Neurons for ITSM OpenID Connect Configuration
The Neurons for ITSM OpenID Connect (OIDC) configuration is based on the IdentityServer3 library.
The steps to enable the Neurons for ITSM OIDC are as follows:
•Adding the necessary Metadata (new Business Objects in ConfigDB and TenantDBs)
•Updating Neurons for ITSM AppServer Web.Config Settings
•Adding a Token Signing Certificate to ConfigDB
•Adding an OIDC_Client record to ConfigDB for the Client Application
Adding Metadata
The Neurons for ITSM OIDC requires new business objects to be added to ConfigDB and TenantDBs, which will be included in the 2019.1 out-of-the-box databases and upgrade packages. However, they are also available in the following standalone packages in the Git SM.UpgradePackageFiles repository:
•OpenIDConnect/OpenIDConnect_ConfigDB.MetadataPatch
•OpenIDConnect/OpenIDConnect_Tenant.MetadataPatch
OpenIDConnect_ConfigDB.MetadataPatch adds the following metadata to ConfigDB:
•OIDC_Client business object and associated workspace
•OIDC_Claim business object (child object of OIDC_Client)
•OIDC_Secret business object (child object of OIDC_Client)
•OIDC_Flow business object and validation list
•OIDC_TokenUsage business object and validation list
•OIDC_TokenExpiration business object and validation list
•OIDC_AccessTokenType business object and validation list
•OIDC_Token business object (stores OIDC refresh tokens and other token types)
•"OIDCTokenSign" Certificate Category (added to FRS_Certificate_Category validation list)
OpenIDConnect/OpenIDConnect_Tenant.MetadataPatch adds the following metadata to a Tenant DB:
•OIDC_Consent business object (stores OIDC consent choices made by users)
Updating Web.Config Settings
The following Neurons for ITSM AppServer Web.Config settings are available:
<appSettings>
<add key="EnableOpenIDConnectAuthentication" value="true" />
<add key="OIDCLegalUrl" value="https://www.ivanti.com/company/legal" />
<add key="OIDCPatentsUrl" value="https://www.ivanti.com/company/legal/ivanti-patents" />
<add key="OIDCHTMLFolder" value="ISM" />
<add key="OIDCSiteName" value="Ivanti Cloud" />
</appSettings>
EnableOpenIDConnectAuthentication - Required to enable Neurons for ITSM OIDC. Default value is "false".
OIDCLegalUrl - Optional. The legal URL link displayed on the OIDC login page. Default value is "https://www.ivanti.com/company/legal".
OIDCPatentsUrl - Optional. The patents URL link displayed on the OIDC login page. Default value is "https://www.ivanti.com/company/legal/ivanti-patents".
OIDCHTMLFolder - Optional. Controls the look and feel of the OIDC login page etc. Default is "ISM". Other options are "Uno" and "app" (generic).
OIDCSiteName - Optional. Controls the title text displayed on the OIDC login page etc. Default is "Ivanti Cloud".
Adding a Token Signing Certificate
Neurons for ITSM OIDC requires a Token Signing Certificate. You can create a self-signed certificate using the following command line tools:
makecert.exe -r -pe -n "CN=OIDCSign1" -b 01/01/2017 -e 01/01/2025 -sky signature -a sha256 -len 2048 -sv OIDCSign1.pvk OIDCSign1.cer
pvk2pfx.exe -pvk OIDCSign1.pvk -spc OIDCSign1.cer -pfx OIDCSign1.pfx -po Password12
makecert.exe will ask you for a private key password. You can select "none".
The above will result in a OIDCSign1.pfx certificate file with a password "Password12"
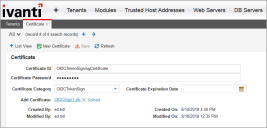
Add the certificate to the ConfigDB Certificates table as shown below:
The Certificate ID must be "OIDCTokenSigningCertificate". The Certificate Category must be "OIDCTokenSign".
Adding OIDC Client Configuration
Each OIDC Client Application must have a corresponding OIDC_Client record in ConfigDB that specifies its configuration and maps it to an Neurons for ITSM Tenant and corresponding users (usually Employee records).
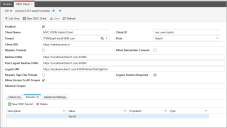
The configuration for the "MVC OWIN Hybrid Client" example client application is shown in the following screenshot:
Field descriptions are as follows:
| Field | Description |
|---|---|
| Enabled |
Specifies if the client record is enabled |
|
Client Name |
Client display name (used for logging and consent screen) |
|
Client ID |
Login ID of the employee of the tenant used for generating the JWT Token. Open the Employee workspace to get the Login ID. |
|
Tenant |
Neurons for ITSM Tenant Mapping for the Client |
|
Flow |
Specifies allowed flow for client (either AuthorizationCode, Implicit, Hybrid, ResourceOwner, ClientCredentials or Custom). If you want to generate JWT Token using the OIDC Login API, ensure you select the Flow as ResourceOwner. |
|
Client URI |
URI to further information about client (used on consent screen) |
|
Require Consent |
Specifies whether a consent screen is required |
|
Allow Remember Consent |
Specifies whether user can choose to store consent decisions |
|
Redirect URIs |
Specifies the allowed URIs to return tokens or authorization codes to (comma separated list) |
|
Post Logout URIs |
Specifies allowed URIs to redirect to after logout (comma separated list) |
|
Logout URI |
Specifies logout URI at client for HTTP based logout (required for Single-Sign-Out) |
|
Require Sign Out Prompt |
Specifies if the client will always show a confirmation page for sign-out |
|
Logout Session Required |
Specifies if the user’s session ID should be sent to the Logout URI |
|
Allow Access To All Scopes / Allowed Scopes |
By default a client has no access to any scopes. Either specify the scopes explicitly here (recommended) or set AllowAccessToAllScopes to "true". |
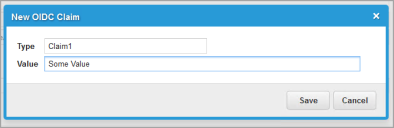
Additional claims can be added to the JWT that's generated using the OIDC_Claim child object:
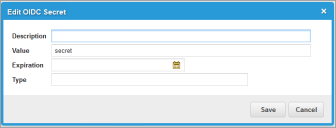
Some OIDC Flows (e.g. Hybrid) require a "secret" value that the Client must supply. Secrets are adding using the OIDC_Secret child object:
Only the Value field is required. The other fields are optional.
The OIDC_Client business object supports all the IdentityServer3 Client settings. The remaining settings are available via the Advanced Settings Form.
The configuration for the "MVC OWIN Implicit Client" example client is as follows.
Implicit Flow does not require a secret.