Aqua Security Connector Guide
Summary: How to set up the Aqua Security connector in Ivanti Neurons RBVM/ASPM/VULN KB.
Aqua Security’s Container Security Platform Overview
Aqua Security’s container security platform Aqua provides automated and manual scanning capabilities for container images stored on supported image registries. The Ivanti Neurons for ASPM platform supports creating an Aqua Security connector, which automatically pulls vulnerability data and metadata of container images scanned by Aqua for ingestion into Ivanti Neurons for ASPM. Pulled Aqua data can be viewed on the Applications and Application Findings page.
Connector Configuration
Prerequisites
- Active subscription to Ivanti Neurons for ASPM.
- Active subscription to AquaSec.
- Access Key and associated Secret Key for AquaSec User.
- Scan data from at least one registry integration and at least one image repository in Aqua
User Setup
To set up the connector, the user needs API access to an AquaSec account with full access to the AquaSec service. The user needs the following permissions:
- A role which grants read access to the image repositories and registries containing scan data
- In addition to general permissions, additional restrictions such as IP address restriction and group restriction can be imposed to limit the scope of the API keys.
Connections
The following API calls are performed during a connector run to pull security vulnerabilities from AquaSec into Ivanti Neurons for ASPM.
|
API Type |
Endpoint |
|---|---|
|
Get Assets |
/build/repositories |
|
Get Vulnerabilities |
/build/detections |
Platform Setup
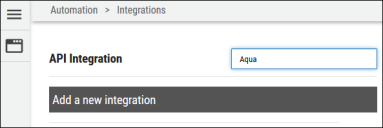
When logged into the platform, navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type Aqua to find the connector.
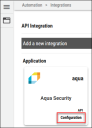
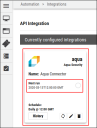
Locate the Aqua Security card on the page and click Configuration.
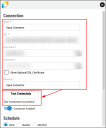
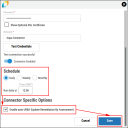
Enter the requested details for the connection, and choose an existing network for the Aqua data to be associated with in the Ivanti Neurons for ASPM platform. Click Test Credentials to verify the credentials are correct and have access to make API calls to the Aqua Security instance.
Configure the desired schedule for the connector to retrieve results from the Aqua instance. Optionally turn on Enable auto URBA (Update Remediation by Assessment), and click Save to create the connector.
Optional Configurations
When the platform successfully connects with the provided credentials, the user can finalize and save the configuration options. As soon as the connector is created, it will begin pulling data from the Aqua Security platform. The connector’s card will also show the next scheduled time and date results will be fetched from Aqua. Check the connector’s status by clicking the History button.
To run the connector on demand, click the Sync icon.
Editing a Connector Configuration
Ivanti Neurons for ASPM
Connector configurations can be updated at any time after creation. Go to the Automate > Integrations page and select the specific connector you want to update.
Utilizing the Connector
The data from a AquaSec API is ingested into Ivanti Neurons for ASPM as Applications and Application Findings. The Scanner Name associated with these scans is AquaSec. Scanner Name can be used as a filter for Applications and Application Findings. Container image scan data retrieved from Aqua is stored in Ivanti Neurons for ASPM using the Application and Application Finding models. The primary metadata and identifier of a container image and its vulnerability data were used to represent applications and findings in the platform.
Assets
Assets extracted from AquaSec API are shown on the Hosts page. Project and version details are also extracted from the endpoint.
Findings
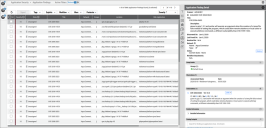
Scan data pulled from AquaSec via the connector can be viewed on the Network > Application Security > Application Findings pages. Container image findings are identified using the image’s metadata (as described above). In addition, all vulnerabilities reported by Aqua are with respect to a resource (such as an executable or a binary) that is part of the image and is known to be vulnerable. Data about a finding’s vulnerable resource can be found in the Container Resource Information section of a container finding’s detail pane.
CVE data is frequently given as it pertains to a container image vulnerability. CVE and other vulnerability data can now be found in the Application Finding Detail pane under the Vulnerabilities section. Ivanti Neurons for ASPM uses CVE data to provide users with information about associated threats. Threat data is now also displayed in a container finding’s detail pane.
Connector Data Mapping
This table maps the high-level fields from AquaSec with that of the Ivanti Neurons for ASPM platform.
|
Section |
Ivanti Neurons for ASPM Field |
Source Field |
|---|---|---|
|
Application |
Address |
Registry Name + Repository + Tag |
|
Name |
Repository + Tag |
|
|
Scanner Type |
A new scanner type, CONTAINER |
|
|
Scanner Name |
A new scanner name, AQUASEC |
|
|
Location |
Vulnerable Resource Identifier |
|
|
Application Finding |
Title |
Title |
|
Description |
Description |
|
|
Severity |
Aqua Score |
|
|
Solution |
Fix Version, Solution |
|
|
Finding Type |
A new finding type, CONTAINER |
|
|
Vulnerabilities |
Title |
|
|
Resource Detail |
Name |
Resource Name |
|
Path |
Resource Path |
|
|
Type |
Resource Type |
|
|
CPE |
Resource CPE |
|
|
Version |
Resource Version |
|
|
Hash |
Resource Hash |
|
|
Arch |
Arch |
|
|
Licenses |
Licenses |