GitHub Advance Security (Dependabot) Connector Guide
Summary: How to set up and use the GitHub Advance security (Dependabot) connector in IvantiNeuronsRBVM/ASPM/VULN KB.
Overview
GitHub's security features help keep your code, and secrets secure in repositories and across organizations. Dependabot’ s alerts inform about vulnerabilities in the dependencies that you use in your repository. These are available for organization-owned and user-owned repositories.
For more information, see GitHub Security Features.
Connector Configuration
Prerequisites
- GitHub account and active GitHub Code Security Plan
- One or more repos in GirHub
- Setup a user with an API Key
Connector API Calls
The following API calls are performed during a connector run to pull security vulnerabilities into Ivanti.
GitHub API Version: 2022-11-28
|
API Type |
Endpoint |
|---|---|
|
Authentication |
GET Method: https://api.github.com/octocat |
|
Get List of Repositories |
GET Method: https://api.github.com/orgs/{{organization Name}}/repos |
|
Get Repository Details |
GET Method: https://api.github.com/repos/{{organizationName}}/{{Repo Name}} |
|
Get Dependabot Alerts Details |
GET Method: https://api.github.com/repos/{{organization}}/{{Repo}}/dependabot/alerts |
Rate Limits
GitHub enforces rate limits on REST API requests to control the number of calls that can be made within a defined time window. These limits are designed to prevent abuse, mitigate denial-of-service (DoS) attacks, and maintain consistent API availability and performance for all users.
Primary rate limit for authenticated users
You can use a personal access token to make API requests. Additionally, you can authorize a GitHub App or OAuth app, which can then make API requests on your behalf.
All these requests count towards your personal rate limit of 5,000 requests per hour. Requests made on your behalf by a GitHub App that is owned by a GitHub Enterprise Cloud organization have a higher rate limit of 15,000 requests per hour.
Primary rate limit for GITHUB_TOKEN in GitHub Actions
You can use the built-in GITHUB_TOKEN to authenticate requests in GitHub Actions workflows. For more information, see Automatic token authentication.
The rate limit for GITHUB_TOKEN is 1,000 requests per hour per repository. For requests to resources that belong to a GitHub Enterprise Cloud account, the limit is 15,000 requests per hour per repository.
Secondary rate limits
In addition to primary rate limits, GitHub enforces secondary rate limits to prevent abuse and keep the API available for all users. You may encounter a secondary rate limit in the following cases:
- Make too many concurrent requests. No more than 100 concurrent requests are allowed. This limit is shared across the REST API.
- Make too many requests to a single endpoint per minute. No more than 900 points per minute are allowed for REST API endpoints.
These secondary rate limits are subject to change without notice. You may also encounter a secondary rate limit for undisclosed reasons.
Exceeding the rate limit
If a request exceeds a secondary rate limit, the GitHub REST API will return an HTTP 403 Forbidden or 429 Too Many Requests status code, accompanied by an error message indicating that the secondary rate limit has been exceeded.
When the Retry-After response header is present, clients must not issue additional requests until the specified duration (in seconds) has elapsed. If the X-RateLimit-Remaining header has a value of 0, clients should defer further requests until the time specified in the X-RateLimit-Reset header, which represents the reset timestamp in UTC epoch seconds.
In cases where neither header is available, it is recommended to wait a minimum of 60 seconds before retrying. If requests continue to fail due to secondary rate limiting, clients should apply an exponential backoff strategy, progressively increasing the wait time between retries. After reaching a predefined maximum number of retries, the request should be aborted, and an appropriate error should be raised.
Continuing to make requests while you are rate limited may result in the banning of your integration.
Ivanti Neurons Connector Setup
-
Log in to the platform, and navigate to the Automate > Integrations page.
-
Using the search bar in the upper-right corner of the Integrations page, type GitHub to find the connector. Locate the GitHub Advance Security card under Applications and click Configuration.
-
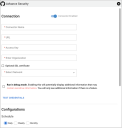
In the Advance Security window, under Connection, complete the required fields, as described below.
-
Name: The connector’s name. For example, "My GitHun Connector"
-
URL: GitHub URL, i.e., https://api.github.com
-
API Key: The API token that has access to the GitHub account
-
Organization: Your organization name in GitHub
-
Network: Ivanti Neurons ASPM network name configured to ingest the connector data.
Click the Test Credentials button to ensure the credentials are correct and have the necessary access to make GitHub account API calls.
-
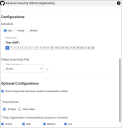
On the Advance Security GitHub window, under Oldest Scan Data Pull, configure the desired schedule for the connector to retrieve results from the GitHub account. User may specify the oldest scan data pull from the following options: 30 days, 60 days, 90 days, 6 months, or 1 year.
-
Under Repositories, select All Repo or a specific repo for which the findings need to be ingested into Ivanti Neurons.
-
Select one or more severity levels to filter the vulnerabilities to be ingested.
-
Click Save to save the connector’s configuration and create the connector. Once saved, the connector is now visible on the Integrations page under Currently Configured Integrations.
Editing a Connector Configuration
Connector configurations can be updated at any time after creation. Go to Automate > Integrations page and select the specific connector you want to update.
Data Visualization in Ivanti Neurons
The data from a GitHub is ingested into Ivanti Neurons as Applications and Application Findings. The Scanner Name associated with these scans is GITHUB. Scanner Name can be used as a filter for Applications and Application Findings.
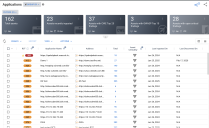
Assets
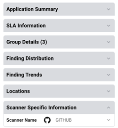
Asset data extracted from GitHub are shown on the Applications page.
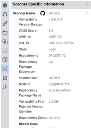
In the Application Detail pane, under the Scanner Specific Information section, the scanner is listed as GitHub.
Findings
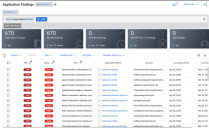
All findings from the GitHub Advance Security connector are shown on the Application Findings page.
Findings that are Fixed or Ignored will not be displayed on the Application Findings page. Details of the dependency with vulnerability can be found under Scanner specific information.