AWS Key Encryption
This mApp® Solution uses AWS Access keys to make direct API calls to AWS. These keys are securely encrypted and used in the Generate Amazon Signature Action Block to generate a signature according to Amazon's sig4 signing process.
This topic covers the encryption process in this mApp Solution as well as some CSM encryption best practices. For details about how to authenticate with keys after applying this mApp Solution, see Configure AWS IAM for CSM and Add AWS Access Keys to CSM .
Encrypt Sensitive Data
To use this mApp Solution, your system is required to store private API keys in the database. You should rotate these keys as per AWS recommendation. For more details, see Best practices for managing AWS access keys.
There are three components needed for encryption with a modifier:
- Encryption Key: The Encryption Key is designed to be a global key unique to your CSM instance. When you apply the mApp Solution, this value will be blank. It will be set the first time you enter an encrypted value for your system, using the Set Encryption Key Action Block.
- Nonce: The nonce changes per encrypted value. A nonce is generated automatically for every record in the AWS Account table, where key values are stored.
- Value to be encrypted: In this case the secret key part of the AWS Access key
Secure Authentication to AWS
To facilitate authenticated AWS requests, there are two Action Blocks used by CSM to provide secure, encrypted authentication.
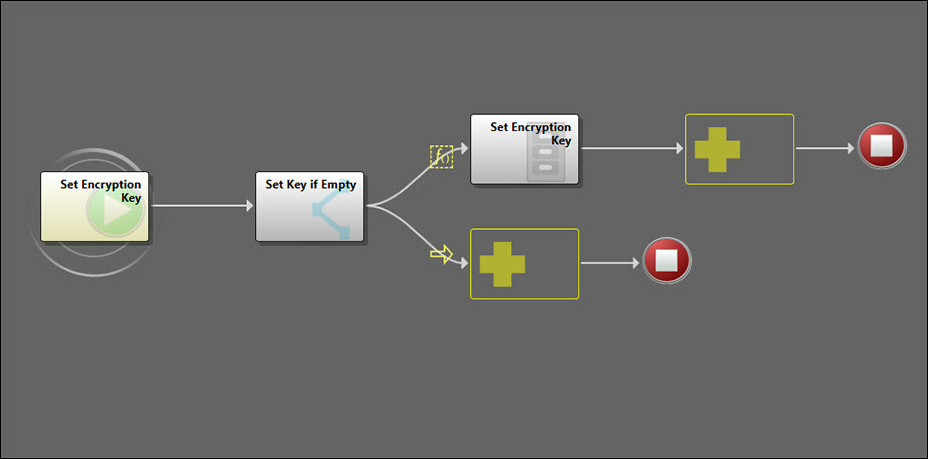
Set Encryption KeyThe Set Encryption Key Action Block is called by the Store Secret Key One-Step Action to set the Encryption Key stored value, if it is empty.
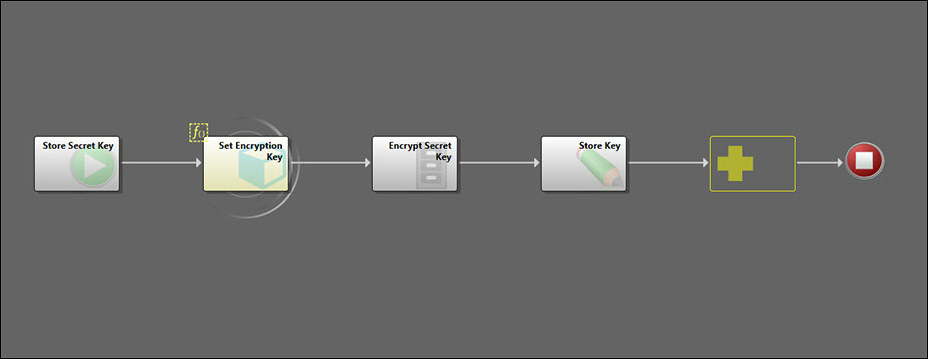
The Set Encryption Key Action Block then checks to see whether the encryption key is currently populated. If it is, the Action Block cancels, but does not stop running the rest of the Store Secret Key One-Step Action. Although there is no need to set the encryption key if the value exists for the system, we do want to continue storing the secret key.
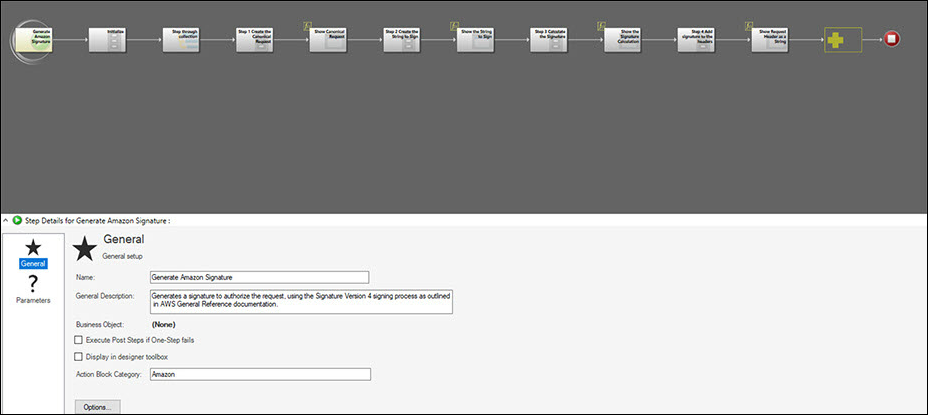
The Generate Amazon Signature Action Block follows the standard Signature Version 4 signing process from Amazon. See Signature 4. This Action Block is the only one stored in the Blueprint scope as it is delicate and should not be changed, unless the signing process itself changes. Its reusability means that each call doesn’t need to add in these authentication steps (which can be difficult to troubleshoot), only call the Action Block and pass it the correct parameters for the specific API call.
Example: In the SearchProductsAsAdmin call, the Get Products As Admin Action Block calls the Generate Amazon Signature Action Block in step 2. See Search Products as Admin.
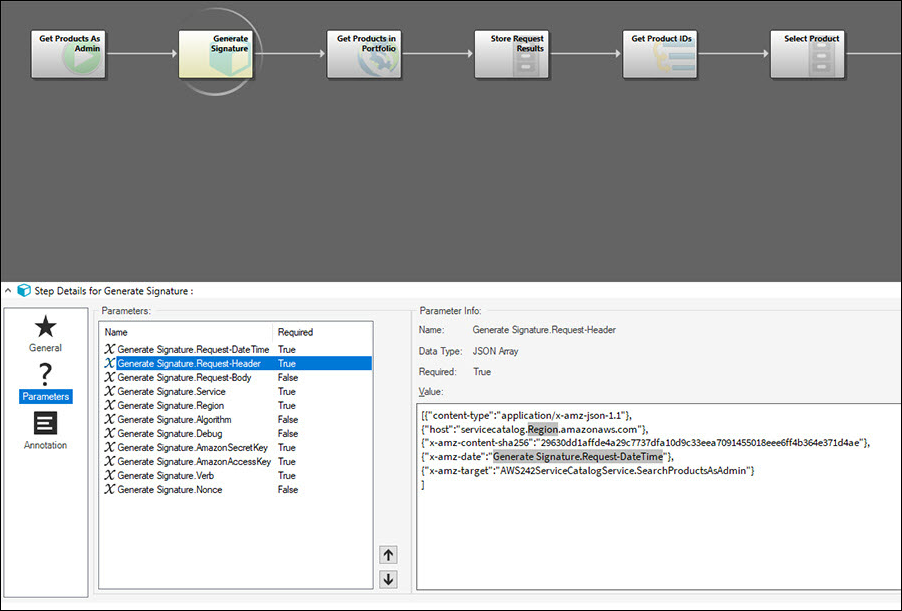
It then passes header information for the SearchProductAsAdmin call, which will be used by the Generate Amazon Signature Action Block to authenticate that specific call.
Decryption and Use of the AWS Secret Key
This mApp Solution implements the AWS Signature Version 4 (sig4) signing process within the Generate Amazon Signature Action Block. This block handles key decryption at the point where the key is used, to ensure that it is decrypted at the last possible moment. At no point is the secret key value stored or output to plain text.