Grant AWS Account Access to CSM Users
This mApp® Solution has been configured to expect AWS Access keys at the organizational level. You may have a single or multiple keys; however, you do not need a key for every CSM user who will need access to AWS products. Rather, this access is granted by linking departments in CSM to portfolios in AWS.
This topic covers the method by which this access has been granted. Use the approach as-is, or modify it to suit your organizational needs.
Design Requirements for AWS Account Access
When designing the AWS Account access for customers in this mApp Solution, there are three requirements:
- Customers should inherit their portfolio permissions from their department.
- Customers could have access to multiple portfolios within a single account, or even multiple accounts. Therefore, access should be granted via AWS portfolios, rather than directly to accounts. Granting access via portfolios provided flexibility to offer multi-account access, while still limiting said access only to the portfolios deemed appropriate within any accounts.
- Design should be as simple to edit as possible, while still meeting the first two requirements.
To meet these requirements, we implemented a multi-layered approach, outlined in detail below.
Inherit Portfolio Access from Departments
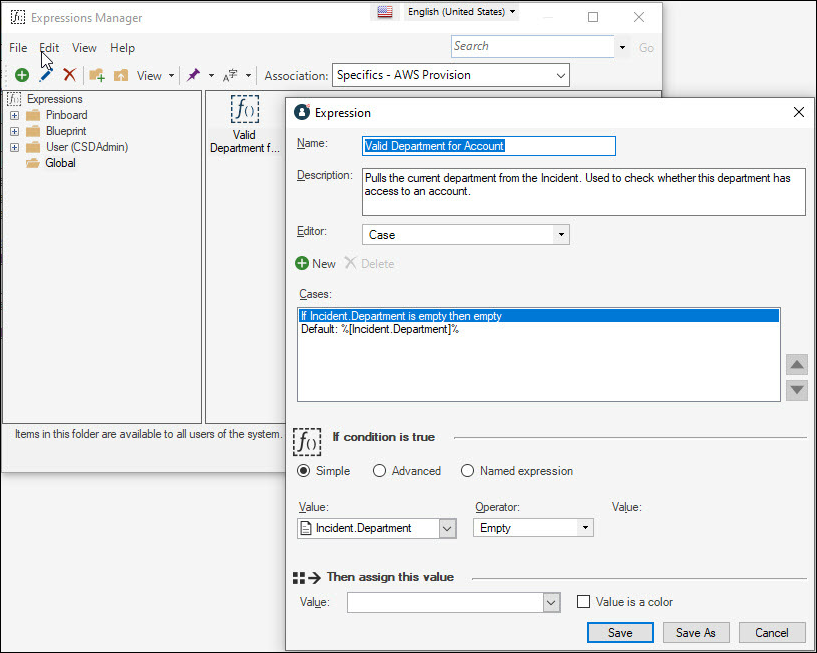
When a customer makes a request for an AWS product, their department
information has been auto-populated on the Service Request by default, in
Incident.Department.
CSM
then compares the department stored on the Service Request with a
comma-separated list of departments on the AWS Account table to check whether
the customer's department has access to this account.
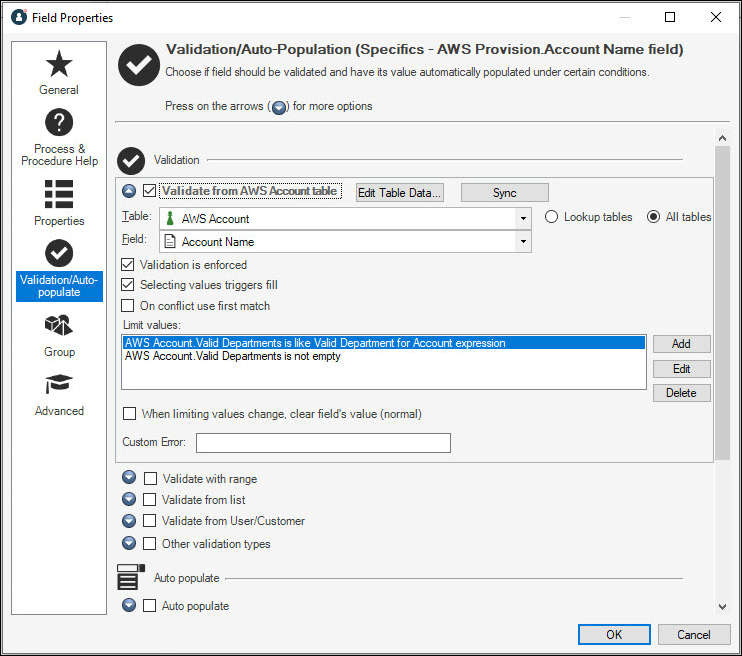
CSM limits the accounts in the drop-down menu on the Specifics - AWS Provision form to only those where it can confirm a department match.
Link Departments to AWS Account Records
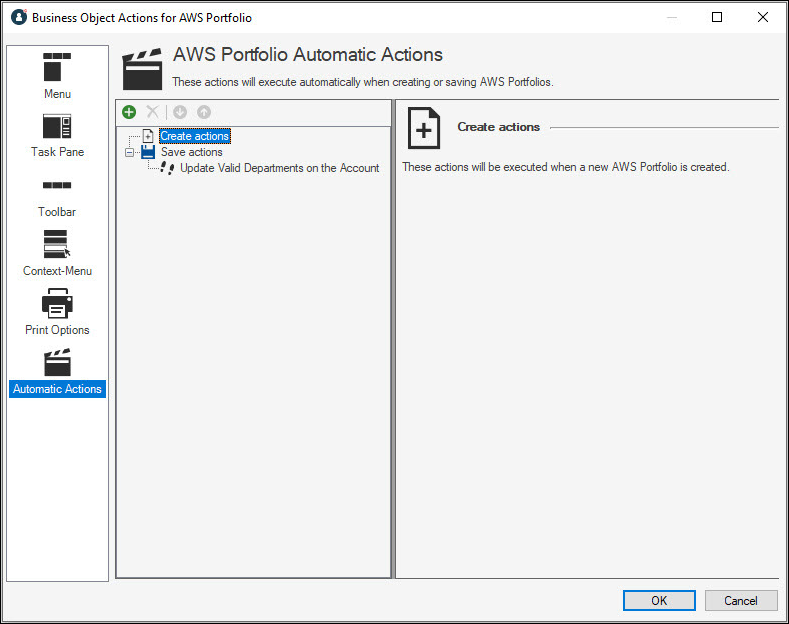
Because departments are linked only to portfolios, but portfolios can only exist in the context of an AWS account, we established some automated updating of the AWS Account table, using Automatic Actions on the AWS Portfolio Business Object. When an AWS Portfolio record is saved, any departments linked that portfolio will update on the related AWS account record as well.
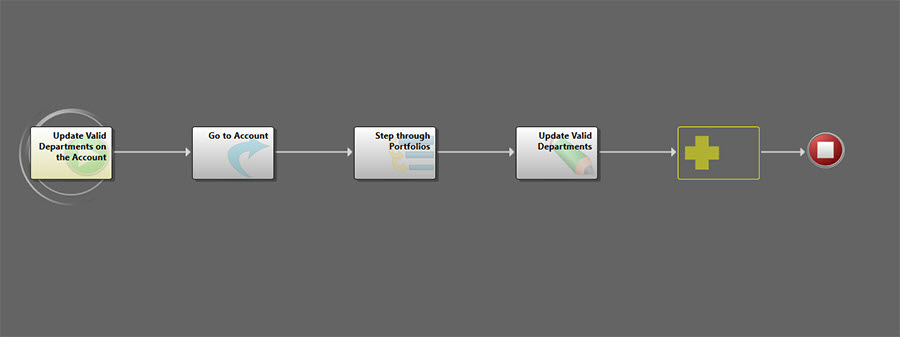
The Update Valid Departments on the Account One-Step™ Action happens on save of any portfolio record. It first navigates to the related AWS Account record, and then checks all portfolios tied to this AWS Account. From that check, it then builds a single list of valid departments and updates that list on the AWS Account record. By checking all related portfolios in addition to the one being saved, we can avoid duplication of departments in the valid departments list.
Change Portfolio Access
If you want to change portfolio access to another approach, you could modify the related expressions and One-Step™ Action to use different criteria.
You can also provide access to every CSM user via a personal AWS Access Key, and remove these account restrictions altogether. Consider your organization's security policies and needs for your implementation.