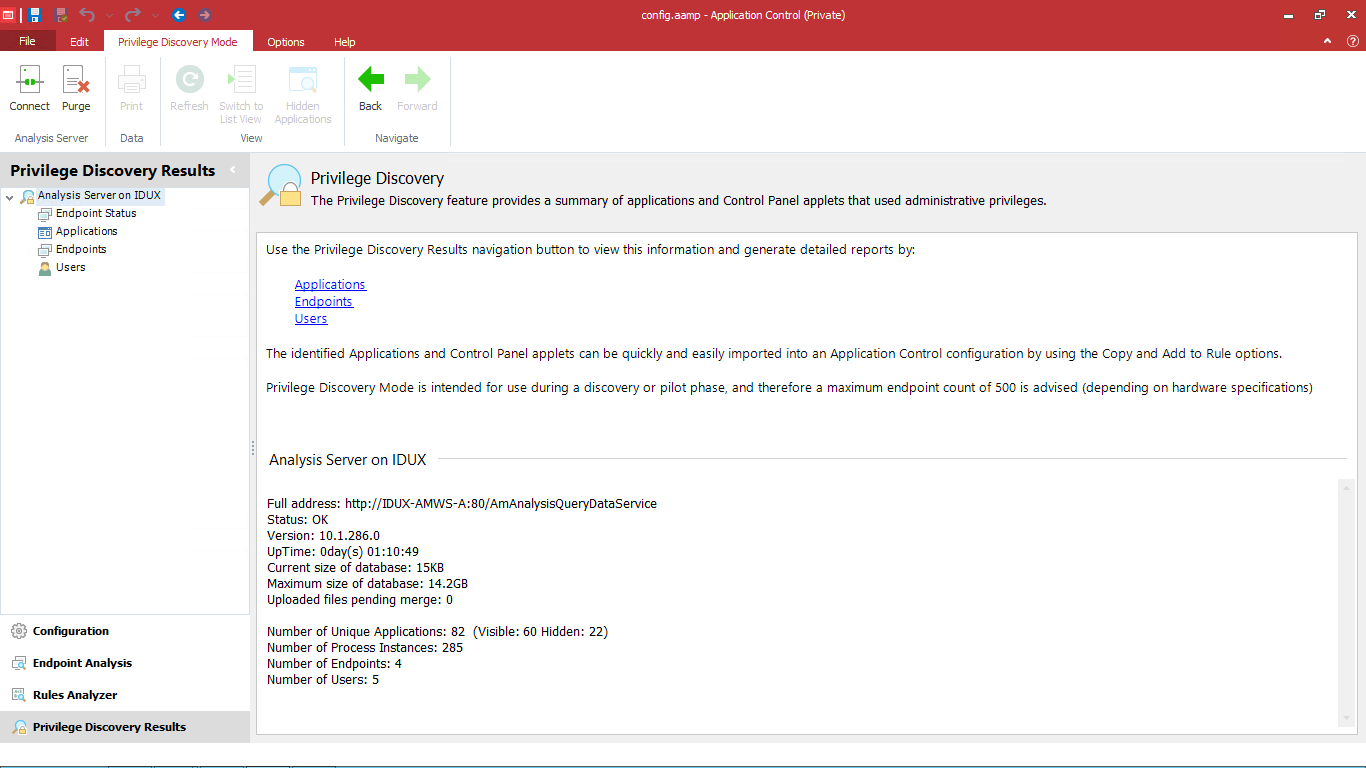
Privilege Discovery Results
In this section:
- About Privilege Discovery Results
- Add a User Rule from the User Results
- Add a User Rule from the Endpoint Results
- Add Discovered Applications to a User Rule
- Privilege Discovery Status
About Privilege Discovery Results
The results from the Privilege Discovery are viewed using the Privilege Discovery Results navigation button accessed from the Application Control console. The results are separated into the following nodes:
-
Applications - The Applications node opens the Application Summary work area and provides access to Application Details. The information in the Application Summary page can be viewed by application icon or as a list by clicking the Switch to List View button and provides details of applications that used administrative privileges to run.
Further information such as the endpoint on which the application was run, the name of the user, the command line that was used to execute the application and the time it was launched, can be accessed when you double-click on a specific application in the summary work area.
Application Details can also be used to create an Application Control configuration that can then be applied to user privileges for specific groups or users.
-
Endpoints - The Endpoints node opens the Endpoint Summary work area and provides access to Endpoint Details. The Endpoint Summary page displays the name of the endpoint, the number of unique applications run from the endpoint, the number of users with administrative privileges that used that endpoint and the how many times a particular application was run.
Further information such as user details, name of the applications used, the command line that was used to execute the application and the time applications on the endpoint were launched can be accessed when you double-click on a specific endpoint in the summary work area.
Endpoint details can also be used to create an Application Control configuration that can then be applied to user privileges for specific groups or users.
-
Users - The Users node opens the User Summary work area and provides access to User Details work area. The information in the Users Summary page consists of the username, the number of times unique applications were run, how many endpoints a particular user accessed and how many instances of an application were run.
Further information such as user details, the number of times a unique application was run with Administrative privileges, the endpoints used and the number of instances applications were run are displayed.
The User Details can also be used to create an Application Control configuration that can then be applied to user privileges for specific groups or users.
Each of the nodes can be used to create user rules for specific groups or users based on the results you have selected. They are then added to an Application Control configuration to be distributed to the endpoints on your network.
The server details are also accessed from the Privilege Discovery Results navigation tree. The details displayed allow you to keep a track of the endpoints being monitored together with details of when monitoring started and the predicted time of completion.
Add a User Rule from the User Results
When the Privilege Discovery monitoring period elapses, the results are collected on the Application Control Web Server and can be viewed using the Privilege Discovery Results navigation button. These results can be used to create rules that be included and distributed to endpoints on your network.
- Click the Privilege Discovery Results navigation button and select Users.
- Do one of the following:
- To view detailed information about the selected user, go to Step 3.
- To add an application or control panel applet used by a user straight to a rule, go to Step 5.
-
Double-click the selected user to display the information.
The User Details work area displays
- Expand and collapse the nodes as required, to access further information.
- Right-click on the application or control panel applet to be added to a user rule.
- Select Add to Rule and specify where the rule should be added.
- Do one of the following:
- Select as file name to add as a file name to the designated User Privileges node.
- Select as signature to add as a signature to the designated User Privileges node.
Select as full command line to add command line control to the designated User Privileges node.
You can check that the application or control panel applet has been added to the correct node by navigating to it in the Configuration navigation tree.
- Save the configuration.
Add a User Rule from the Endpoint Results
When the Privilege Discovery monitoring period is underway, you can add application items, specific endpoints or associated user components directly to an Application Control configuration and then distribute the configuration file to all the configured endpoints on your network.
It is recommended that, where possible, you wait for the Privilege Discovery period to elapse in order to create the configuration file.
- Click the Privilege Discovery Results button in the navigation pane and select Endpoints.
- Do one of the following:
- To view detailed information about the selected endpoint, go to Step 3.
- To add an application or control panel applet used by an endpoint straight to a rule, go to Step 5.
-
Double-click the selected endpoint to display the information.
The Endpoint Details work area displays
- Expand and collapse the nodes as required to access further information.
- Right-click on the application or control panel applet to be added to a user rule.
- Select Add to Rule and specify where the rule should be added.
- Do one of the following:
- Select as file name to add as a file name to the designated User Privileges node.
- Select as signature to add as a signature to the designated User Privileges node.
Select as full command line to add command line control to the designated User Privileges node.
You can check that the application or control panel applet has been added to the correct node by navigating to it in the Configuration navigation tree.
- Save the configuration.
Add Discovered Applications to a User Rule
When the privilege discovery monitoring period is underway, you can add application items, specific endpoints or associated user components directly to an Application Control configuration and then distribute the configuration file to all the endpoints on your network.
It is recommended that, where possible, you wait for the Privilege Discovery period to elapse before creating the configuration file.
- Click the Privilege Discovery Results Navigation button and select Applications.
- Do one of
the following:
- To view detailed information about the selected application, go to Step 3.
- To add the application or control panel applet straight to a rule, go to Step 5.
-
Double-click the selected application to display the information
The Application Details work area displays
- Expand and collapse the nodes as required, to access further information.
- Right-click on the application or control panel applet to be added to a user rule.
- Select Add to Rule and specify where the rule should be added.
- Do one of
the following:
- Select as file name to add as a file name to the designated User Privileges node.
- Select as signature to add as a signature to the designated User Privileges node.
Select as full command line to add command line control to the designated User Privileges node.
You can check that the application or control panel applet has been added to the correct node by navigating to it in the Configuration navigation tree.
- Save the configuration.
Add Known Applications to the Hidden Applications list
Once you have dealt with a discovered application, either by adding it to the configuration so that it will run elevated with administrative rights, or by deciding that end users should not be able to run the application with administrative rights, then you can hide the application from displaying in any of the report views. You do this by adding the known applications to an automatic exclusion list called “Hidden Applications”. When applications are added to this list they are automatically ignored in any future Privilege Discovery Reports and are no longer displayed as part of your results. To add applications to this list, highlight one or more of the applications, right-click and select Hide Application from the context menu.
The Hidden Applications list is accessed using the Hidden Applications button in the Privilege Discovery Mode ribbon and allows you to view and restore previously excluded applications using the Restore and Restore All buttons.
Privilege Discovery Status
The server details are displayed when you first select the Privilege Discovery Results navigation button. The details include the server information, current and maximum allowable database size, and details of the endpoint usage.
The Endpoint status node provides details of the endpoints currently being monitored with information such as the date and time of the last update together with the time the privilege discovery report is scheduled to finish.