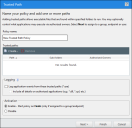
Trusted Path
Trusted Path authorizes applications to run based on their location instead of adding them to a whitelist. Trusted Path allows an application to execute if it is stored in one of the paths specified in the policy. We recommend you consider using Trusted Path for:
-
Unsigned executables that change frequently, where every installation of the application is unique
-
Shared Network Paths, such as build output locations for in-house software development
Create a Trusted Path Policy
-
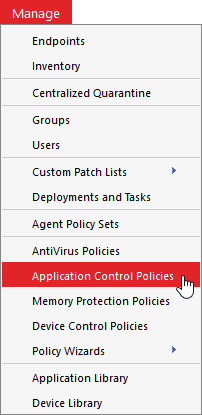
From the Endpoint Security Console, select Manage > Application Control Policies.
-
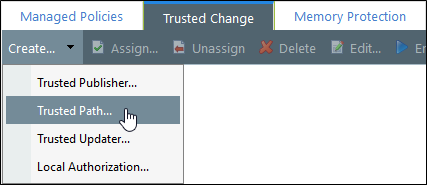
Click the Trusted Change tab.
-
Select Create > Trusted Path to open the Trusted Path wizard.
-
Progress through the wizard. See Creating a Trusted Updater Policy in the Application Control Help for detailed steps.
Set Ownership Restrictions
While allowing applications to execute based on their location may not seem like a particularly secure solution, you can set ownership restrictions by specifying an Authorized Owner. This restriction allows a file to execute in the Trusted Path only if the owner matches the Authorized Owner that you specified in the Trusted Path policy.
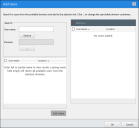
You can add one or more Authorized Owners while you're in the Trusted Path wizard, using the Add Users dialog.
-
In the Trusted Path wizard, click on the Authorized Owners ellipses (...) button next to the Trusted Path you created.
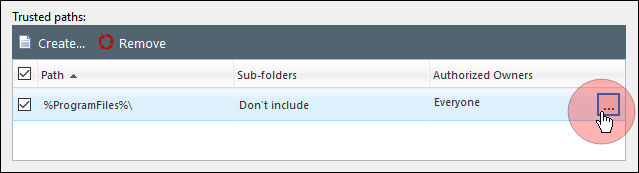
The Add Users dialog opens.
-
Search for users that you want to set as Authorized Owners and add them to the selection list. See Adding an Authorized Owner to a Trusted Path in the Application Control Help for details.