Tenable.io Connector Guide
Summary: How to set up and use the Tenable.io connector in Ivanti Neurons for RBVM.
Overview
The Ivanti Neurons for RBVM platform supports client connector configurations to provide a scheduled upload of the Tenable.io vulnerability data. The connector configuration page will display the details of the latest connector data pull. This connector allows customers to gain visibility into their overall risk due to vulnerabilities in their hosts and web applications and enables a more straightforward, more efficient way to manage those vulnerabilities.
Connector Configuration
Prerequisites
- Requires an active subscription to Ivanti Neurons for RBVM.
- Requires an active subscription to Tenable.io.
- URL used to access the instance of Tenable.io.
User Setup
In order to connect Ivanti Neurons for RBVM to Tenable.IO, an API user will need to be created with the following minimum access:
- Requires STANDARD [32] user role.
- Requires CAN VIEW [16] user permissions.
Connections
The following API calls are performed during a connector run to pull security vulnerabilities from Tenable.IO into Ivanti Neurons for RBVM.
|
API Type |
Endpoint |
|---|---|
|
Get All Assets |
/assets/export/ |
|
Get All Scans |
/scans/ |
|
Get All User Policies |
/policies/ |
|
Get All Policy Templates |
/editor/policy/templates |
|
Get All Vulnerabilities |
/vulns/export/ |
|
Get All Networks |
/networks |
|
Get All Tags |
/tags/values |
Platform Setup
Navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type tenable.io to find the connector.
Locate tenable.io on the page and click Configuration.
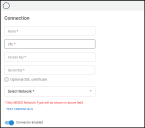
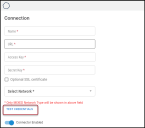
In the new window under Connection, complete the required fields, as described below.
-
Name: The connector’s name.
-
Location (URL): The URL to access the specific instance of Tenable Nessus or the Tenable.io link.
-
Access Key: Username used to access the connected system.
-
Secret Key: Password used to access the connected system.
-
Network: Network that will contain the new Tenable.io assets.
After completing the login credentials form, click the Test Credentials button.
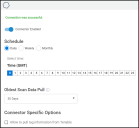
If the credentials test is successful, the Schedule connector wizard will appear.
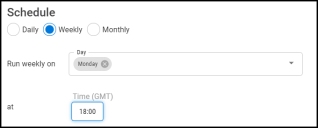
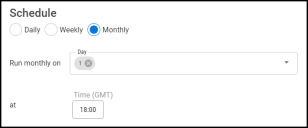
By default, the connector is enabled. The following schedules are available.
NOTE: All time selections are based on 24-hour GMT time.
Daily: Configures the connector to run at a set daily interval.
Weekly: Configures the connector to run at a set weekly interval.
Monthly: Configures the connector to run on a set date every month.
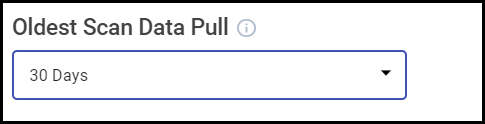
Determine the Oldest Scan Data Pull for the initial data synchronization. This can be set to pull between 30 days and 1 year. The setting will only apply for the first time the connector is run.
Optional Configurations
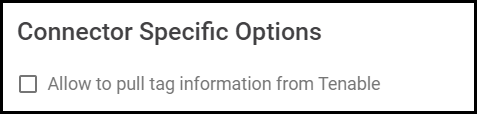
Tenable.io has its own asset tag system that can be replicated in the platform. Enable this feature under Connector Specific Options.
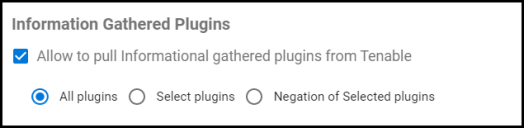
The informational plugins identified by Tenable Nessus scans may be included in the data synchronization, or users may choose to filter the input. The new connector setting for informational plugins will allow users to include or exclude specific plugins.
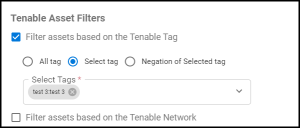
Tenable.io users may not want all the assets and findings imported to the platform. Tenable recommends that users create a user or access group for the connector that includes only the desired assets. This method of controlling information flow is preferred. The new connector also allows for filtering the inputs by tags or networks.
Click the Save button to save the configuration and view the configured connector.
Editing a Connector Configuration
Connector configurations can be updated at any time after creation. Go to the Automate > Integrations page and select the specific connector you want to update.
Utilizing the Connector
The data from Tenable.io is ingested into Ivanti Neurons as Hosts and Host Findings. The Scanner Name associated with these scans is NESSUS. Scanner Name can be used as a filter in both the Hosts and Host Findings views.
Assets
All assets from the Tenable Vulnerability Management (Formerly Tenable.io) connector are shown in the Hosts view in Ivanti Neurons.
-
Any active assets within the oldest pull date range listed in Tenable.io are shown in the Hosts view.
-
Both IP address and hostname are extracted from the Tenable.io API.
-
In the Host Detail, the Scanner is listed as NESSUS under the Sources section.
Findings
All findings from the Tenable.io scan file are shown in the Host Findings view in Ivanti Neurons for RBVM.
This connector includes several scanner-specific fields that are viewable in the detail pane, list view columns, filters, and exports:
-
Nessus CVSS v3.0 Base Score
-
Nessus CVSS v2.0 Base Score
-
Nessus MAC Addresses
-
Nessus Network Name
-
Nessus Asset Status
-
Nessus IPv4 Addresses
-
Nessus Severity ID
-
Nessus CVSS v3.0 Temporal Score
-
Nessus CVSS v2.0 Temporal Score
-
Nessus Default Severity ID
-
Nessus IPV6 Addresses
-
Nessus Hostnames
-
scannerUUID
-
Nessus Operating Systems
Severity Mapping
|
Severity |
CVSSv2 Range |
CVSSv3 Range |
|---|---|---|
|
Critical |
The plugin's highest vulnerability CVSSv2 score is 10.0. |
The plugin's highest vulnerability CVSSv3 score is between 9.0 and 10.0. |
|
High |
The plugin's highest vulnerability CVSSv2 score is between 7.0 and 9.9. |
The plugin's highest vulnerability CVSSv3 score is between 7.0 and 8.9. |
|
Medium |
The plugin's highest vulnerability CVSSv2 score is between 4.0 and 6.9. |
The plugin's highest vulnerability CVSSv3 score is between 4.0 and 6.9. |
|
Low |
The plugin's highest vulnerability CVSSv2 score is between 0.1 and 3.9. |
The plugin's highest vulnerability CVSSv3 score is between 0.1 and 3.9. |
|
Info |
The plugin's highest vulnerability CVSSv2 score is 0 or the plugin does not search for vulnerabilities. |
The plugin's highest vulnerability CVSSv3 score is 0 or the plugin does not search for vulnerabilities. |
Source: CVSS vs. VPR (Tenable Vulnerability Management)
Connector Data Mapping
This table maps the high-level fields from Tenable.io with that of the Ivanti Neurons for RBVM platform.
|
Section |
Platform Field |
Tenable.io Field |
Filter |
|---|---|---|---|
|
Hosts
|
First Discovered On |
asset.first_seen |
Yes |
|
Last Discovered On |
asset.last_seen |
Yes |
|
|
Asset Tag |
asset.tags.key:asset.tags.value |
Yes |
|
|
IP Address |
plugin.asset.ipv4 |
Yes |
|
|
HostName |
plugin.asset.hostname. |
Yes |
|
|
FQDN |
asset.FQDNs |
Yes |
|
|
Operating System -> Name |
asset.operating_systems |
Yes |
|
|
Host UUID |
asset.id |
Yes |
|
|
Nessus AWS Instance ID |
asset.aws_ec2_instance_id |
Yes |
|
|
Nessus Azure VM ID |
asset.azure_vm_id |
Yes |
|
|
Nessus CVSS v3.0 Base Score |
plugin.cvss3_base_score |
Yes |
|
|
Nessus CVSS v3.0 Temporal Score |
plugin.cvss3_temporal_score |
Yes |
|
|
Nessus CVSS v2.0 Base Score |
plugin.cvss_base_score |
Yes |
|
|
Nessus CVSS v2.0 Temporal Score |
plugin.cvss_temporal_score |
Yes |
|
|
Nessus Default Severity |
plugin.severity_default_id |
Yes |
|
|
Nessus Severity |
plugin.severity |
Yes |
|
|
Nessus VPR |
plugin.vpr.score |
Yes |
|
|
Nessus Google Cloud Instance ID |
asset.gcp_instance_id |
Yes |
|
|
Nessus Last Authenticated Scan Date |
asset.last_authenticated_scan_date |
Yes |
|
|
Nessus Network Name |
asset.network_name |
Yes |
|
|
Nessus Netbios Names |
asset.netbios_name |
Yes |
|
|
Nessus Operating Systems |
asset.operating_system |
Yes |
|
|
Nessus FQDNs |
asset.FQDNs |
Yes |
|
|
Nessus Hostnames |
asset.hostnames |
Yes |
|
|
Nessus IPV4 addresses |
asset.ipv4 |
Yes |
|
|
Nessus IPV6 addresses |
asset.ipv6 |
Yes |
|
|
Nessus Mac Addresses |
asset.macaddress |
Yes |
|
|
Host Findings
|
HostName |
asset.hostname |
Yes |
|
Nessus UUID |
asset.uuid |
Yes |
|
|
IP Address |
asset.ipv4 |
Yes |
|
|
Operating System |
asset.operating_system |
Yes |
|
|
Plugin Output |
plugin.output |
Yes |
|
|
Nessus CVSS v3.0 Base Score |
plugin.cvss3_base_score |
Yes |
|
|
Nessus CVSS v3.0 Temporal Score |
plugin.cvss3_temporal_score |
Yes |
|
|
Nessus CVSS v2.0 Base Score |
plugin.cvss_base_score |
Yes |
|
|
Nessus CVSS v2.0 Temporal Score |
plugin.cvss_temporal_score |
Yes |
|
|
Plugin Description |
plugin.description |
Yes |
|
|
Scanner plugin |
plugin.id |
Yes |
|
|
Plugin Name |
plugin.name |
Yes |
|
|
Possible Solution |
plugin.solution |
Yes |
|
|
Plugin Output |
plugin.synopsis |
Yes |
|
|
Port |
plugin.port.port |
Yes |
|
|
Service |
plugin.port.protocol |
Yes |
|
|
Scanner Reported Severity |
plugin.severity |
Yes |
|
|
Nessus Default Severity |
plugin.severity_default_id |
Yes |
|
|
First Discovered on |
plugin.first_found |
Yes |
|
|
Last Discovered on |
plugin.last_found |
Yes |
|
|
Source Status |
plugin.state |
Yes |
|
|
Nessus Reason Recast |
plugin.recast_reason |
No |
|
|
Nessus Reason Accepted |
plugin.recast_reason |
No |
|
|
Suppression Value |
plugin.severity_modification_type |
Yes |