Privileges: Overview
Summary: High-level overview of the privileges available to roles in RiskSense's Identity and Access Management (IAM).
Role-based access control is designed where privileges determine what a person can do within the platform. Roles are comprised of a set of privileges. You then assign users one or more roles based on their job and scope of work. This system allows you to define what users can and cannot do within the limitations of the system (in this case, RiskSense).
Each privilege carries one or more allowances:
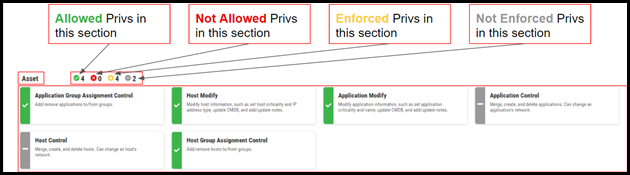
Allowed is the explicit granting of a privilege. If any one role is set to allow, the user has access to that feature or function.
Not Allowed explicitly denies access to that privilege. If any role for a user is not allowed, the user cannot make use of that feature or function. If the user is assigned multiple roles which contain both allowed and not allowed statuses for a specific privilege, the not allowed status is honored.
Enforced is a superset of both allowed and not allowed, denoting that a privilege status is explicitly affected by a given role.
Not Enforced is the other side to the enforced coin, neither allowing nor denying the privilege. If no roles granted to a user allow the privilege, it is considered an implicit denial of that privilege.
The rest of this article provides all privilege and privilege descriptions available in RiskSense’s Identity and Access Management (IAM).
API Token
-
API Token Control: Remove API Token access from other users.
Assessment
-
Assessment Upload Read: Download and view uploaded assessment files.
-
Assessment Control: Create and delete assessments.
Asset
-
Application Group Assignment Control: Add/remove applications to/from groups.
-
Host Modify: Modify host information, such as set host criticality and IP address type, update CMDB, and add/update notes.
-
Application Modify: Modify application information, such as set application criticality and name, update CMDB, and add/update notes.
-
Application Control: Merge, create, and delete applications. Can change an application's network.
-
Host Control: Merge, create, and delete hosts. Can change a host's network.
-
Host Group Assignment Control: Add/remove hosts to/from groups.
Automation
-
Automation Control: Enable/disable playbooks.
-
Automation Modify: Create and modify playbooks and rules. Allows role to run playbooks.
Client
-
Client Settings Control: Modify Client Settings.
-
Client Settings Read: View Client Settings.
Core Read
-
Core Read: All the privileges necessary for the UI to function properly.
Dashboard
-
Multi-Client Dashboard Read: View multi-client dashboard.
-
Dashboard Control: Modify and unshare other users' shared dashboards.
-
Dashboard Modify: Save and share customized dashboards.
Export
-
Export Template Modify: Save, share, and modify their own export templates.
-
Export Template Control: Save, unshare, and modify other users' shared export templates.
Filter
-
Filter Control: Save, unshare, and modify other users' shared filters.
-
Filter Modify: Save, share, and modify their own filters.
Finding
-
Finding Modify: Modify findings.
-
Finding Assignment Control: Add and remove finding assignments.
-
Finding Self Assignment Modify: Add and remove their own findings assignments.
-
Finding Control: Create and delete findings.
-
Finding SLA Control: Add and remove due dates.
Group
-
Group Control: Create, modify, and delete groups. Can view all groups regardless of their own group membership.
Identity and Access Management
-
Role Control: Create, modify, and delete roles.
Integration
-
Integration Manual Upload Control: Create/modify uploads, run URBA on assets, and run ad hoc connector jobs.
-
Integration File Read: Download files from Uploads.
-
Integration Control: Create and modify integrations.
-
Integration Upload Read: View Uploads.
Network
-
Network Control: Create, modify, and delete networks.
Scanner
-
Scanner Control: Create, modify, and delete scanners.
SLA
-
SLA Control: Create, modify, and delete SLAs.
Tag
-
Tag Control: Override tag ownership and modify other users' tags.
-
Tag Apply: Apply and unapply tags.
-
Tag Modify: Create and modify tags.
Ticket
-
Ticket Control: Create tickets for configured integrations.
User
-
User Read: View all information about users.
-
User Role Disposition Control: Assign/unassign roles to/from other users in accessible clients.
-
User Control: Create/resend welcome emails and reset two-factor authentication to email.
-
User Group Assignment Control: Assign/unassign users to/from groups they can access.
Vulnerability KB
-
Vulnerability KB Read: View Vulnerability KB. Requires purchase of module.
Workflow
-
Severity Update Modify: Approve, rework, and reject severity update requests.
-
Risk Acceptance Modify: Approve, rework, and reject risk acceptance workflows.
-
False Positive Control: Update other users' false positive workflows.
-
Risk Acceptance Request: Submit risk acceptance workflows.
-
Severity Update Request: Submit severity update workflows.
-
Remediation Request: Submit remediation workflows.
-
False Positive Request: Submit false positive workflows.
-
False Positive Modify: Approve, rework, and reject false positive workflows.
-
Severity Update Control: Update other users' severity update workflows.
-
Risk Acceptance Control: Update other users' risk acceptance workflows.
-
Remediation Control: Update other users' remediation workflows.
-
Remediation Modify: Approve, rework, and reject remediation workflows.