Creating Antivirus Policies
Ivanti AntiVirus provides two wizards for creating antivirus policies, the Recurring Virus and Malware Scan Wizard and the Real-time Monitoring Policy Wizard.
You can launch either of these wizards using the Create control on the following pages:
- The Antivirus Policies page.
- The Antivirus Policies tab of an endpoint's Details page.
- The Antivirus Policies view of a group's page.
The process of using each wizard follows a general pattern:
- Name the policy
- Configure basic scanning options
- Configure additional scanning options
- Configure exclusions or inclusions
- Assign to endpoints or groups
Only the first two steps are required to create a basic antivirus policy. After it has been created you can edit the policy to configure additional options and exclusions/inclusions, and assign it to endpoints or groups.
Creating a Recurring Virus and Malware Scan Policy
The Recurring Virus and Malware Scan Policy Wizard enables you to schedule a recurring scan, set scanning options, and build a list of target endpoints.
A recurring scan runs on a regular, scheduled basis. It typically scans all the files on an endpoint (apart from those that are specifically excluded from the scan). A recurring scan can take an appreciable amount of time to run if there are a large number of files to be scanned.
- Select Manage > Antivirus Policies.
The Antivirus Policies page opens. - From the Manage > AntiVirus Policies toolbar, select Create > Recurring Virus and Malware Scan.
The Recurring Virus and Malware Scan Policy Wizard opens at the Name and Schedule Policy page.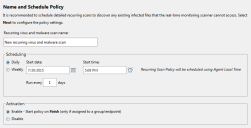
- Type a new name in the Recurring virus and malware scan name field. Make the name descriptive, conveying the role of this recurring policy.
- Select and configure a Scheduling option:
- Select the Daily option.
- Type the start date in the Start date field. You can also select the start date by clicking the Calender icon.
- Type the start time in the Start time field using a hh:mm format followed by AM or PM. This field supports both 12- and 24-hour time. Alternatively, you can select the start time by clicking the Clock icon.
-
Type a value in the Run every x days field.
- Select the Weekly option.
- Type the start date in the Start date field. You can also select the start date by clicking the Calender icon.
- Type the start time in the Start time field using a hh:mm format followed by AM or PM. This field supports both 12- and 24-hour time. Alternatively, you can select the start time by clicking the Clock icon.
- Type a value in the Run every x weeks on: field.
-
Select one or more of the daily check boxes to run the scan on those days.
- Select an Activation option.
- Click Next to set the scanning options.
The Scan Options page opens.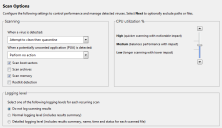
- From the drop-down list, select the action that occurs when a virus is detected.
- To clean an infected file means to completely remove the malicious code so that the file is safe to use. It is not always possible to remove the malicious code, however. When this happens, you can either delete the file or quarantine it. To quarantine means to move it to a safe place on the endpoint where it can be kept for further examination.
In certain cases (such as when the malware is a Trojan) the entire file is malicious. Such a file cannot be cleaned, so the only options are to quarantine or delete it. - Virus detection actions are not used for memory scans.
- From the drop-down list, select the action to be taken when a potentially unwanted application (PUA) is detected:
- Set the Scanning options:
- Perform no action - the boot sector is left as it is and an alert is sent to the Virus and Malware Event Alerts page.
- Clean/Delete/Quarantine - the boot sector is automatically repaired.
- Scanning archives will result in longer scan durations.
- Infected .rar files can be quarantined and deleted, but can't be cleaned.
- Set the CPU utilization % threshold to control the level of impact the scan is to have on endpoint performance:
- Set the logging options:
- Click Next.
- You have some applications whose manufacturers recommend be excluded from virus scans.
- You have folders containing large amounts of data that you consider relatively safe, such as graphics files. Excluding them from the scan saves time.
- You have files that cause known "false positives" during a scan.
- Exclude files and folders, using one of the following methods:
- Click Add.
A blank entry is added to the exclusions list. - Select an exclusion type from the Type field.
The types are File and Folder. - Enter the path to the item you want to exclude in the Path field.
- Click
 to add the exclusion to the list.
to add the exclusion to the list.
Repeat this procedure for all files and folders you want to exclude from the scan. - Configure the Optional drives settings:
- Click Next.
- Build a list of targets (endpoints), using either or both of the following methods:
Important: Recurring scans will not run on an endpoint that is shutdown or hibernating at the scheduled scan time.
Method
Steps
To define targets using groups:
- If the Groups section is not open, click its up arrow to open it.
- Select one or more endpoint groups by selecting their check boxes.
- Click Add.
This adds the group(s) to the Assigned list.
To define targets using endpoints:
- If the Endpoints section is not open, click its up arrow to open it.
- In the search field, do one of the following:
- Type an endpoint name (to search for a specific endpoint)
- Type part of an endpoint name (to search for similarly named endpoints)
- Leave it blank (to search for all available endpoints)
- Click the Search icon.
Depending on what you typed, one or more endpoints will appear in the Name column, with their respective IP addresses. - Select the check box for each endpoint you want to assign.
- Click Add.
This adds the endpoint(s) to the Assigned list.
You can remove targets from the Assigned list by selecting the applicable check boxes and clicking Remove.
- Click Finish.
The Virus and Malware Scan Policy Wizard closes. The newly created policy is displayed in the Antivirus Policies page.
The name must be unique, otherwise a warning will be displayed.
Important: If an endpoint's internal clock changes (for example, due to Daylight Savings Time or time-zone differences while traveling) a recurring scan scheduled to take place during the time skipped will not occur.
Ensure you or the endpoint user run a Scan Now immediately after a time change to maintain continuous protection.
|
Method |
Steps |
|---|---|
|
Daily |
|
|
Weekly |
Leave the value at 1 if you want the scan to run at least once a week. |
|
Setting |
Result |
|---|---|
|
Enable - Start policy on Finish (only if assigned to a group/endpoint) |
The policy is created and activated when you click Finish and the wizard closes. The policy must be assigned to at least one endpoint or group. |
|
Disable |
The policy is created but not activated when you click Finish and the wizard closes. You may activate it at a later time. |
If you click Finish at this point, a basic policy is created, but is not assigned to any endpoints. You can configure the policy further and assign it to endpoints later.
|
Setting |
Result |
|---|---|
|
Perform no action |
Does nothing with the infected file, but sends an alert to the server. |
|
Attempt to clean then quarantine
|
Attempts to clean the infected file. If this is not possible, the file is quarantined. An alert is sent to the server. |
|
Attempt to clean then delete |
Attempts to clean the infected file. If this is not possible, the file is deleted. An alert is sent to the server. |
|
Attempt to clean then quarantine then delete |
Attempts to clean the infected file. If this is not possible, the file is quarantined. If it is not possible to quarantine it, it is deleted. An alert is sent to the server. |
Note:
|
Setting |
Result |
|---|---|
|
Perform no action
|
The system ignores the potentially unwanted application. |
|
Send alert only |
An alert is sent to the server only. |
|
Alert and action (treat as malware) |
An alert is sent to the server and the file is cleaned, quarantined, or deleted, according to the action you selected in the When a virus is detected drop down. |
|
Setting |
Result |
|---|---|
|
Scan boot sectors |
The virus scan will be more thorough if you scan boot sectors in addition to program and data files. If malware is detected in a boot sector, the action taken depends on the virus detection option selected: |
|
Scan archives |
The virus scan will be more thorough if you scan archive files such as .zip and .cab files.
|
|
Scan memory |
Viruses and other malware can reside in memory as well as on the disk(s). The virus scan will be more thorough if you scan memory for such viruses and malware. Virus detection actions and exclusions are not applied to memory scans. |
|
Rootkit detection |
A rootkit, similar to a hack tool, enables attackers to gain administrator access to a system. They hide the attacker's presence and give them full control of a server or client endpoint without being noticed. |
|
Setting |
Result |
|---|---|
|
High |
Quicker scanning but may noticeably impact endpoint performance. |
|
Medium |
Balances scan speed with endpoint performance impact (default option). |
|
Low |
Slower scanning but has the lowest impact on endpoint performance. |
As logging information is kept on the endpoint, the option you choose will not affect the loggings sent to the server.
|
Setting |
Result |
|---|---|
|
Do not log scanning results |
No scan log is generated. |
|
Normal logging level (includes results summary) |
A standard scan log is generated. |
|
Detailed logging level (includes results summary, name, time and status for each scanned file) |
A detailed scan log is generated. Caution: Logging detailed virus scan results typically generates large amounts of data, especially when recurring scans run frequently. |
If you click Finish at this point, the policy will be created, but not assigned to any endpoints. You can assign it to endpoints at a later time.
The Exclude Files and Folders page opens.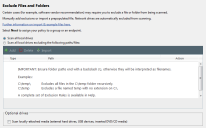
This page enables you to exclude specified files and paths from the scan. You may want to do this because:
Caution: Excluding files or paths from the scan always involves some degree of risk.
Masks and system variables can be used in exclusions. See Exclusion Rules.
More information on excluding files and folders from Ivanti AntiVirus malware scans, including recommended exclusions, can be found in the Ivanti Community Article Excluding files, folders and processes from scans.
|
Method |
Steps |
|---|---|
|
Manually exclude specific files and folders from the scan. |
Click Remove ( |
|
Import an XML file containing a formatted list of file and folder exclusions. |
|
Setting |
Result |
|---|---|
|
Scan locally-attached media |
All storage media (including external hard drives, USB devices, and DVD/CD media) are included in the scan. |
If you click Finish at this point, the policy will be created, but not assigned to any endpoints. You can assign it to endpoints at a later time.
The Assign virus and malware scan policy to groups and/or endpoints page opens.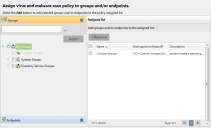
You have created a recurring Recurring Virus and Malware Scan Policy.
Creating a Real-time Monitoring Policy
The Real-time Monitoring Policy Wizard enables you to set real-time scanning options, include or exclude files or paths, and build a list of target endpoints.
A Real-time scan runs when an endpoint accesses a file to perform an action, such as a read or write. This scan type runs continuously in the background to catch malware before it can infect systems.
- Select Manage > Antivirus Policies.
The Antivirus Policies page opens. - Click Create > Real-time Monitoring Policy.
The Real-time Monitoring Policy Wizard opens.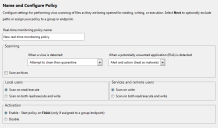
- Type a new name in the Real-time monitoring policy name field. Make the name descriptive, conveying the role of this real-time monitoring policy.
- From the drop-down list, select the action that occurs when a virus is detected.
- To clean an infected file means to completely remove the malicious code so that the file is safe to use. It is not always possible to remove the malicious code, however. When this happens, you can either delete the file or quarantine it. To quarantine means to move it to a safe place on the endpoint where it can be kept for further examination.
In certain cases (such as when the malware is a Trojan) the entire file is malicious. Such a file cannot be cleaned, so the only options are to quarantine or delete it. - Virus detection actions are not used for memory scans.
- From the drop-down list, select the action to be taken when a potentially unwanted application (PUA) is detected:
- [Optional] Select the Scan archives check box to scan compressed files like: .zip, .rar, and .cab
- Scanning the contents of archive files will impact endpoint performance.
- Infected .rar files can be quarantined or deleted, but can't be cleaned.
- Configure the Local users setting. This applies when the endpoint is being used as a workstation, with a logged-on user.
- Configure the Services and remote users setting. This applies when the endpoint is being used as a server. If someone physically logs on to the server, the Local users setting applies.
- Select an Activation option.
- Click Next.
- You have some applications whose manufacturers recommend be excluded from virus scans.
- You have folders containing large amounts of data that you consider relatively safe, such as graphics files. Excluding them from the scan saves time.
- You have files that cause known "false positives" during a scan.
- Exclude files, folders or processes, using one of the following methods:
- Click Add.
A blank entry is added to the exclusions list. - Select an exclusion type from the Type field. File, Folder, or Process.
- Enter the path to the item you want to exclude in the Path field.
- Click
 to add the exclusion to the list.
to add the exclusion to the list.
Repeat this procedure for all files, folders and processes you want to exclude from the scan. - Configure the Optional drives settings:
- Click Next.
- Build a list of targets (endpoints), using either or both of the following methods:
- If the Groups section is not open, click its up arrow to open it.
- Select one or more endpoint groups by selecting their check boxes.
- Click Add.
This adds the group(s) to the Assigned list. - If the Endpoints section is not open, click its up arrow to open it.
- In the search field, do one of the following:
- Type an endpoint name (to search for a specific endpoint)
- Type part of an endpoint name (to search for similarly named endpoints)
- Leave it blank (to search for all available endpoints)
- Click the Search icon.
Depending on what you typed, one or more endpoints will appear in the Namecolumn, with their respective IP addresses. - Select the check box for each endpoint you want to assign.
- Click Add.
This adds the endpoint(s) to the Assigned list. - Click Finish.
The Real-time Monitoring Policy Wizard closes. The newly created policy is displayed in the Antivirus Policies page.
The name must be unique. If it is not, a warning will be displayed.
|
Setting |
Result |
|---|---|
|
Perform no action |
Does nothing with the infected file, but sends an alert to the server. |
|
Attempt to clean then quarantine[default setting] |
Attempts to clean the infected file. If this is not possible, the file is quarantined. An alert is sent to the server. |
|
Attempt to clean then delete |
Attempts to clean the infected file. If this is not possible, the file is deleted. An alert is sent to the server. |
|
Attempt to clean then quarantine then delete |
Attempts to clean the infected file. If this is not possible, the file is quarantined. If it is not possible to quarantine it, it is deleted. An alert is sent to the server. |
Note:
|
Setting |
Result |
|---|---|
|
Perform no action
|
The system ignores the potentially unwanted application. |
|
Send alert only |
An alert is sent to the server only. |
|
Alert and action (treat as malware) |
An alert is sent to the server and the file is cleaned, quarantined, or deleted, according to the action you selected in the When a virus is detected drop down. |
Note:
See Archive Types Supported for Scanning.
|
Setting |
Result |
|---|---|
|
Scan on read/execute |
Scans files before they are used. |
|
Scan on both read/execute and write |
Scans files that are opened for write. New or changed files are scanned on close. |
With Scan on read/execute selected, it is possible that an infected file can be downloaded from the Internet and saved to disk. With Scan on both read/execute and write selected, the scanner will detect and (if possible) remove the malware before writing the file to disk.
|
Setting |
Result |
|---|---|
|
Scan on write |
Scans files that are saved to disk. |
|
Scan on both read/execute and write |
Scans files that are being read or executed, as well as those being saved to disk. This is not the default option, as it increases scanning time. But if the server becomes infected, this is the option to select. |
|
Setting |
Result |
|---|---|
|
Enable - Start policy on Finish (only if assigned to a group/endpoint) |
The policy is created and activated when you click Finish and the wizard closes. The policy must be assigned to at least one endpoint or group. |
| Disable |
The policy is created but not activated when you click Finish and the wizard closes. You may activate it at a later time. |
If you click Finish at this point, a basic policy is created, but is not assigned to any endpoints. You can configure the policy further and assign it to endpoints later.
The Exclude Files, Folders and Processes page opens.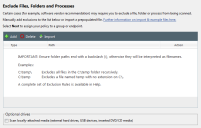
This page enables you to exclude specified files and paths from the scan. You may want to do this because:
Caution: Excluding files or paths from the scan always involves some degree of risk.
Masks and system variables can be used in exclusions. See Exclusion Rules.
More information on excluding files and folders from Ivanti AntiVirus malware scans, including recommended exclusions, can be found in the Ivanti Community Article Excluding files, folders and processes from scans.
|
Method |
Steps |
|---|---|
|
Manually exclude specific files, folders and processes. |
Click Remove ( |
|
Import an XML file containing a formatted list of file, folder and process exclusions. |
|
Setting |
Result |
|---|---|
|
Scan locally-attached media |
All storage media (including external hard drives, USB devices, and DVD/CD media) are included in the scan. |
If you click Finish at this point, the policy will be created, but not assigned to any endpoints. You can assign it to endpoints at a later time.
The Assign real-time monitoring policy to groups and/or endpoints page opens.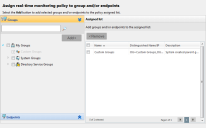
Important: Recurring scans will not run on an endpoint that is shutdown or hibernating at the scheduled scan time.
|
Method |
Steps |
|---|---|
|
To define targets using groups: |
|
|
To define targets using endpoints: |
|
You can remove targets from the Assigned list by selecting the applicable check boxes and clicking Remove.
Importing File, Folder and Process Exclusions
You can facilitate the exclusion of a large number of files, folders, and processes (Real-time Monitoring Policy only) from an antivirus scan through the import of a formatted XML file.
Prerequisites:
- You must be in the process of configuring a Real-time Monitoring Policy, Recurring Virus and Malware Scan Policy or Scan Now.
- You must have created an import XML file. See <install_dir>/AntiVirus/Controls/Components/ExcludeFileImport/NonDomainExcludes.xml for an example.
Scan performance can be improved and false positives prevented by skipping certain files and paths during scans. The Exclude Files and Paths page on the policy and Scan Now wizards enables you to exclude specific files and paths, according to the Exclusion Rules.
More information on excluding files and folders from Ivanti AntiVirus malware scans, including recommended exclusions, can be found in the Ivanti Community Article Excluding files, folders and processes from scans.
As an alternative to manually entering exclusions, you can import an XML file containing a list in a specific format:
<?xml version="1.0"?>
<excludes>
<exclude path=""/>
<pexclude path=""/>
</excludes>
Where:
<exclude path=""/> - file and folder exclusion paths.
<pexclude path=""/> - process exclusion paths (Real-time Monitoring Policies only)
Scan durations can be reduced by avoiding exclusions for software not installed on endpoints.
Keep the exclusion file up to date, especially if you install new software in your environment.
Caution: Do not exclude files or folders unless their contents are known to be threat-free.
Exclusions are not applied to memory scans (when the Scan Memory option is selected during scan configuration).
- From the Exclude Files or Paths wizard page, click the Import button.
The Import Exclusion list from File dialog opens. - Click Browse, select the file, and click OK.
The XML file imports and you will be made aware of any file and path duplicates detected.
You have added a list of exclusions to an antivirus policy or Scan Now configuration.
After Completing This Task:
Continue configuring a Real-time Monitoring Policy, Recurring Virus and Malware Scan Policy or Scan Now.
Exclusion Rules
Use wildcards (masks) and system variables to precisely choose files and paths to exclude from antivirus policies and a Scan Now.
Caution: Do not exclude files or folders unless their contents are known to be threat-free.
Important: Wildcard character * is not accepted in filenames (test00*.log) but can be used for:
- Drives (*\temp )
- Paths (c:\temp\*\) but only once in a single exclusion
Drive and path wildcards can also be used together in a single exclusion (*\temp\*\test\). DOS 8.3 short names (ALONGF~1.TXT) are not accepted.
Exclusions are not applied to memory scans (when the Scan Memory option is selected during scan configuration).
Files without paths
| Rule | Resulting Exclusion |
|---|---|
|
*.exe |
All files with extension EXE. |
|
file.* |
All files named file with any extension. |
|
file |
All files named file with no extension. |
|
file.exe |
All text.exe files. |
Absolute file paths
Folder paths must end with a path separator (\).
| Rule | Resulting Exclusion |
|---|---|
|
c:\temp\ |
All files in the c:\temp folder recursively. |
|
*\temp\ |
All files in the temp folder on all drives recursively. |
|
c:\temp\*.* or c:\temp\* |
All files in the c:\temp folder but not recursively. |
|
c:\temp |
The file named temp with no extension on c:\. |
|
c:\temp\test |
The file named test in the c:\temp folder. |
|
c:\temp\*.exe |
All files with the extension EXE in the c:\temp folder. |
|
c:\temp\test.doc |
The test.doc file in the c:\temp folder. |
Environment variable directories
| Rule | Resulting Exclusion |
|---|---|
|
%WINDIR%\ or %WINDIR%/ or %WINDIR% |
All files in the Windows folder recursively. |
|
%WINDIR%\* |
All files in the Windows folder but not recursively. |
|
%WINDIR%\*\temp\ |
All files in a subfolder named temp recursively within any folder in the Windows folder. |
System account environment variables with multiple values are not supported. For example:
path%
Wildcard Usage
Exclusions can contain the “*” single asterisk wildcard (mask) character in specific combinations, with a maximum of two per exclusion.
Caution: Improper wildcard usage can exclude incorrect files and directories.
Full directory
Restriction:
- Cannot be used with a file exclusion (c:\directory1\*\file.exe is invalid)
- Cannot be used in an exclusion that uses a filename wildcard (*\directory1\*.exe and c:\directory1\*\*.exe are invalid)
- Use of multiple directory wildcards in a single exclusion is not permitted (c:\*\*\directory3\ is invalid)
- For exclusions without a specific file or filename with wildcard, a trailing backslash must be present or the exclusion will be treated as a file exclusion.
|
Valid |
Invalid |
|---|---|
|
c:\*\directory1\directory2\ |
c:\directory1\directory*\ |
|
c:\directory1\*\directory3\ |
c:\directory1\*\directory3\*\directory5\ |
|
%system_variable%\*\directory1\ |
c:\*\*\directory3\ |
Full filename and extension
Restriction: Cannot be used in conjunction with full directory wildcards (c:\directory1\*\*.exe is invalid).
|
Valid |
Invalid |
|---|---|
|
*.exe |
*file.exe |
|
abc.* |
file*.exe |
|
c:\directory1\*.exe |
c:\directory1\*file.exe |
|
c:\directory1\file.* |
c:\directory1\file*.exe |
|
%system_variable%\directory1\*.exe |
c:\*\file.exe |
|
|
%system_variable%\directory1\*\*.exe |
Drives and System Variables
Restriction: Cannot be used with a file exclusion (*\directory1\file.exe is invalid)
|
Valid |
Invalid |
|---|---|
|
*\directory1\directory2\ |
*\directory1\*.exe |
|
*\*\directory2\ |
*\directory1\file.* |
|
*\%system_variable%\directory1\*\ |
*\directory1\file.exe |