WIZ Connector User Guide
Overview
WIZ serves as a unified platform for cloud security, offering enhanced capabilities for both security and development teams. It provides comprehensive visibility, context, and risk prioritization across the entire development lifecycle.
Ivanti Neurons for RBVM and ASPM provides an API-based connector that integrates with WIZ, enabling customers to bring in their findings. It allows customers to gain visibility into their overall risk due to vulnerabilities in their endpoint and a more straightforward, efficient way to manage those vulnerabilities.
Connector Configuration
Prerequisites
- Requires an active subscription to Ivanti Neurons for RBVM / ASPM.
- Requires an active subscription to WIZ with API access.
User Setup
Ivanti Neurons requires a user account with the following access to communicate with and pull data from WIZ
- Read access to the assets and their associated issues.
- API access.
Roles and Permissions
The user should have the following roles for this integration
- read:vulnerabilities
- read: issues
- read:cloud_configuration
- read: inventory
- read:resources
Platform Setup
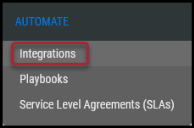
Navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type WIZ to find the connector.
Locate the WIZ card on the page and click Configuration. The connector card appears in both the Network and Application sections.
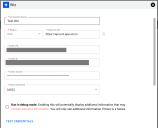
Complete the required fields in the new window under Connection as described below.
- Name: The connector’s name.
- Region / Region URL: Select your region. You can also select “Private Platform” and enter the URL manually.
- Auth URL: The authorization URL
- Client ID: The username of the instance.
- Client Secret: The password of the instance.
- SSL: Optional instance SSL certificate in base64 format.
Click the Test Credentials button to ensure the credentials are correct and have the necessary access to make API calls.
Under Schedule, configure the desired schedule for the connector to retrieve results from the WIZ instance.
If platform successfully makes a connection with the given credentials, you can also fill out the Optional Configurations section.
In the first section, you can choose to automatically closed findings that WIZ has marked as “suppressed.” You can also enable auto URBA (Update Remediation by Assessment).
Connector Specific Options:
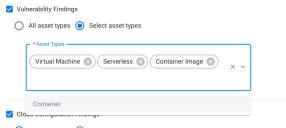
Depending on the findings you have in WIZ, you can configure the connector to ingest certain types. The available categories include Issues, Vulnerability, and Cloud Configuration findings. For Vulnerability findings, you can select between
- Virtual Machine
- Serverless
- Container
- Container Image
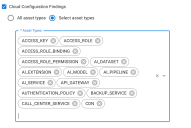
For Cloud Configuration findings, you can choose between many different types of assets. The image below shows some of them.
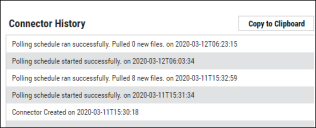
When the connector is set up, a new entry for it appears at the top of the Integrations page. This connector runs once the initial setup is complete. Check the connector’s status by clicking the History button.
Editing a Connector Configuration
Connector configurations can be updated at any time after creation. Go to Automate > Integrations and select the specific connector you want to update.
Utilizing the Connector
The data from WIZ is ingested into Ivanti Neurons for ASPM as applications and application findings or RBVM as hosts and host findings depending on the asset type. “Issues” and “Cloud Configuration Findings” appear on the Host Findings page. Vulnerabilities for the “Virtual Machines” and “Serverless” asset types also become host findings. On the other hand, vulnerabilities for “Container” and “Container Image” assets will show up on the application findings page.
For host findings, host findings appear under the scanner name “WIZHOST”. For application findings, findings appear under the scanner name “WIZAPP”.
Connector Data Mapping
This section shows how various RBVM/ASPM fields map to the corresponding fields in the WIZ APIs. If a field lacks a direct corresponding match in RBVM or ASPM, then the field often becomes a scanner-specific field. This section also lists scanner-specific fields that RBVM/ASPM ingest from WIZ.
Host Fields
|
RBVM Field |
Issues Mapping |
Vulnerability Mapping |
Cloud Configuration Mapping |
|---|---|---|---|
|
Hostname |
issues->nodes->entitySnapshot -> name |
vulnerabilityFindings->nodes->vulnerableAsset -> name |
configurationFindings->nodes->resource -> name |
|
IP Address |
N/A |
vulnerabilityFindings->nodes->vulnerableAsset -> IpAddresses |
N/A |
|
Operating System |
N/A |
vulnerabilityFindings->nodes->vulnerableAsset -> operatingSystem |
N/A |
|
Type |
issues->nodes->entitySnapshot -> type |
VIRTUAL_MACHINE (Single value injected; no mapping) |
VOLUME (Single value injected; no mapping) |
|
Tags |
issues->nodes->entitySnapshot -> tags |
vulnerabilityFindings->nodes->vulnerableAsset -> tags |
configurationFindings->nodes->resource -> tags |
Host Scanner-Specific Fields
|
Scanner-Specific Field |
Issues |
Vulnerabilities |
Cloud Configuration |
|---|---|---|---|
|
WIZ Host Asset ID |
X |
||
|
WIZ Host Asset Name |
X |
||
|
WIZ Host Asset Region |
X |
X |
X |
|
WIZ Host Asset Status |
X |
X |
X |
|
WIZ Host Business Impact |
X |
X |
X |
|
WIZ Host Business Unit |
X |
X |
X |
|
WIZ Host Cloud Platform |
X |
X |
|
|
WIZ Host Cloud Provider |
? |
? |
|
|
WIZ Host Cloud Provider URL |
X |
X |
|
|
WIZ Host EntitySnapshot ID |
X |
||
|
WIZ Host EntitySnapshot Name |
X |
||
|
WIZ Host External ID |
X |
||
|
WIZ Host Native Type |
X |
X |
|
|
WIZ Host Projects |
X |
X |
|
|
WIZ Host Provider ID |
X |
X |
|
|
WIZ Host Provider Unique ID |
X |
||
|
WIZ Host Resource Group External ID |
X |
||
|
WIZ Host Resource Group ID |
X |
||
|
WIZ Host Resource Name |
X |
||
|
WIZ Host Runtime |
X |
||
|
WIZ Host Subscription ID |
X |
X |
|
|
WIZ Host Subscription External ID |
X |
X |
X |
|
WIZ Host Subscription Name |
X |
X |
X |
|
WIZ Host Subscription Tags |
X |
||
|
WIZ Host Projects |
X |
Application Fields
|
ASPM Field |
Vulnerability JSON Mapping |
|---|---|
|
Name |
vulnerabilityFindings->nodes->vulnerableAsset -> name |
|
Address |
vulnerabilityFindings->nodes->vulnerableAsset -> imageId (for container images) vulnerabilityFindings->nodes->vulnerableAsset -> ImageExternalId (for container) |
|
Type |
vulnerabilityFindings->nodes->vulnerableAsset -> type |
|
Tags |
vulnerabilityFindings->nodes->vulnerableAsset -> tags |
Application Scanner-Specific Fields
- WIZ App Asset ID
- WIZ App Asset Identified By
- WIZ App Asset Identifier
- WIZ App Asset Name
- WIZ App Asset Region
- WIZ App Asset Status
- WIZ App Business Impacts
- WIZ App Business Units
- WIZ App Cloud Platform
- WIZ App Cloud Provider URL
- WIZ App Image External ID
- WIZ App Image ID
- WIZ APP Internet Exposure
- WIZ App Node Name
- WIZ App Pod Name
- WIZ App Pod Namespace
- WIZ App Projects
- WIZ App Provider Unique ID
- WIZ App Serverless Container
- WIZ App Subscription External ID
- WIZ App Subscription ID
- WIZ APP Subscription Name
- WIZ App Type
- WIZ App VM External ID
- WIZ App Wide Internet Exposure
Host Findings Fields
| RBVM Field | Issue JSON Mapping | Vulnerability JSON Mapping | Cloud Configuration JSON Mapping |
|---|---|---|---|
|
Scanner Plugin |
issues->nodes->control-> id |
vulnerabilityFindings->nodes->name |
configurationFindings->nodes->rule-> id |
|
Scanner Reported Severity |
issues->nodes->severity |
vulnerabilityFindings->nodes->score |
configurationFindings->nodes->severity |
|
Severity |
issues->nodes->severity |
vulnerabilityFindings->nodes->CVSSSeverity |
configurationFindings->nodes->severity |
|
Title |
issues->nodes->control-> name |
vulnerabilityFindings->nodes->name |
configurationFindings->nodes->rule-> name |
|
Description |
issues->nodes->sourceRule-> controlDescription |
vulnerabilityFindings->nodes->CVEDescription |
configurationFindings->nodes->rule-> description |
|
First Discovered on |
issues->nodes->createdAt |
vulnerabilityFindings->nodes->firstDetectedAt |
configurationFindings->nodes->firstSeenAt |
|
Last Discovered On |
issues->nodes->updatedAt |
vulnerabilityFindings->nodes->lastDetectedAt |
|
|
Possible Solution |
issues->nodes->sourceRule-> resolutionRecommendation |
vulnerabilityFindings->nodes->remediation |
configurationFindings->nodes-> remediation |
Host Finding Scanner-Specific Fields
|
RBVM Field |
Issues |
Vulnerabilities |
Cloud Configuration |
|---|---|---|---|
|
WIZ URL |
|
X |
|
|
WIZ Host Control ID |
X |
|
|
|
WIZ Host Detail Description |
|
X |
|
|
WIZ Host Detailed Name |
|
X |
|
|
WIZ Host Detection Method |
|
X |
|
|
WIZ Host Exploitability Score |
|
X |
|
|
WIZ Host Finding Status |
|
X |
|
|
WIZ Host Fixed Version |
|
X |
|
|
WIZ Host Has CISA KEV Exploit |
|
X |
|
|
WIZ Host Has Exploit |
|
X |
|
|
WIZ Host Impact Score |
|
X |
|
|
WIZ Host Link |
|
X |
|
|
WIZ Host Location Path |
|
X |
|
|
WIZ Host Node ID |
X |
X |
X |
|
WIZ Host Projects |
|
X |
X |
|
WIZ Host Resolution Reason |
|
X |
|
|
WIZ Host Result |
|
|
X |
|
WIZ Host Rule Description |
|
|
X |
|
WIZ Host Rule Function as Control |
|
|
X |
|
WIZ Host Rule Graph ID |
|
|
X |
|
WIZ Host Rule ID |
|
|
X |
|
WIZ Host Rule Name |
|
|
X |
|
WIZ Host Rule Remediation Instructions |
|
|
X |
|
WIZ Host Security Sub Category |
X |
|
X |
|
WIZ Host Security Sub Category Title |
X |
|
|
|
WIZ Host Type Name |
X |
|
X |
|
WIZ Host Projects |
X |
|
X |
|
WIZ Host Vendor Severity |
|
X |
|
|
WIZ Host Version |
|
X |
|
Application Finding Fields
|
ASPM Field |
Vulnerability JSON Mapping |
|---|---|
|
Scanner Plugin |
vulnerabilityFindings->nodes->id |
|
Scanner Reported Severity |
vulnerabilityFindings->nodes->score |
|
Location |
vulnerabilityFindings->nodes->portalUrl |
|
Severity |
vulnerabilityFindings->nodes->CVSSSeverity |
|
Title |
vulnerabilityFindings->nodes->name |
|
Description |
vulnerabilityFindings->nodes->CVEDescription |
|
First Discovered on |
vulnerabilityFindings->nodes->firstDetectedAt |
|
Last Discovered On |
vulnerabilityFindings->nodes->lastDetectedAt |
|
CVE |
vulnerabilityFindings->nodes->name |
|
Finding Type |
Vulnerability |
|
Possible Solution |
vulnerabilityFindings->nodes->remediation |
Application Finding Scanner-Specific Fields
- Wiz App Detail Description
- WIZ App Detailed Name
- WIZ Detection Method
- WIZ App Exploitability Score
- WIZ App Finding Type
- WIZ App Fixed Version
- WIZ App Has CISA KEV Exploit
- Wiz App Has Exploit
- WIZ App Impact Score
- WIZ App Link
- WIZ App Location Path
- WIZ App Projects
- WIZ App Resolution Reason
- WIZ App Vendor Severity
- WIZ App Version
- WIZ URL