Phase 5: Lock Down Endpoints
You are ready to move endpoints into lockdown after the following:
-
You've monitored the logs for the necessary period of time
-
You've created the Trust policies required in your environment
-
The logs have stabilized and you haven't seen any unexpected entries for at least one month
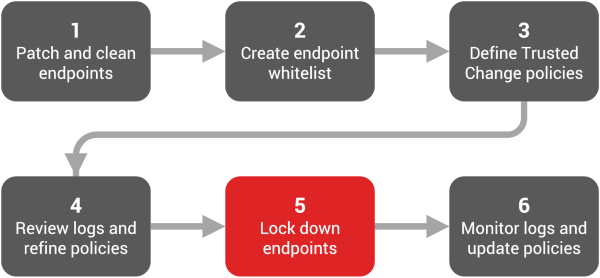
In this phase you will:
-
Communicate with users so that they understand the upcoming changes and how to get assistance. See Appendix 2 for sample end user communications.
-
Conduct a thorough antivirus scan prior to lockdown
-
Lock down endpoints by applying the Easy Lockdown policy
-
Authorize blocked applications when needed
-
Use Local Authorization wisely to provide flexibility
Once endpoints are locked down, the whitelist is enforced. Applications are blocked if they:
- Are not on the whitelist
- Are not allowed to execute by a Trusted Change policy
After lockdown, you can manage your Application Control deployment and authorize any blocked applications you want to allow in your environment.