Trusted Updater
Trusted Updater allows you to install and automatically authorize software patches or new applications without additional overhead. By assigning trust to particular executables, any files added to the endpoint by those executables are automatically added to the whitelist for that endpoint. You should use Trusted Updater where possible to manage change in your applications.
Trusted Updater is the only trust mechanism that updates the endpoint whitelist directly. You should not use other trust mechanisms to install or update applications, as it can result in stability issues if the installations or updates change the driver files used in the boot sequence.
Sections in this topic:
- Where to Use Trusted Updater Policies
- Identify Updater Files
- Create a Trusted Updater Policy
- Add a Trusted Updater Directly from Logs
- Understand and Manage Updater Behavior
Where to Use Trusted Updater Policies
We recommend that you set up Trusted Updater policies for the following software categories:
-
Software distribution tools or patch and remediation tools, including:
-
Windows Update
-
Ivanti Ivanti Patch and Remediation
-
Novell Zenworks
-
HP Radia
-
Microsoft System Center Configuration Manager (SCCM)
-
Altiris
-
Tivoli
-
Shavlik
-
-
Third-party antivirus solutions, including:
-
Sophos
-
McAfee
-
Symantec
-
Kaspersky
-
Trend Micro
-
-
Self-updating applications such as:
-
Adobe
-
Apple iTunes
-
Java
-
Mozilla Firefox
-
The following sections provide best practices for defining Trusted Updater policies for each of the above software categories.
Windows Update
Windows update is enabled on endpoints by default. However, to prevent instability issues on endpoints, Application Control blocks Windows Update from executing unless you add Windows Update as a Trusted Updater. If you're using Windows Update to update endpoints, create a Windows Update Trusted Updater policy before you put endpoints into lockdown.
For your convenience, we have created a Windows Update policy kit that contains a list of all the hashes of the updater files for Windows Update. Given the number of different updater files and versions, this kit greatly simplifies the task of creating a Windows Update Trusted Updater policy yourself. To import this policy kit to your Endpoint Security Server, please contact Support.
Software Distribution Tools or Patch and Remediation Tools
Ivanti Ivanti Patch and Remediation is a Trusted Updater by default, so no configuration on your part is required. If you are using other software distribution or patch and remediation tools, you should add the application executable to the Trusted Updater policy. You should also add any updater files for the application to the policy.
Third-party Antivirus Solutions
Antivirus solutions are updated every day with new signature files and occasionally with new engine files. To accommodate these changes, you need to create a Trusted Updater policy. However, you must add only the antivirus updater and not the antivirus scan engine to the policy. If you add the the scan engine to the Trusted Updater policy, every file that the scan engine accesses (i.e., every file that the user accesses) will inherit the trust settings. This has the same effect as turning off Application Control on the endpoint altogether.
Bottom line: Trust the antivirus updater only, not the scan engine.
Web Browsers
You should not add entire browser files (e.g., iexplore.exe, firefox.exe, etc.) to the Trusted Updater policy, as this has the same effect as trusting the entire Internet! Instead, you should add the browser updater to the Trusted Updater policy to support browser updates. You could add Firefox's updater updater.exe, for example.
Self-Updating Applications
Software applications are updated over time to address bugs, security issues and to add new features. Each application typically has one or more updater files it uses to perform updates. These updater files will execute because you'll have already added them to the whitelist during the Easy Auditor scan.
However, the new files that the updater adds to the endpoint will not execute as they are not on the whitelist. For each of these updaters, decide whether to:
-
Explicitly deny the updater in the environment
-
Add the updater as a Trusted Updater
Identify Updater Files
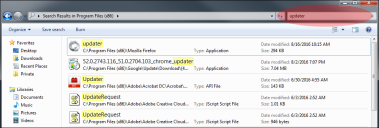
A common challenge when creating a Trusted Updater policy for applications is identifying and locating the updater files. Use one or more of the following methods to help you identify updater files:
-
Search for "update" or "updater" in C:\Program Files (x86). On 32-bit versions of Microsoft Windows, the folder is C:\Program Files.
Applications that update themselves have specific executables that perform the updates. The executable often has the word "update" in its name or in the name of the folder containing the executable. -
Refer to the vendor's documentation.
Application vendors often provide information on the update mechanisms for their applications. -
Use the logs.
Create a daily Application Event log query for Easy Auditor: Applications Blocked When Enforcement is Enabled. This query highlights any executables that would have been blocked if the endpoint had been in lockdown. The parent processes for these executables may be updaters. However, the parent process in the logs is the immediate preceding process and may not always be the actual updater process.
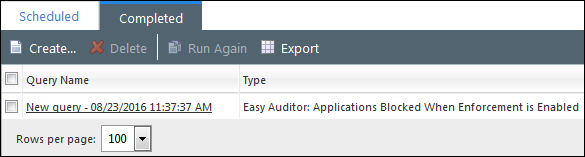
To Create the Applications Blocked When Enforcement is Enabled Query
-
From the Endpoint Security Console, select Review > Application Control Log Queries.
-
On the Application Control Log Queries page, click Create.
The Application Control Log Query wizard opens.
-
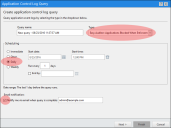
Complete the following in the wizard:
-
Type a name for the new query in the Query Name field.
-
Under Type, select Easy Auditor: Applications Blocked When Enforcement is Enabled.
-
Under Scheduling, select Daily. Define a Start date and Start time.
-
Select whether to have an email sent to you when the query is complete.
We recommend you receive email notifications. These act as a daily reminder to review the logs and update the policies as needed. Make sure that you have already defined your email server within Endpoint Security. See Configuring Alert Settings in the Endpoint Security Help.
-
-
Click Next and add endpoints or groups of endpoints to the query.
-
Click Finish to create the query. After the query runs, view its summary and results on the Completed tab.
If you have trouble determining the updater for an application, contact Support for help.
Create a Trusted Updater Policy
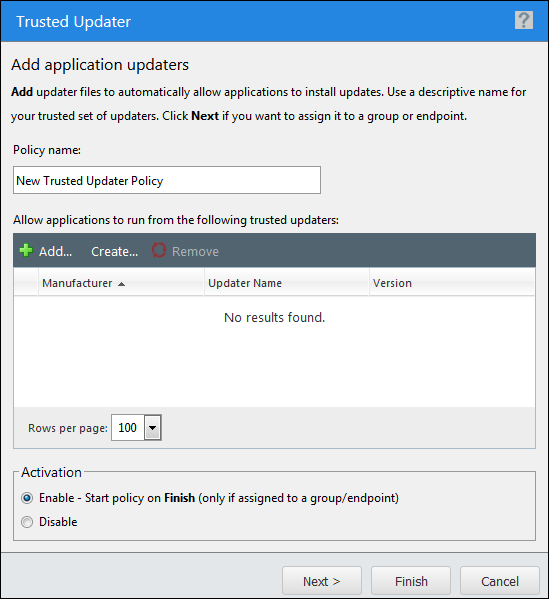
You've identified the updater files across your endpoints. Now use the Trusted Updater wizard to create a new Trusted Updater policy and add the updater files to it.
For the Trusted Policy to be effective, add all updater versions to the policy.
-
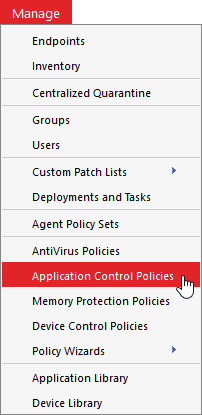
From the Endpoint Security Console, select Manage > Application Control Policies.
-
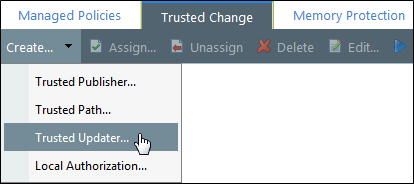
Click the Trusted Change tab.
-
Select Create > Trusted Updater to open the Trusted Updater wizard.
-
Complete the wizard. See Creating a Trusted Updater Policy in the Application Control Help for detailed steps.
Add a Trusted Updater Directly from Logs
In addition to using the Trusted Updater wizard, you can add Trusted Updaters directly from the log queries. If an application updater file appears in the EasyAuditor: Applications Blocked When Enforcement is Enabled log query, you can either add the updater to an existing Trusted Updater policy or create a new policy.
-
From the Endpoint Security Console, select Review > Application Control Log Queries.

-
On the Completed tab, open the Easy Auditor: Applications Blocked When Enforcement is Enabled query that you previously created.

-
[Optional] There may have been activity on your endpoints since you initially created the query. To refresh the query and capture any new log entries, click Refresh.
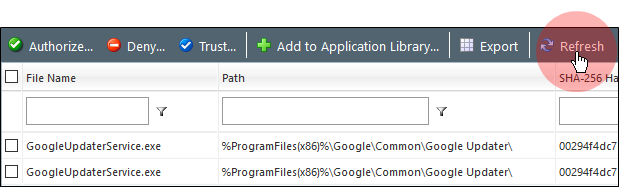
-
Select the updater file you want to add as a Trusted Updater and click Trust.
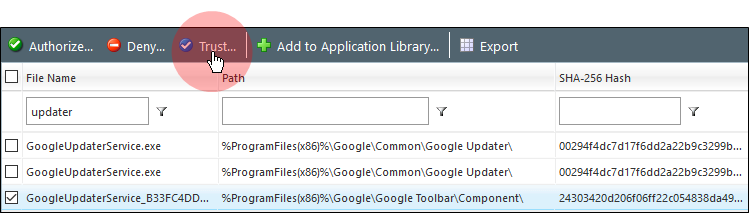
The Trust Selected Files dialog appears.
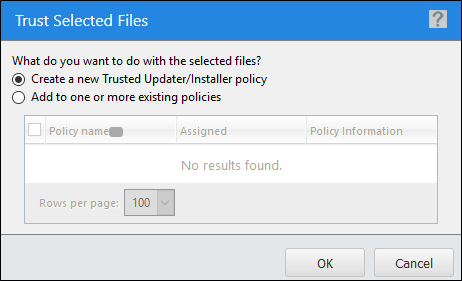
-
Select whether to create a new Trusted Updater policy or add the file to an existing policy.
Understand and Manage Updater Behavior
Common Updater Behavior
Applications receive updates differently; there is no standard update mechanism across all applications. The most common update method uses updater files, which you should add to the Trusted Updater policy. However, over time vendors may change the method they use to update applications. If this happens, the updated version of the application may be blocked. Resolve this by:
-
Identifying the new updater and adding it to the Trusted Updater policy
-
Authorizing the new version of the application for any affected users
Unsecured Updaters
Some updating mechanisms are inherently insecure from an application control perspective. For example, sometimes the application itself, such as a web browser, detects that a new version of the application is available and downloads the installer automatically. In this scenario:
-
There are no specific updater files to add to the Trusted Updater Policy. Adding the primary application executable instead would be very insecure (recall from earlier in this section that you should not trust browser executables).
-
The installer uninstalls the old version of the application and installs the new version.
-
The new version is not on the endpoint whitelist and therefore does not execute.
How do you manage this scenario? Add the new version of the installer to the Trusted Updater policy. Then you can reinstall the new application version on any affected endpoints.
Installers as Trusted Updaters
When an installer is a Trusted Updater, any file installed on the endpoint by that installer is automatically whitelisted. If you plan to refer users to a repository of approved software, scan the repostory location and add all of its application installers to a Trusted Updater Policy. Users can then download the installers and install the approved software on their endpoints as needed.
Best Practice Recommendations
-
Take time to understand updater behavior while endpoints are in Easy Auditor.
-
If you can't create a Trusted Updater policy for an application, consider an alternate trust mechanism such as Trusted Publisher.
-
Alternatively, disable automatic updates for the application and use a test endpoint in automatic update mode to obtain the new updater or installer. Then add the new updater or installer to the Trusted Updater policy and roll out the updated version.