Configure AWS CloudWatch Alarms for CSM
This mApp® Solution allows you to automatically create Incidents in CSM, based on CloudWatch Alarms. These Incidents are linked to existing AWS Configuration Item records.
Before you begin configuring your CloudWatch alarms, ensure that you have appropriate topics and subscriptions to which you can publish CloudWatch Alarm messages from AWS. Refer to Configure AWS SNS for CSM.
You can connect CloudWatch alarms so that when they go into alarm state, an Incident is created in CSM and tied to the appropriate AWS Configuration Item in your CMDB. Depending on your usage of AWS, you may already have configured AWS CloudWatch Alarms for your AWS resources. You can connect these existing alarms, or you can create new ones.
The overall workflow for the automatic creation of Incidents for your AWS Product configuration items is shown below:
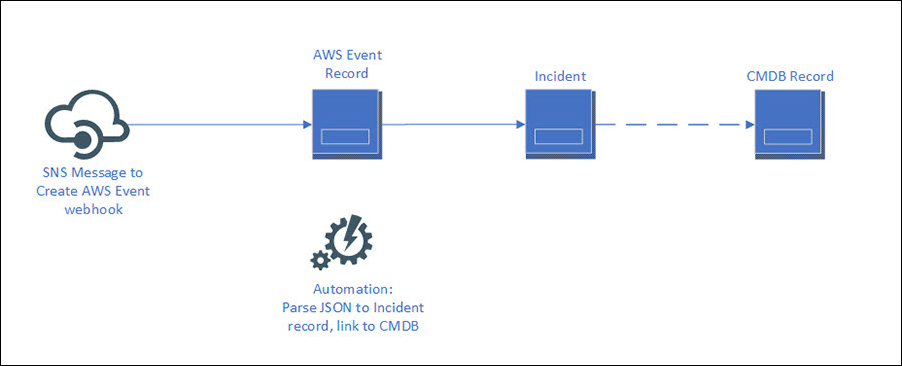
A webhook triggers the Create AWS Event One-Step Action. This webhook was designed as a sample to demonstrate how you might automatically create Incidents for your AWS resources when they go into alarm state or violate an established rule. This sample expects a CloudWatch Alarm notification from Amazon SNS, such as an EC2 instance which has exceeded its CPU utilization threshold, and stores the JSON from that alarm notification in an AWS Event object record. Then, an automation process (AWS Event) creates an Incident linked to the associated CI in your CMDB. You may wish to configure additional, similar event types using either AWS CloudWatch or AWS Config. To facilitate this process, we have included sample JSON for these event types, as well as configured the (None) Create AWS Event One-Step Action with a decision tree that covers two possible paths: a notification from AWS Config that a CloudWatch Alarm has changed from OK to ALARM state, and a CloudWatch alarm which sends the SNS notification directly with details about the affected resource. There is a sample of what kind of JSON is expected for the event. It's very particular, so we provide relevant sample code.
To configure AWS CloudWatch Alarms for CSM:
- In the AWS console, navigate to https://console.aws.amazon.com/cloudwatch/.
- Create a new alarm for use with this integration (see https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/US_AlarmAtThresholdEC2.html). You can modify existing alarms for use with this mApp Solution by simply adding a notification for these alarms to the 'cherwell-ci-create-incident' topic created in Configure AWS SNS for CSM .