Cherwell ISMS Workflow Diagrams
These workflows demonstrate the various features offered by the Cherwell ISMS mApp® Solution.
ISMS Audit
An audit is a scheduled review of compliance related to an industry standard, such as ISO 20071:2013 or key Configuration Items (infrastructure, supporting services, and/or collateral). Audits can be scheduled on a recurring basis and Actions such as Preventative and Corrective can be associated with audit activities.
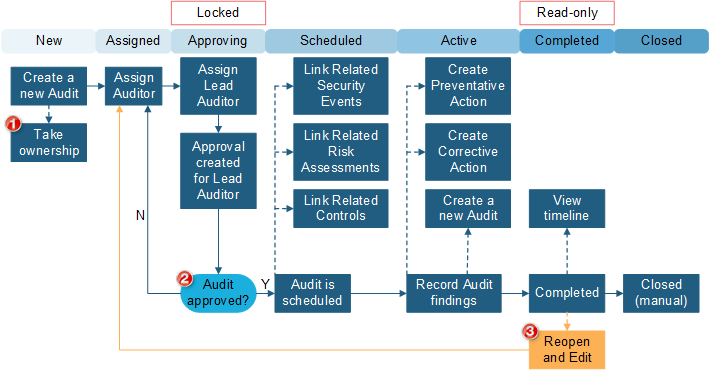
| 1 | Required fields include: Description, Operating Unit, Source, Type, Priority, Level of Effort. |
| 2 | When an Approval is Denied or Approved, the Approval Block ID is cleared. This removes the Approval tab so Approval History is not tracked. |
| 3 | This is an Enhancement Request and does not currently exist in the functionality. |
Security Event
Security Events are used to track and manage security-specific events using an independent process and lifecycle. Security Events provide the means for analysts to quickly analyze possible security threats and take necessary action. The following graphic shows a Security Event workflow.
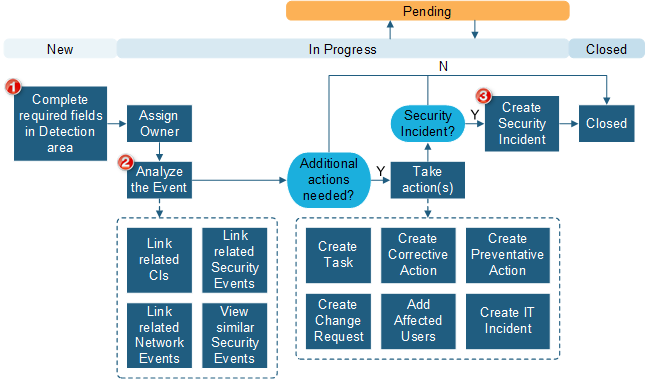
| 1 | These fields may be automatically completed by integration or when opened from Incidents or Network Events. |
| 2 | Complete the Analysis and Event Actions information ongoing throughout the analysis activities. |
| 3 | A Security Event can be closed or remain open independent of the state of the Security Incident. |
Security Incident
If a Security Event results in a breach or loss of any type, the event can be escalated to a Security Incident. ISMS Security Incidents are specific to security breaches, and differ from the CSM Incident Business Object. Security Incidents follow the NIST guidelines for Security Incident handling and allow strict privacy throughout the process to recovery. The following graphic shows a Security Incident workflow.
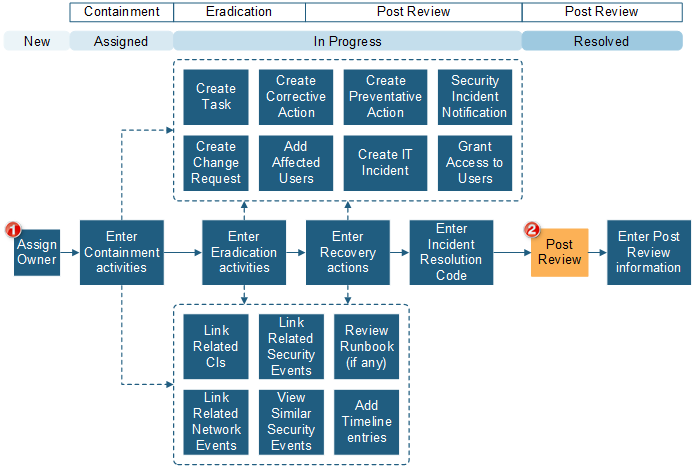
| 1 |
You must always open a Security Incident through a Security Event. The Security Incident Detection and Analysis fields are copied from the Security Event. The Containment, Eradication and Recovery areas of the Security Incident are all displayed on the Overview tab. To view the Post Review form, select the Post Review link under Stage. |
| 2 | Security Incidents can be Resolved without a completed Post Review. |
Policy
Policies are used to create policy documents and track related Controls. The following graphic shows a Policy workflow.
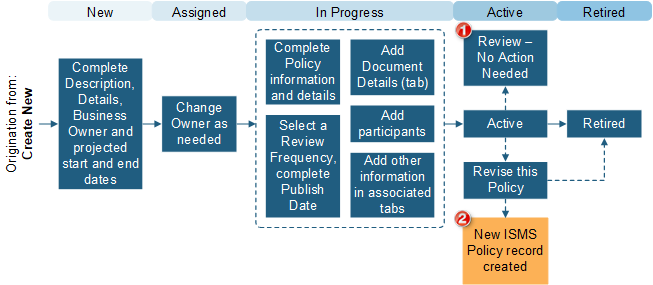
| 1 | Review Date field modified. |
| 2 | Current information is copied to the new record. |
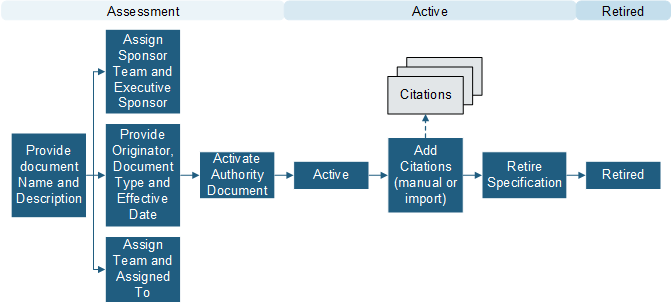
Authorization Document
Use an Authorization Document to define a set of Controls (individual requirements for specific areas of security) that align to industry standards, such as ISO 20071:2013. The following graphic shows an Authorization Document workflow.
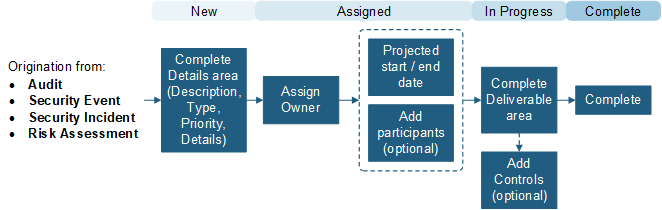
Compliance Corrective and Preventative Actions
A Compliance Corrective Action is used to record and track reactive actions taken to ensure compliance of a policy or Control. You can create a Corrective Action directly from a Security Event or audit. A Compliance Preventative Action is used to record and track proactive actions taken to ensure compliance of a policy or Control. You can create a Preventative Action directly from a Security Event or audit. The following graphic shows a Corrective/Preventative Action workflow:
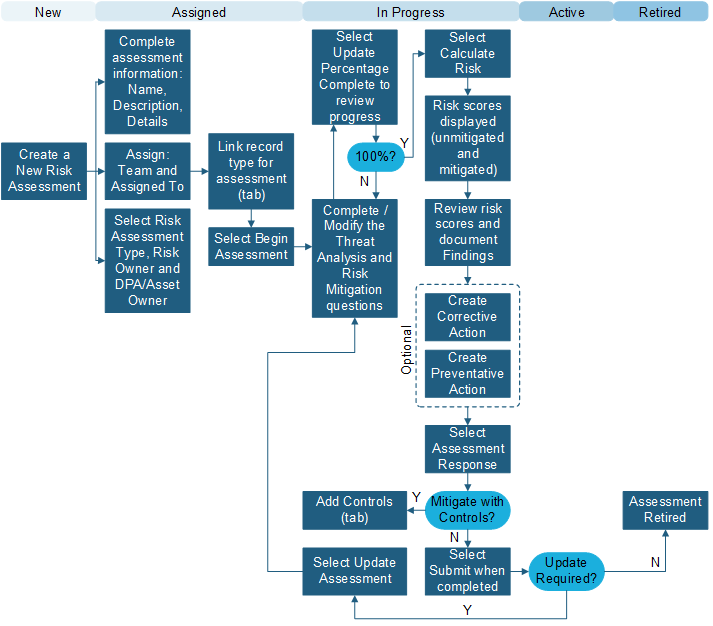
ISMS Risk Assessment
A Risk Assessment is completed by answering a set of questions that are weighted using a classification scale driven by Table Management. The following graphic shows a Risk Assessment record workflow: