Finding Article Overview
The platform provides multiple ways for you to add your own data to findings, including custom attributes and notes. You can also apply finding articles to findings if you need to provide more structured or more visual examples for other users. For example, you can write an article that provides configuration or patching steps with screenshots and attach additional documentation. You can create and apply finding articles from the Host Findings or Application Findings pages.
If you work as an analyst, you can write finding articles to provide more threat context. You can mark a finding article as a “proof of exploitation” (PoE) and apply it to one or more findings. The platform also allows you to prioritize the PoE by spotlighting it within the platform. You have the option to create a PoE that changes the VRR score of any associated finding to a 10.0 and alters the assignment of asset and organizational RS3 scores.
Viewing Finding Articles
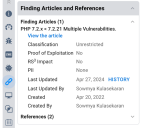
You can view the finding articles associated with a finding under the Finding Articles and References section of the Finding Details. This section gives you access to the finding article history and the full article.
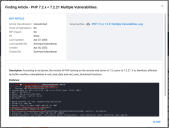
To view the full article and its attachments, click View the Article. The platform opens a popup containing the full text and the attachments.
Finding Article Classification
To perform any action on a finding article, you must have the appropriate privileges. “Read” privileges allow you to view the full text of an article and to download the attachments. “Modify” privileges enable creating finding articles, modifying them, deleting them, and applying them to findings. To see the full list of privileges, visit the Roles page within the platform.
An article can have one of two classifications: Unrestricted or Restricted. One set of privileges exists for each classification level. However, the Restricted privileges enable you to perform the same actions on both unrestricted and restricted articles.
Authors may want to mark articles as restricted if they contain sensitive information. For example, you may want to make a PoE or a list of asset identifiers available only to other users who can read restricted articles.
Administrators cannot use asset groups to control access to specific finding articles. APIs for findings, assets, and groups check a user’s group assignments before returning data. APIs for finding articles ignore asset groups. For example, assume that a user with the ability to read an unrestricted finding article has access to all unrestricted finding articles.
Creating an Article
You must first have the correct privileges to create or update a finding article. Roles that grant these privileges include Vulnerability Manager, Security Analyst, Finding Article Owner, and Restricted Finding Article Owner.
Go to either the Host Findings page or the Application Findings page. Locate the Finding Articles menu.
To create an article, open up the Finding Articles menu and select CREATE. If you select one or more findings first, you will automatically apply your new article to those findings.
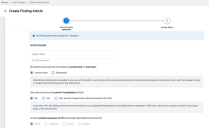
On the first step, you must
- Provide a title. The title of the article must be unique and can be up to 256 characters in length.
- Choose a classification level (unrestricted or restricted). If you lack the privilege to create an restricted article, you will only have the option to create an unrestricted article.
- State whether the finding article is informational or provides proof of exploitation. If your article describes an exploit for a vulnerability, you can also optionally give higher priority to any finding associated with the finding article. The last option turns the finding article into a PoE with RS3 Impact. As the name implies, this option has a direct impact on the asset, group, and client level RS3 scores (more below).
- State whether the vulnerability has the potential to expose Personally Identifiable Information (PII) to an attacker. You can only modify this property if you have marked the finding article as a PoE.
When you complete the first step, the platform creates a finding article with an empty body. The finding article will also become visible in the Finding Articles list.
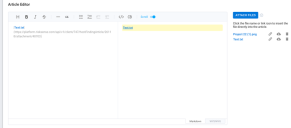
In the next step, you will provide the body of the finding article. The markdown editor offers both a split-pane markdown editor with a preview and a full-size WYSIWYG editor.
To the right of the editor, you can upload attachments. Once you have uploaded an attachment, you can add it to the finding article by clicking on the file name or the link icon. Images show up directly within the editor. For other types of files, the editor will insert them as links.
Regardless of whether you insert attachment links directly into the article, users can still access any attachments from the full article view accessible from the Finding Details.
Note that the platform validates attachment links before it lets you submit. It may show an error message if the article contains
- Links that refer to deleted attachments or invalid attachment IDs
- Links to attachments belonging to other articles
Updating a Finding Article
You can open up an article for editing from the Finding Articles menu or from the full finding article view.
Applying a Finding Article to Finding
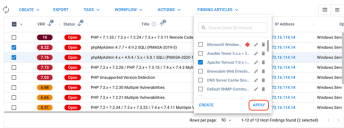
To apply an article to a finding, first select the findings. Then open the Finding Articles menu and search for the article.
Check the box next to the article. Then select Apply. Your update will become visible in a few moments.
Removing a Finding Article from a Finding
To remove a finding article from a finding, first select the findings. Then open the Finding Articles menu and search for the article.
Uncheck the box next to each finding article that you want to remove from these findings. Then select Apply.
Impact of Applying a PoE
If the finding article is informational, the article will show up in the Finding Articles and References section of the Finding Details.
If the finding article is a PoE, the PoE will show up in the Threats section of the Finding Details as well as the Finding Articles and References section. On the system dashboards, counts of weaponized findings will include findings associated with PoEs.
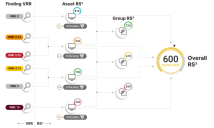
If a PoE has RS3 Impact, then the following occur:
- Any finding associated with that PoE will automatically have a VRR score of 10.0.
- As long as any of these findings remain open, any impacted asset will have an RS3 score of 300.
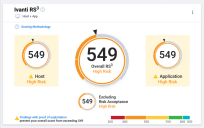
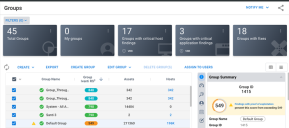
- The system caps any RS3 average that includes the impacted assets to 549, including the overall client RS3.
- Warning indicators will appear on widgets within the Executive and Prioritization Dashboards as well as Group, Host, and Application list views.
Examples of Dashboard and List View Indicators
The platform enables you to quickly locate any open findings that have a PoE with RS3 Impact. For example, the Ivanti RS3 widget on the Executive Dashboard shows warning indicators when the overall RS3 average includes one or more impacted assets. You can click the text Findings with proof of exploitation… to go directly to the open findings with the PoE.
The Groups, Hosts, and Applications list view shows similar warnings. On these pages, a warning indicator will appear in the RS3 column. The detail pane will provide more information and let you quickly navigate to the open findings with the PoE.
Reversing the Impact of a PoE with RS3 Impact
To reverse the effects of a PoE with RS3 Impact, you can either
- close the finding
- remove it from the finding
- delete the finding article
- update the finding article to change its type
Examples of Applying a PoE with RS3 Impact
Assume in these examples that you apply a PoE to open finding A on client A and on open finding B on client B. The visible outcomes can differ depending on the original RS3 score, the criticality of the impacted asset, and the number of assets included in the calculation.
On Client A, the overall RS3 score shows more change because the PoE with RS3 Impact limits how high the score can go: a max score of 549.
|
Client |
Before PoE with RS3 Impact |
After PoE with RS3 Impact |
|---|---|---|
|
A Finding A is on Asset A Total assets contributing to client score: 1500 |
Finding A VRR Score: 7.5 Asset A RS3 Score: 650 Client A RS3 Score: 705 |
Finding A VRR Score: 10.0 Asset A RS3 Score: 300 Client A RS3 Score: 549 |
|
B Finding B is on Asset B Total assets contributing to client score: 1500 |
Finding B VRR Score: 10.0 Asset B RS3 Score: 422 Client B RS3 Score: 513 |
Finding B VRR Score: 10.0 Asset B RS3 Score: 300 Client B RS3 Score: 512 |