This is not the latest version of Identity Director documentation.View available documentation.
Configure Password Reset
At Setup > Login Page Services > Password Reset, enable users to reset their Active Directory password. This reduces the number of help desk password tickets and enhances productivity of the user. Users can reset their Active Directory password from the Microsoft Windows logon screen, or from the Identity Director Web Portal or Mobile client logon page, either via a wizard or via service delivery.
- You can add code validation to password resets. This adds an extra check to authenticate the identity of the user who requests a password reset: a verification code is sent to the user e.g. by SMS or e-mail. Users then need to provide this verification code before they can proceed with a password reset. This ensures that passwords are reset as secure as possible.
- Using organizational context, you can define to whom the Verification Code and/or Security Questions apply.
- You can configure password complexity policies based on regular expressions, to ensure that passwords provided by your users meet the complexity requirements of your organization.
- You can add translations for the labels and messages that appear to end users in the Web Portal.
- The availability of this functionality may be subject to the license type used in your environment.
- See Ivanti Identity Director Password Reset Guide for more information and scenarios.
Configuration
|
Field |
Explanation and Tips |
|---|---|
|
Password reset settings |
Specify the availability of the password reset functionality.
Windows 10 users will only be able to access the Password Reset button from the logon screen, and not from the lock screen.
|
|
Reset link text |
Specify the text of the password reset link. |
|
People identifier |
Specify the identification method of users when they request a password reset. |
|
Service |
Specify the service that is delivered as part of the password reset (for example, the service Reset password based on user input that is provided with the Identity Director Password Reset Guide). |
|
User instructions |
Specify instructions when users click the password rest link. |
|
Status page message |
Specify status information. |
|
Redirection URL |
Specify a URL of choice after a password reset, rather than the default Web Portal sign-in page. In certain scenarios, for example when users access the Web Portal from a thin client, redirecting them to the default page may not be user-friendly. You can prevent this by specifying a different URL. |
|
Display the Finish button |
Specify if you want the Finish button to be displayed at the end of the process. By default, this button will take users to the Web Portal login screen. If you do not display the Finish button, no redirection (to the Web Portal login page or the Redirection URL) will occur. |
|
Password input |
Specify if password input is provided through the wizard or through a service workflow. If you allow users to reset their password through a wizard, do not configure Active Directory to require a password change on next logon. This may lead to situations in which users can no longer sign in. |
|
Password attribute |
Specify the service attribute that can store the password that the user provides.
|
|
Select organizational context |
Specify the Organization(s) or Organizational attribute(s) that determine if the Verification Code applies to a user.
|
|
Organizational context diagnostics |
After you specify organizational context, the first (max) 100 people that meet the conditions are listed here. |
|
Generating verification code message |
Specify status information that is displayed to the user about generation of the code. |
|
Enter verification code message |
Specify user instructions to validate the code.
|
|
Invalid verification code message |
Specify the message that is that is displayed to the user if the provided code is incorrect. |
|
Exceeding maximum number of attempts message |
Specify the message that is that is displayed to the user when he exceeds the limit. This field is only available if you have selected the option Limit number of attempts. |
|
Validating verification code message |
Specify status information about validation of the code. |
|
Field |
Explanation and Tips |
|---|---|
|
Enabled |
Enable the Security Questions method for user validation |
|
Number of security questions |
Specify the number of questions in the wizard. If this number exceeds the number of questions and answers stored in a user's Security Questions and Answers attribute (see below), the user will get an error and cannot complete the Password Reset service. |
|
Questions attribute |
This field shows the default people attribute Security Questions and Answers that stores the security questions and answers of the wizard. The attribute can be filled using the User Validation Service you specify on the Login Page Services page.
|
|
Attempts to answer before lockout |
The number of permitted attempts to answer the questions correctly before the account gets locked out. By default, this value will be 0 (=no limit) and the options Lockout time in minutes and Cool down time in minutes will be grayed out.
The maximum number of attempts will be reached when the user:
(other combinations are possible) |
|
Lockout time in minutes |
Specify the times (in minutes) that the account will be locked out after reaching the configured number of Attempts to answer before lockout. During this time, the respective account will not be able to try again to reset the password. If the Attempts to answer before lockout is set to 0, this field will be grayed out. |
|
Cool down time in minutes |
Specify the time (in minutes) after which the lockout counter is reset. After this cool down time has expired, the counter for Attempts to answer before lockout is reset and the next incorrect answer to a security question is considered to be the first attempt again. |
|
Exceeding the maximum number of attempts message |
Specify the message that is displayed to the end user when the maximum number of attempts has been reached. You can use parameters to include the number of minutes the account lockout is in effect. Example: You can start again in {0} minutes. |
|
Select organizational context |
Specify the Organization(s) or Organizational attribute(s) conditions that determine if the Security Questions apply to a user.
|
|
Organizational context diagnostics |
After you specify organizational context, the first (max) 100 people that meet the conditions are listed here. |
Identity Director can keep track of the password history, to manage password reuse. The history itself is contained within Identity Director and does not come from integrations with various providers, such as Microsoft AD, Okta, etc.
|
Field |
Explanation and Tips |
|---|---|
|
Enabled |
Enable password history option. |
|
Number of passwords remembered |
Specify the number of passwords that will be stored in Identity Director, to check that users don’t reuse their old passwords. The history is designed to be populated by the passwords set by users. If the password is changed manually from AD, or if the option Provided through service workflow is used as a reset method, Identity Director has no way of knowing about the values used as a part of those operations. Best practices dictate using only Identity Director & user input as a method for choosing the password for best results. In case the password has been reset by another method, this feature will look also at the login events. |
|
Password reused message |
Specify the message that will be displayed to the end user when an old password is reused. You can use parameters to include the number of old passwords that cannot be reused. |
|
Select organizational context |
Specify the Organization(s) or Organizational attribute(s) that determine if the Password History applies to a user.
When an Organization or Organizational attribute is specified here, all the users who match the conditions are subject to collecting their password and enforcing the history. |
|
Organizational context diagnostics |
After you specify organizational context, the first (max) 100 people that meet the conditions are listed here. |
|
Field |
Explanation and Tips |
|---|---|
| Diagnostics
(Organizational picker) |
Add an organization to load its active profiles and to test the configured password complexity rules. |
| Active Profiles | After the organization context has been set, this will display the profiles that apply for that organization. |
| Test Your Password | Insert the desired password to test out the rules. As each one of the rules is fulfilled, the check mark next to it will change color. This allows you to test out in real time the validity of the password policy for a given organization inside you company before saving the configuration. |
| Add complexity profile |
Click this button to add a new profile with its own password complexity policy.
In this case John, will have to specify a password that consists of 12 digits and a special character. |
|
Regular expression |
Same as above. |
|
Password complexity hints |
Same as above. |
|
Add Organization |
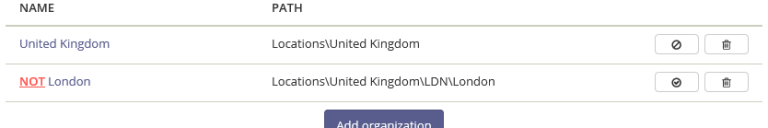
Specify the Organization(s) that determine if the Complexity Profile applies to a user. This is a mandatory field. However, a profile without rules can be added.
Example: A profile with the configuration as shown above:
By default, with this configuration, the Default Password Complexity Profile applies to that last group of users. |
Behavior and details
- You can add as many rules per complexity profile as you want, including for the Default Password Complexity Profile.
The resulting rules make up the final policy and all of them must apply to the new password the user will set.
Please note, that using too many complexity rules may affect the user experience. - You can add as many complexity profiles as you want.
- No organizational context can be added for the Default Password Complexity Profile.
- You can also use the regular expressions to define dictionaries of certain words that you do not allow for password usage such as “Password” or the user’s employee ID number.
If you have enabled translations at Setup > Translations, you can add translations for the labels and messages that appear to end users in the Web Portal for password reset.
To add translations:
- Alongside the default language, click
 to export its RESX to use as the basis of translations for the other supported languages.
to export its RESX to use as the basis of translations for the other supported languages.
The name of this file is passwordresetsettings.resx. - Save a renamed copy of this file and translate it as required.
- Click
 to import the RESX of the language.
to import the RESX of the language.
This ensures that custom labels are translated in the correct language.
Each supported language uses the default language if you do not upload a RESX file.
Click ![]() to reapply the default language.
to reapply the default language.
Click ![]() to export the RESX of the language to make adjustments to the translation.
to export the RESX of the language to make adjustments to the translation.