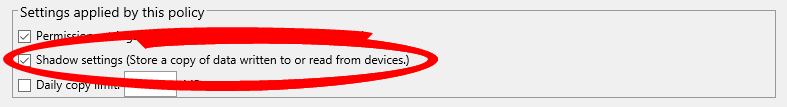
File Shadowing
File Shadowing is a Device Control feature that creates a copy of any file that a user interacts with on a device. This interaction includes reading a file on a device, saving a file to a device, or saving a file from a device. This copied file is then uploaded to the Endpoint Security Server.
You can enable File Shadowing while creating:
- Device class policies
- Device collection policies
- Port control policies
After creating a policy that shadows files, you can view those files by creating a Device Event Log Query.
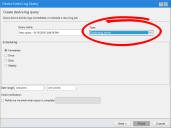
To Create A File Shadow Device Event Log Query:
- From the Navigation Menu, select Review > Device Event Log Queries.
- Click Create.
The Device Event Log Query wizard opens. - Complete the wizard. While completing the wizard, select Shadowing events from the Type drop-down. Click Finish when you're done.
To View A File Shadow Device Event Log Query
- From the Navigation Menu, select Review > Device Event Log Queries. Make sure the Completed tab is selected.
- Click the Device Event Log Query containing Shadowing events.
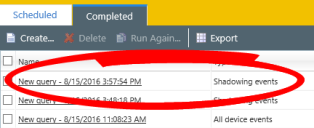
The Shadow files are displayed with the following metadata:
- The names of files transferred to and from devices (depending on how your policy is configured
- User name
- Endpoint name
- Time of the transfer
If you enabled Full File Shadowing, you can view the file itself. Expand the row for an event and click the ![]() icon. You have three options for viewing the file:
icon. You have three options for viewing the file:
- View using Hex Viewer
This option is the safest, but least informative (depending on the file). The file content displays in hexadecimal format, alongside an ASCII representation of the data. This option is safest because the file is not sent to your browser. It remains in the shadow storage location and is not executed. - Download the file to your computer through your browser
This option lets you choose the best option for examining the file. - Open the file in the browser using the browser's default action for that file type
This option is the fastest way of viewing the file, but introduces risk as the file may contain malware or have other unexpected content.