What is Easy Auditor?
Easy Auditor is a policy that creates a whitelist of authorized applications already on an endpoint, without blocking any applications that are installed later. It scans endpoints and adds the executables it finds to each endpoint's whitelist. This lets you to build a picture of application usage on the network without affecting users' ability to run the applications they need.
Plan Ahead
Scanning your endpoints to build the endpoint whitelist requires a fair amount of CPU and disk resources and may take several hours to complete. Run this scan outside of operating hours, if possible, to avoid disrupting productivity.
Make sure your endpoints are configured so that they do not go into sleep or hibernation modes, as these force the scan to start over.
Select Sample Endpoints
In this phase, start by scanning 10 or fewer endpoints so that you can review the initial logs without being overwhelmed by data. Select endpoints that give you the widest representation of variability within your organization. These endpoints will populate the Application Library with a diverse range of applications. Include endpoints from departments such as:
- Human Resources
- IT
- Sales
- Engineering
Scan Endpoints with Easy Auditor
-
From the Endpoint Security Console, select Manage > Policy Wizards > Easy Auditor.
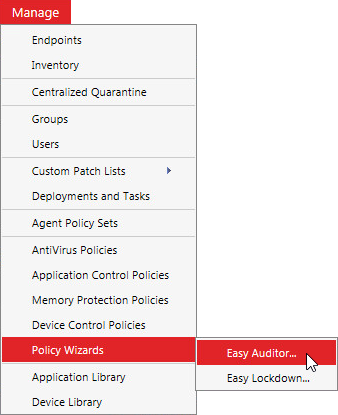
The Easy Auditor Wizard opens.
-
Proceed through the wizard. See Creating an Easy Auditor Policy in the Application Control Help for additional explanation and detailed steps.
Avoid positive logging, which is logging the execution of authorized applications. Logging authorized applications can result in very large log file sizes and consumes excess space on your Endpoint Security Server. Instead, log only non-authorized applications. You can, however, log authorized applications when troubleshooting an endpoint.
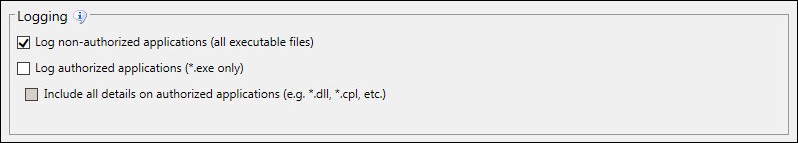
You've scanned your endpoints for applications and created an endpoint whitelist. Each endpoint now goes into a non-blocking audit mode and logs when applications are executed, based on the logging settings you selected. These logs are sent to your Endpoint Security Server so that you can analyze them.