Discovery Troubleshooting
Agentless Engine
Agentless Remote Inventory
Agentless inventory information is gathered by copying some temporary files onto the remote device. This requires administrative credentials on the target for authentication.
Troubleshooting: Log onto the Agentless representative device and try to access the Admin share on the target via a UNC path:
Example: \\10.1.2.3\c$
If this connection prompts for authentication, attempt to authenticate with the same credentials that have been specified for the agentless engine.
SNMP
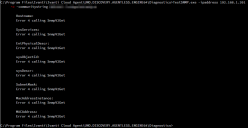
There is a standalone tool in the Diagnostics folder in the UNO.DISCOVERY.AGENTLESS.ENGINE64 folder that can be used to test that SNMP from the Agentless device is working. This allows adhoc queries to be run as follows:
- Launch an Admin Command prompt
- Cd to C:\Program Files\Ivanti\Ivanti Cloud Agent\UNO.DISCOVERY.AGENTLESS.ENGINE64\Diagnostics
- Use TestSNMP.exe with the -scanDevice -ipaddress and the -communitystring switches
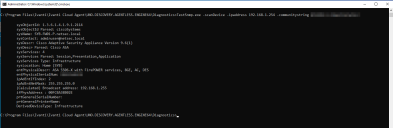
If these TestSNMP commands fails to return any SNMP data, then Error LIBSNMP_CLASS_TIMEOUT calling SnmpGet will be displayed:
For failing queries check the following:
- SNMP settings on the device
- IP address being used
- Community string being used
- Firewalls / Access Lists
- Routing
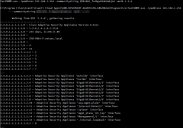
You can also 'walk' a device to return all Object Identifiers below a specific location in the hierarchy buy using the -walkDevice option instead of
-scanDevice. To limit the walk to a certain branch of the MIB hierarchy, specify a starting point for the walk. If you do not specify a starting point the entire tree will be walked.
SNMP V3 Example:
Discovery Engine
Name Resolution
Ivanti Neurons for Discovery uses both NetBIOS and DNS to try to resolve a discovered IP address to a name. NetBIOS needs to be enabled on the discovered device and also be contactable for the query to succeed. For DNS name resolution, only the IP address is known by the Discovery engine, so a reverse DNS lookup query is required for a ‘ptr’ record that matches the IP address. This query is not done directly against the discovered IP. Instead this is a query sent to a DNS server from the TCP/IP settings from the preferred adapter.
NetBIOS
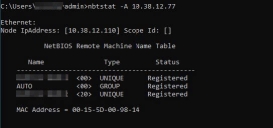
From the Discovery device, try to use a NetBIOS name query to resolve the IP address to hostname.
Example: nbtstat -A 10.38.12.77
If successful, this should display the NetBIOS name like in the example below:
Possible reasons for failure:
- NetBIOS not enabled: Check the WINS settings/DHCP settings for the adapter on the remote device.
- NetBIOS blocked by a firewall: Check the firewall on the remote device.
DNS
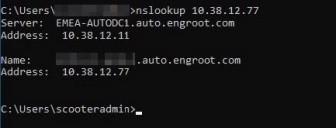
From the Discovery device, try to use a reverse DNS lookup query to resolve the IP address to fully qualified domain name.
Example: nslookup 10.38.12.77
If successful, this should display the fully qualified machine name like in the example below:
Possible reasons for failure:
- DNS server reverse lookup zone for the subnet was not created.
- No record exists for the device.
Operating System
The Operating System is detected using nmap O/S Fingerprinting technology. This relies on open TCP and UDP ports to be able to try to fingerprint the operating system. If there is a firewall that denies access to ports that are used, then the fingerprinting may not be successful.
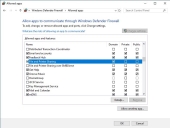
Example: A Windows 10 device is being fingerprinted as FreeBSD. This may be down to the device being locked down and nmap is unable to perform a guess on ports as these are blocked. Main cause is the local firewall profile not allowing access for File and Print sharing.
Allow access to File and Printer sharing for the required profile:
Control Panel > System and Security > Windows Defender Firewall > Allow an app or feature through Windows Defender Firewall: