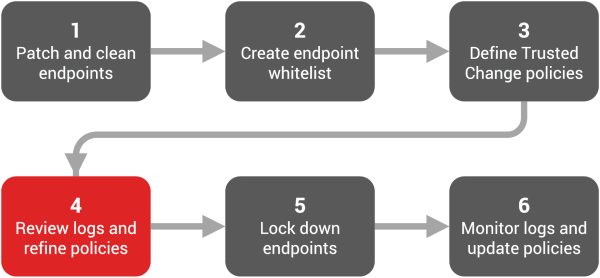
Phase 4: Review Logs and Refine Policies
After you have completed Easy Auditor scans on your test endpoints and developed initial policies, monitor the Application Event logs daily to identify any missing policies or policies that need to be updated.
In this phase you will:
-
Create scheduled Application Event log queries
-
Review Easy Auditor logs daily and create or adjust Trusted Change policies to accommodate changes
-
Manage re-appearing entries by authorizing files directly or re-running Easy Auditor to "reset" logs, if necessary
-
Review Memory Injection Detection events logs daily and add exceptions to the Memory Protection Policy, if required
-
Identify and eliminate potential Trust Leaks
-
Optionally, apply Local Authorization policy to users in Easy Auditor once the logs are stabilized
-
Maintain a test endpoint so that new software can be scanned and added to the Application Library
-
Increase the number of endpoints in Easy Auditor and adjust your policies to accommodate the new endpoints
-
Communicate with users to prepare them for lockdown and to ensure that they understand how to obtain approval for blocked applications. See Appendix 2 for sample end user communications.
The goal in this phase is to prepare endpoints for lockdown. Endpoints create log events when actions occur on the endpoint for which an Application Control policy does not yet exist. When log event entries appear in daily log queries, it means that there are policies you still need to create to manage the actions occurring on the endpoints. The endpoints are not ready for lockdown until you've created all the necessary policies.
This phase continues until the logs are stable with no unexpected entries. Recall that the stabilization period should:
-
Last for at least one month
-
Incorporate at least one Patch Tuesday
-
Incorporate at least significant corporate event, such as quarter-end
At the end of this phase you'll be ready to move your endpoints into lockdown.