Encryption Scenarios
When adding encryption permissions to Device Control policies, most organizations typically divide their users into three different categories:
- Users not approved to encrypt devices
This category is the simplest group to address. When configuring your Device Control policies for these users, leave the Encrypt and Decrypt permission options unchecked, as depicted in the following image.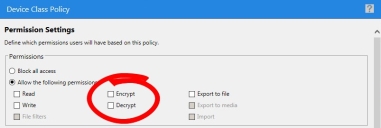
- Users permitted to encrypt devices
This group is assigned permissions to encrypt devices, but the users assigned the policy are not forced to encryption; they have the option to encrypt. - Users required to encrypt devices
In this case, you configure two policies: One policy for unencrypted devices, and another for encrypted devices. For more information on how to configure each policy, see How to enforce encryption for removable storage devices.
Users in this encryption category can still access encrypted devices, depending on the options you select when creating a policy.
Accessing Encrypted Devices
You have two options for managing how users can access encrypted devices.
- Password based access:
A password is chosen by the end user when the device is encrypted. The encryption key is placed on the device outside of the encryption container, and is itself encrypted with the password. To allow users to encrypt a device that is accessible with a password, they need the Encrypt and Export to media permissions in a policy that applies to them.
- Certificate based access:
If you have a Microsoft Certificate Authority (CA) in your organization, and you provide certificates to users that are valid for encryption, there is a second option for device access. Users can choose Windows Users who are allowed access to the device after encryption. They can add a number of users from AD, all of which will have access to the device when on a device- controlled endpoint. When the device is connected to an endpoint, Device Control compares the logged in user's encryption certificate to those added to the device. If the user is listed on the device, the device will be unlocked using the certificate. No password is required. The device cannot be unlocked in this manner on un-managed machines, or machines outside of your organization since the certificate is needed. To provide this capability, you must have a Microsoft CA in your environment, and you must set the Microsoft CA key provider option on the Tools > Options to Enabled (Decentralized).