Ivanti Neurons for GRC Workflow Diagrams
These workflows demonstrate the various features offered by Ivanti Neurons for GRC.
GRC Audit
An Audit is a scheduled review of compliance related to an industry standard, such as ISO 20071:2013 or key Configuration Items (infrastructure, supporting services, and/or collateral). Audits can be scheduled on a recurring basis and Actions (example: Preventative and Corrective) can be associated with Audit activities.

| 1 | Required fields include: Name, Details, Source, Type, Priority, Level of Effort, and Lead Auditor. |
| 2 | When an Approval is Denied or Approved, the Approval Block ID is cleared. This removes the Approval tab so Approval History is not tracked. |
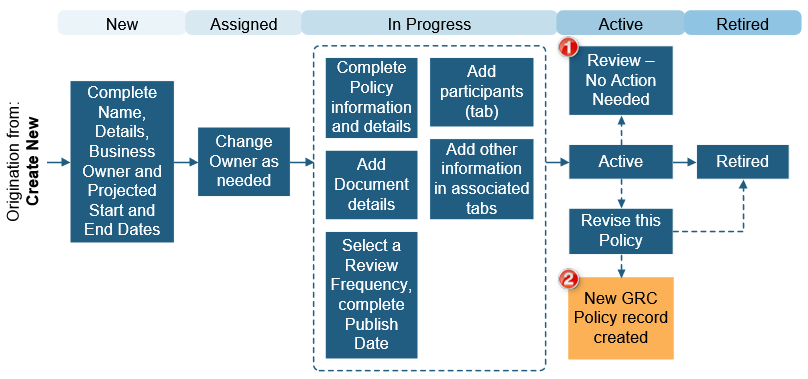
Policy
Policies are used to create policy documents and track related Controls. The following graphic shows a Policy workflow.
| 1 | Review Date field modified. |
| 2 | Current information is copied to the new record. |
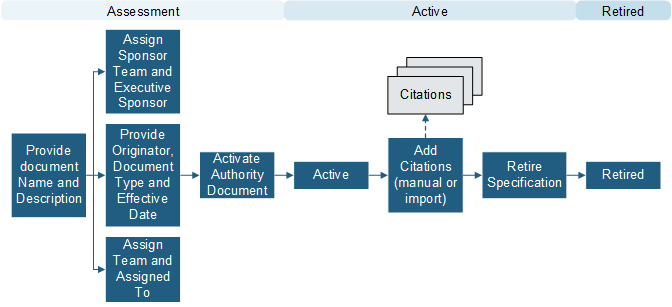
Authorization Document
Use an Authorization Document to define a set of Controls (individual requirements for specific areas of security) that align to industry standards, such as ISO 20071:2013. The following graphic shows an Authorization Document workflow.
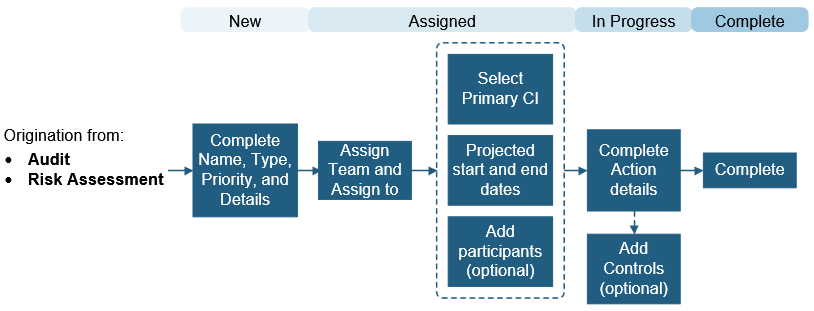
Compliance Corrective and Preventative Actions
A Compliance Corrective Action is used to record and track reactive actions taken to ensure compliance of a policy or Control. You can create a Corrective Action directly from an Audit. A Compliance Preventative Action is used to record and track proactive actions taken to ensure compliance of a policy or Control. You can create a Preventative Action directly from an Audit. The following graphic shows a Corrective/Preventative Action workflow.
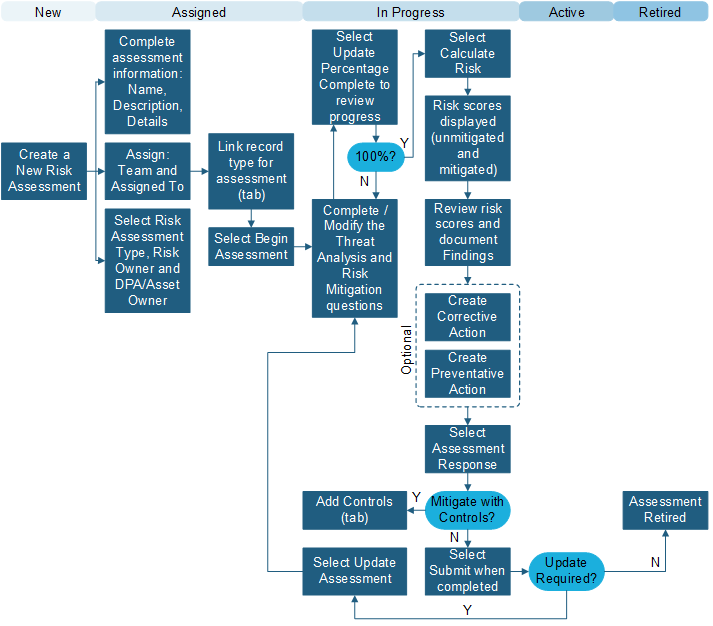
GRC Risk Assessment
Complete a Risk Assessment by answering a set of questions that are weighted using a classification scale driven by Table Management. The following graphic shows a Risk Assessment record workflow: