Configure the RBVM Data Import Connector to Import RBVM Events
You can synchronize data to Neurons for ITSM from RBVN, based on filter criteria configured in the RBVM Connector settings. With use of Open Data Protocol (OData) calls, data is imported directly from RBVM, ensuring updated information is always available. This integration also removes the requirement to edit scripts, and the limitation on importing records into Neurons for ITSM.
The connector configuration UI feature enables you to easily set up a connection, set filter criteria for the data, and set schedules to run the connector and import from RBVM. Once the data is pulled from RBVM, based on the filter criteria then the Security Events are created, and if the Event Severity and Risk Score of the Security Event is greater than or equal to 9 then Security Incidents are created.
Prerequisites
To enable connection between Neurons for ITSM and the RBVM client, your tenant Configuration Database (DB) needs to be configured to permit the connection. which must be setup by Ivanti. Please provide Ivanti Professional Services Organization (PSO) with the following information when requesting setup:
•RBVM Platform ID
•RBVM Client ID
•RBVM API Key
Configure the RBVM Connector
An RBVM Connector is provided in the Data Import Connections list. If you cannot locate this connector in the list, contact Ivanti Professional Services Organization (PSO).
1.Log in as Administrator, and open the Configuration console.
2.Select Tools > Integration Tools > Data Import Connections.
3.Click on the RBVM Connector entry.
The Connection Settings configuration UI opens. You do not need to alter the default settings.
4.Click Test Connection.
The result is displayed in a popup window.
5.Click Next.
The Filter Manager settings open.
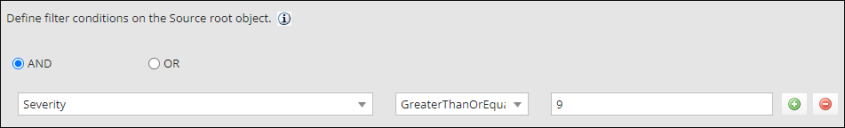
6.Select your required criteria in the drop-down lists and enter a value in the value field. You can define one or more filters to apply, click Add  to add more filters.
to add more filters.
Filters defined here determine the range of data imported from the RBVM client.
Example: In the screenshot shown above, RBVM data is imported if the Severity value is greater than, or equal to 9.
You can edit the criteria or add additional filters at any time.
7.Click Next, and then select a schedule (or schedules) from the list in the Schedule Manager:
•Select one or more schedules, and then click Next to move to the next screen. To select multiple schedules, hold down the Ctrl key, and then select each schedule. You can create a new schedule in the Schedule Entry workspace if required, and then select it from this list. To create a new schedule, see About the Schedule Entry and Scheduled Jobs Workspaces.
•If no schedule is required, click Next to move to the next screen.
If you select to proceed without a schedule, a Confirmation dialog is shown, select Yes to proceed, or No to cancel.
8.Publish the connection configuration:
•Publish: Select this option to publish without running the connection configuration. If you selected a schedule, the connection runs at the scheduled time and imports any data from RBVM that meets the filter criteria. The imported data is automatically turned into Security Events and Security Incidents in ITSM.
•Publish and Run Now: Select this option to publish and run the connection configuration now. Selecting this option immediately imports any data from RBVM that meets the filter criteria. The imported data is automatically turned into Security Events and Security Incidents in ITSM.
•Publish and Test Run: Select this option to publish and test the connection and import only, no Security Events or incidents are created.
When you run the connector, you can check the Integration Queue to see if the request is queued, running, or has run and completed. To do this select Integration Tools > Integration Queue.
Verify the RBVM Data Import
When the RBVM Connector run has completed, check the Event and Security Incident workspaces to verify that any imported data is published into new events and Security Incidents.
1.Log on as Administrator.
2.Open the Event workspace and check that corresponding new events are created.
3.Open the Security Incident workspace and check that corresponding new Security Incidents are created.