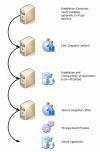
Procedure of application virtualization with ThinApp
Virtualizing an application with ThinApp is performed in the following steps:
- Step 1: The first snapshot of the system (file system, registry) is captured on a freshly installed computer.
- Step 2: The application itself is installed.
- Step 3: The application is configured.
- Step 4: The second snapshot of the system is captured. The changes since the first snapshot (file system, registry) are determined, and are the basis for the build process that generates a virtual application.
- Step 5: The build process to create a virtual application can be modified as required. This means adapting the package.ini file.
Figure: Procedure of application virtualization. Click to enlarge.
Step 4 - Details
When taking the second snapshot of your installation computer, ThinApp captures the files and registry keys configured or deleted since the first snapshot. The executable files it finds become entry points in the virtual application. If you virtualize Microsoft Office for instance, the executable files for Word, Excel, etc become entry points of the virtual Microsoft Office application.
Step 5 - Details
In the package.ini file, which drives the ThinApp build process, a shortcut appears for each entry point that is found. ThinApp makes one entry point the primary executable, provisioning it with the ThinApp virtualization layer (runtime environment, runtime). The Virtual Application wizard enables you to define which entry points there are to be in the virtual application, and which of them is to hold the ThinApp virtualization layer.
An .exe file is formed for each entry point. Only the primary executable is able to execute by itself. All other entry point executables need the primary executable to start, with the runtime environment in the same directory. They share a virtual registry and a virtual file system with the primary executable.
The virtual application per se does not alter any more. So it can be filed away in a released folder with read-only access rights.