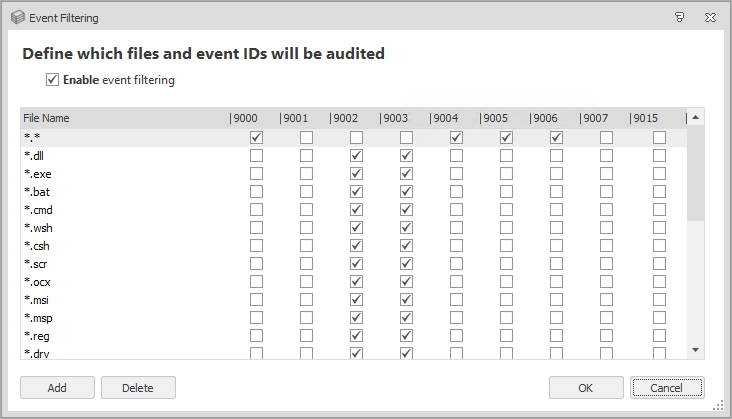
Event Filtering
Event Filtering allows you to filter the file types that you want to audit. This is particularly useful if you choose a high volume event. The event filtering dialog is accessed by clicking Event Filtering in the Auditing Dialog. Enable event filtering is enabled by default and comes pre-configured to get started quicker.
Update the settings as required, selecting the file types to audit for each listed event. Click Add to specify new file types for the required event types.
By default, all 9001, 9007, and 9015 events will not be raised as they are completely filtered out.
Select the file types to audit for each listed event. Use Add to specify new file types for the required event types.
It is possible to override the event filtering and cause certain rules to raise events that otherwise would have been filtered out. This is enabled via the Ignore Audit Event Filtering option in the Allow and Denied items dialogs.
Ignore event filtering does not work with event 9015.
Event Filtering applies to both events raised to the local event log and to events raised to the Management Center.
System Events
The following are non-configurable system events:
| Event ID | Event Name | Event Description |
|---|---|---|
| 8000 | Service Started | Application Control Agent: Service Started. |
| 8001 | Service Stopped | Application Control Agent: Service stopped. |
| 8095 | No Configuration found | Application Control cannot find a valid configuration. |
| 8099 | Invalid License | Application Control software is not licensed. |