The Users Page
This page lists users discovered during active directory synchronization jobs (directory syncs). Use this page to view or create individual users, which you can manage using Ivanti Endpoint Security features.
This page features a directory tree, which lists users and user groups discovered during directory syncs. You can select items in this tree. After selecting an item, information about that item displays on the page.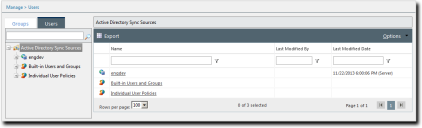
The Users page contains a breadcrumb that indicates your position in the user browser directory tree. Click links in the breadcrumb to move closer to the directory tree root level.
The User Browser Directory Tree
Use the User Browser, a Users page pane, to select users found during directory syncs. The number of users in the tree depends on the number of users detected during syncs.
Click an Expand icon (+) to view active directory sync sources, built-in users and groups, or individual user policies. By expanding the tree, information for selected items becomes more detailed.
To display detailed user information, select a user or group name. After selecting a user or group name from Built-in Users and Groups or Individual User Policies, use the View list to access different views. After selecting a Built-in Users and Groups or Individual User Policies item, you can select from the following view:
- Information
- Application Control Policies
Tip: Click the Groups tab to open the Groups page.
The Users Page Toolbar
This toolbar contains buttons related to assignment of policies to individual users. The buttons that display change based on the item selected from the User Browser directory tree.
The following topics describe the toolbar buttons that display based on the User Browser directory tree item selected:
This toolbar contains buttons related to data exportation.
The following table describes the buttons available when Active Directory Sync Sources is selected from the User Browser directory tree.
|
Button |
Description |
|---|---|
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
the Users page toolbar only appears when the Application Control Policies or the Device Control Policies view is selected.
This toolbar contains buttons related to data exportation.
The following table describes the buttons available when Active Directory Sync Sources is selected from the User Browser directory tree.
|
Button |
Description |
|---|---|
|
Export |
Exports the page data to a comma-separated value ( .csv ) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
The Users page toolbar only appears when the Application Control Policies or the Device Control Policies view is selected.
This toolbar contains buttons related to data exportation.
The following table describes the buttons available when an item is selected from the Built-in Users and Groups sub-items in the User Browser directory tree and the Application Control Policies view is selected (Application Control only).
|
Button |
Description |
|---|---|
|
Unassign |
Unassigns the selected policy (or policies) from the selected user(s). For additional information, refer to Unassigning Policies from Users. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
The following table describes the buttons available when an item is selected from the Built-in Users and Groups sub-items in the User Browser directory tree and the Device Control Policies view is selected (Device Control only).
|
Button |
Description |
|---|---|
|
Create... |
Opens the Create menu. |
|
Device Class Policy (Create... Menu Item) |
Opens the Device Class Policy Wizard. Use this wizard to create a device class policy. When you complete the wizard, the policy is assigned to selected user or group. |
|
Device Collection Policy (Create... Menu Item) |
Opens the Device Collection Policy Wizard. Use this wizard to create a device collection policy. When you complete the wizard, the policy is assigned to selected user or group. |
|
Media Collection Policy (Create... Menu Item) |
Opens the Media Collection Policy Wizard. Use this wizard to create a media collection class policy. When you complete the wizard, the policy is assigned to selected user or group |
|
Port Collection Policy (Create... Menu Item) |
Opens the Port Collection Wizard. Use this wizard to create a port collection policy. When you complete the wizard, the policy is assigned to selected user or group |
|
Assign... |
Opens the Assign Policy dialog. Use this dialog to assign an existing policy to the user or group. |
|
Unassign |
Unassigns any policies assigned to the selected user or group. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
The Users page toolbar only appears when the Application Control Policies or the Device Control Policies view is selected.
This toolbar contains buttons related to individual user management and data exportation.
The following table describes the toolbar buttons that are available when Individual User Policies is selected from the User Browser directory tree.
|
Button |
Description |
|---|---|
|
Add |
Adds a user to Individual User Policies. For additional information on adding users to Individual User Policies, refer to Adding an Individual User to a Policy. |
|
Remove |
Removes a user from Individual User Policies. For additional information on removing users from Individual User Policies, refer to Removing an Individual User from the User Browser. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
The Users page toolbar only appears when the Application Control Policies or the Device Control Policies view is selected.
This toolbar contains buttons related to data exportation.
The following table describes the buttons available when an item is selected from the Individual User Policies sub-items in the User Browser directory tree.
|
Button |
Description |
|---|---|
|
Unassign |
Unassigns the selected policy (or policies) from the selected user(s). For additional information, refer to Unassigning Policies from Users. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. |
The Users page toolbar only appears when the Application Control Policies or the Device Control Policies view is selected.
The Users Page List
On the main portion of the Users page, information about the item selected from the User Browser directory tree is displayed. This main portion is called the Users page list.
Information displayed in the list changes depending on the item selected from the User Browser.
The following topics describe the information that displays when you select a User Browser directory tree item:
When Active Directory Sync Sources is selected from the Users page User Browser directory tree, information about built-in users and groups and individual user policies is displayed.
The following table describes each column that displays when Active Directory Sync Sources is selected.
|
Column |
Description |
|---|---|
|
Name |
The name of an active directory sync source. Clicking a Name link selects the applicable group within the User Browser directory tree. |
|
Last Modified By |
The Ivanti Endpoint Security user that last modified an item within the applicable sync source. |
|
Last Modified Date |
The date that the sync source was last modified. |
When Built-in Users and Groups is selected from the Users Browser directory tree, information about standard built-in users and groups found in active directories are displayed.
The following table describes each column that displays when Built-in Users and Groups is selected.
|
Column |
Description |
|---|---|
|
Name |
The name of a user or group built in to active directory. |
|
Last Modified By |
The last user that last modified an item within the applicable sync source. |
|
Last Modified Date |
The date that the sync source was last modified. |
When an item under Built-in Users and Groups is selected from the User Browser directory tree, information about that built-in user or group is displayed.
There are several views for each Built-in Users and Groups item. After you select a Built-in Users and Groups item, you can change the data displayed by selecting a different item from the View list. You can select from the following views:
- Information
- Application Control Policies (Application Control only)
- Device Control Policies (Device Control only)
The following table describes each field that displays when a Built-in Users and Groups item is selected from the User Browser and Information is selected from the View list.
|
Field |
Description |
|---|---|
|
Name |
The name of the built-in user or group. |
|
Distinguished Name |
The organizational unit and common name for the select item. |
|
Last Modified Date |
The date the user or group was last modified. |
|
Last Modified By |
The user that last modified the user or group. |
|
Sync Name |
The name of the sync job that detected the user or group. |
|
Frequency |
The frequency of the sync job that detected the user or group. |
|
Last Status |
The last status of the sync job that detected the user or group. |
|
Last Status Date |
The date that the last status was updated. |
|
Started On |
The date the sync job that detected the user or group first ran. |
|
Ended On |
The date the sync job that detected the user or group is scheduled to run for the last time. |
The following table describes each column that displays when a Built-in Users and Groups item is selected from the User Browser directory tree and Application Control Policies is selected from the View list.
|
Column |
Description |
|---|---|
|
Action |
Contains a Remove icon you can user to unassign the policy from the selected user. |
|
Status |
Indicates the policy status. Mouse over the icon for a description of the status. |
|
Policy Name |
Indicates the policy assigned to the user. |
|
Policy Type |
Indicates the policy type (Denied Applications, Supplemental Easy Lockdown/Auditor, Trusted Path, and Local Authorization). |
|
Blocking |
Indicates the policy blocking value (N/A, Off, Non-authorized). |
|
Logging |
Indicates the policy logging value (Off, On, Authorized, Non-authorized, Non-authorized Authorized) |
|
Source |
Indicates the policy source (Assigned or Unassigned). |
|
Assigned Date |
Indicates the date and time the policy was assigned to the selected network user. |
Additionally, when the Application Control Policies view is selected, you can expand each list item. Expand an item by clicking a rotating chevron. The following table describes each field that displays when you expand a list item.
|
Field |
Description |
|---|---|
|
Created by |
The Ivanti Endpoint Security user who created the policy applied to the selected network user. |
|
Created date |
The date and time the policy was created. |
|
Last updated by |
The Ivanti Endpoint Security user who last modified the applicable policy. |
|
Last updated date |
The date and time the policy was last modified. |
|
Trusted Paths |
The trusted path(s) applied to the selected network user. This field only appears for Trusted Path policies. |
The following table describes each column that displays when a Built-in Users and Groups item is selected from the User Browser directory tree and Device Control Policies is selected from the View list.
|
Column |
Description |
|---|---|
|
Status |
Indicates the policy status. Mouse over the icon for a description of the status. |
|
Policy Name |
Indicates the policy assigned to the user. |
|
Policy Type |
Indicates the policy type (Device Class Policy, Device Collection Policy, Media Collection Policy, and Port Control Policy). |
|
Device Collection |
Indicates the device collection the policy applies to. |
|
Source |
Indicates the policy source (Assigned or Unassigned). |
|
Device Class |
Indicates the device class the policy applies to. |
|
Last Update |
Indicates the date and time the policy was last updated. |
Additionally, when the Device Control Policies view is selected, you can expand each list item. Expand an item by clicking a rotating chevron. The following table describes each field that displays when you expand a list item.
|
Field |
Description |
|---|---|
|
Name |
The name of the individual policy. |
|
Value |
The value of the individual policy. |
|
Description |
The description of the individual policy. |
When Individual User Policies is selected from the User Browser directory tree, a list of manually added network users that have policies directly applied to them is displayed.
The following table describes each column that displays when Individual User Policies is selected.
|
Column |
Description |
|---|---|
|
Name |
The name of the user. Click the name to move to that user in the User Browser directory tree. |
|
|
The email address of the user. |
|
Last Modified By |
The user that last modified the user within the User Browser directory tree. |
|
Last Modified Date |
The date that the user was last modified. |
When you select an item beneath Individual User Policies in the Users Browser directory tree, information about that user and its associated policies are displayed.
There are several views for each Individual User Polices item. After you select a Individual User Polices item, you can change the data displayed by selecting a different item from the View list. You can select from the following views:
- Information
- Application Control Policies (Application Control only)
- Device Control Policies (Device Control only)
The following table describes each column that displays when an Individual User Policies item is selected from the User Browser directory tree and Information is selected from the View list.
|
Field |
Description |
|---|---|
|
Name |
The name of the individually added user or group. |
|
Distinguished Name |
The organizational unit and common name for the select item. |
|
Last Modified Date |
The date the user or group was last modified. |
|
Last Modified By |
The user that last modified the user or group. |
|
Sync Name |
The name of the sync job that detected the user or group. |
|
Frequency |
The frequency of the sync job that detected the user or group. |
|
Last Status |
The last status of the sync job that detected the user or group. |
|
Last Status Date |
The date that the last status was updated. |
|
Started On |
The date the sync job that detected the user or group first ran. |
|
Ended On |
The date the sync job that detected the user or group is scheduled to run for the last time. |
The following table describes each column that displays when an Individual User Policies item is selected from the User Browser directory tree and Application Control Policies is selected from the View list.
|
Column |
Description |
|---|---|
|
Action |
Contains a Remove icon you can user to unassign the policy from the selected user. |
|
Status |
Indicates the policy status. Mouse over the icon for a description of the status. |
|
Policy Name |
Indicates the policy assigned to the user. |
|
Policy Type |
Indicates the policy type (Denied Applications, Supplemental Easy Lockdown/Auditor, Trusted Path, and Local Authorization). |
|
Blocking |
Indicates the policy blocking value (N/A, Off, Non-authorized). |
|
Logging |
Indicates the policy logging value (Off, On, Authorized, Non-authorized, Non-authorized Authorized) |
|
Source |
Indicates the policy source (Assigned or Unassigned). |
|
Assigned Date |
Indicates the date and time the policy was assigned to the selected network user. |
Additionally, when the Application Control Policies view is selected, you can expand each list item. Expand an item by clicking a rotating chevron. The following table describes each field that displays when you expand a list item.
|
Field |
Description |
|---|---|
|
Name |
The name of the individual policy. |
|
Value |
The value of the individual policy. |
The following table describes each column that displays when an Individual User Policies item is selected from the User Browser directory tree and Device Control Policies is selected from the View list.
|
Column |
Description |
|---|---|
|
Status |
Indicates the policy status. Mouse over the icon for a description of the status. |
|
Policy Name |
Indicates the policy assigned to the user. |
|
Policy Type |
Indicates the policy type (Device Class Policy, Device Collection Policy, Media Collection Policy, Port Control Policy) |
|
Device Class |
Indicates the device class the policy applies to. |
|
Device Collection |
Indicates the device collection the policy applies to. |
|
Source |
Indicates the policy source (Assigned or Unassigned). |
|
Last Update |
Indicates the date and time the policy was last updated. |
Additionally, when the Device Control Policies view is selected, you can expand each list item. Expand an item by clicking a rotating chevron. The following table describes each field that displays when you expand a list item.
|
Field |
Description |
|---|---|
|
Name |
The name of the individual policy. |
|
Value |
The value of the individual policy. |
|
Description |
The description of the individual policy. |