Phase 6: Monitor Logs and Update Policies
Now that your endpoints are locked down, you can control which applications can execute in your environment.
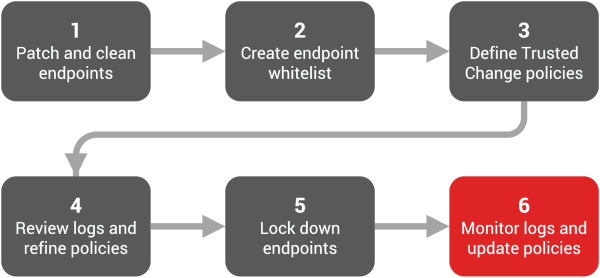
In this phase you will:
-
Continue to monitor logs and update Trusted Updater policies as needed
-
Organize files in the Application Library so that you can authorize them
-
Authorize applications centrally using a Supplemental Easy Lockdown/Auditor policy
-
Use Local Authorization to authorize applications in time-critical situations or to support disconnected users
-
Ensure you've implemented a process for users to request approval for new or blocked applications
-
Remove old Application Control events to maintain a smaller, faster database