Security Concept
DSM manages servers and clients in large network environments. These management tasks require DSM to perform system-related actions that imply extensive rights and permissions for the individual computers in the network. DSM employs the following security procedures for protecting the relevant data.
Password Encryption
DSM uses specific user accounts, that the network administrator assigns individually when configuring DSM, to get the required permissions.
DSM protects the passwords as follows, to prevent that these user accounts are misused:
- The user name and the password of the individual accounts are stored in the configuration database (ICDB).
- Management Points:
The passwords of accounts that allow access to the components of the DSM infrastructure server (Management Points) are encrypted by means of the Advanced Encryption Standard (AES), thus providing a high-level security standard. The key length is 256 (AES 256).- These accounts include
- BLS authentication
- Distribution Service
- Database access
- Service Installation Service
- Client Proxy
- Each Management Point Password is encrypted with an AES 256 key that is generated by using a public key. A private key is required for decryption. Both public and private key are generated when configuring the DSM environment and are only valid within this specific environment.
- The DSM configuration mechanism guarantees that the private key for decryption is stored in a highly protected directory on the depots only the DSM infrastructure can access any time.
The following ICDB setting lets you specify one user group per depot that has access to the directory:
Depot > Group with access to the private key.
The members of this group must all be distribution accounts that are used to access the depot (see figure below). In addition to this group, the local SYSTEM account is assigned Read and Write access to the directory.
The system distributes the directory to the depots as usual and protects it according to the distribution accounts that are being used. This does not apply to HTTP depots because they must be prepared manually and the directories cannot be protected automatically (see also: Protecting HTTP Depots).
- These accounts include
- Managed Clients:
The passwords for accounts every managed computer must have are encrypted for each DSM environment during the installation of DSM 2015.1.- DSM uses the following default accounts:
- DSM Runtime Service
- Depot Access
Alternatively, you can use computer accounts from the Active Directory rather than DSM accounts (see below: Zero Account Model). This also applies to existing environments.
- DSM uses the following default accounts:
Encryption of Data on Managed Computers
The variables and installation parameters a managed computer needs are stored encrypted in the Windows registry. The required key is stored in a protected area of the registry. Encryption is unique for every managed computer. There is one exception regarding roaming profiles: In this case, the encryption is unique for every DSM environment.
The DSM control data, which is cached locally on managed computers, resides in a directory only local administrators can access. The account of the DSM Runtime Service is one of the local administrator accounts.
In addition, you can protect the log files of managed computers by assigning Read access to the log file directory only for local administrators. There is a special configuration setting for this purpose.
Using Computer Accounts Instead of DSM Accounts (Zero Account Model)
DSM 2015.1 introduces a complete way around using dedicated DSM user accounts on managed computers. Provided that there is an Active Directory environment, you can use the SYSTEM account as user account for both the DSM Runtime Service and also for accessing the depot. All of the DSM processes running with the SYSTEM account use that computer account for accessing external resources. This implies that the computer accounts are assigned Read access to these external resources.
When you install DSM for the first time, you can specify the required accounts in the Configuration Wizard.
In general, existing DSM environments can change to the Zero Account Model.
Protecting the Private Key in Existing Environments
When you update to DSM 2015.1, the system automatically provides access permissions (based on the existing infrastructure) for the directory that contains the private key for decrypting passwords.
During this procedure, the system assigns Read and Write access to all distribution accounts that are using the respective depot in one of the distribution steps. In addition, the local SYSTEM account is assigned Read and Write access to the directory.
The following figure illustrates the distribution accounts concerned. The example also shows the exceptions when using a virtual depot and when Management Points access the key directory.
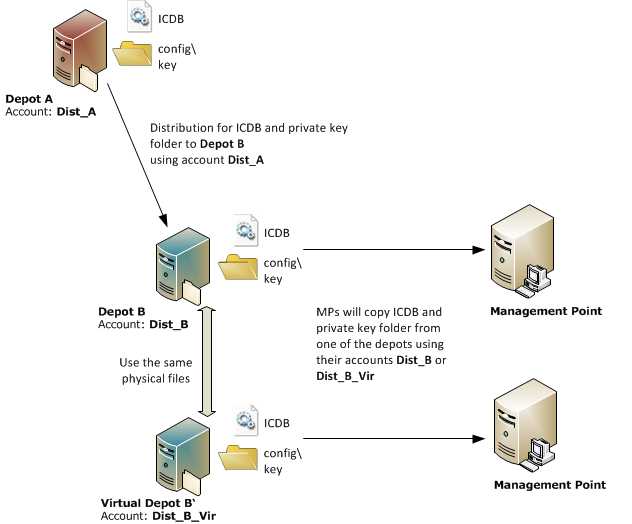
When you update to DSM 2015.1, the system automatically assigns Read and Write access to the accounts Dist_A, Dist_B and Dist_B_Vir for the config\key directory on Depot B.
If you specify a user group later that has access to the directory, the same accounts must be added as member of this group (ICDB setting Depot > Group with access to the private key).