This is not the latest version of Identity Director documentation.View available documentation.
Configure permissions for Administrative Roles
In the Management Portal at Setup > Administrative Roles, prevent unauthorized access to the Management Portal and Setup and Sync Tool.
On the Administrative Roles tab, click an administrative role to configure its permissions. This determines what the login account to which it is assigned is allowed to do.
| Permissions | Explanation and Tips |
|---|---|
|
|
Select Deny to hide the item. By default, the access permissions of a new administrative role are set to Deny. |
|
|
Select Read to set read-only access (available for services, people, organizational context and data connections). |
|
|
Select Modify to grant full access. |
|
|
Select Inherit (blank) to let items inherit the access permissions of their parent (available for data connections, organizational context and services). |
Please note, that the permissions of the default administrative role Full Access cannot be changed.
- The Building Block functionality is only available if your login account has been assigned the Full Access role. Other administrative roles, including ones that grant Modify access to all functionality, do not grant access to the Building Block functionality.
- Similarly, you can only synchronize data connections via a command line if your login account has been assigned the Full Access role.
Access to restricted information
With the item  Attribute Value Visibility, you can specify permissions to view Restricted information in text and table service attributes, text and table people attributes and people identifiers, including any related placeholders.
Attribute Value Visibility, you can specify permissions to view Restricted information in text and table service attributes, text and table people attributes and people identifiers, including any related placeholders.
This ensures you can be compliant with the privacy laws of your country or organization, as you can limit access to private information like e-mail addresses, phone numbers, social security numbers, etc.
If an administrative role has permission for the item  Attribute Value Visibility set to:
Attribute Value Visibility set to:
- Modify, administrators with that role see the icon
 for restricted attributes and their placeholders. They can click this icon to view their value. These values are hidden again when the page is refreshed. This prevents situations in which others can view restricted information by shoulder surfing these administrators. Where appropriate, a button is available to view ALL restricted attributes in a section at once.
for restricted attributes and their placeholders. They can click this icon to view their value. These values are hidden again when the page is refreshed. This prevents situations in which others can view restricted information by shoulder surfing these administrators. Where appropriate, a button is available to view ALL restricted attributes in a section at once. - Deny, administrators with that role see the icon
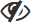 for restricted attributes and their placeholders. At Transactions, restricted attributes are shown as [attributename]. Although these administrators cannot see the value of the attribute, this still allows them to verify if the context or definition of the attribute is correct.
for restricted attributes and their placeholders. At Transactions, restricted attributes are shown as [attributename]. Although these administrators cannot see the value of the attribute, this still allows them to verify if the context or definition of the attribute is correct.
This functionality applies to the Management Portal only; restricted information is still shown in the Web Portal.
 Attribute Value Visibility does not influence:
Attribute Value Visibility does not influence:
- the ability to modify restricted data
- the ability to change restricted data to unrestricted data
Multiple administrative roles
If you assign multiple administrative roles to a login account, the permissions of all roles are combined, in which the least restrictive permissions apply:
- Modify takes precedence over Read and Deny
- Read takes precedence over Deny
- Administrative role 1 has Deny permissions on a specific service A.
- In administrative role 2, service A inherits Modify permissions from the service category.
Result: A login account that is assigned both administrative roles 1 and 2 gets Modify permissions on service A.
- Administrative role 1 has Modify permissions on the Entitlement Catalog page.
- Administrative role 2 has Read permissions on the Entitlement Catalog page.
Result: A login account with roles 1 and 2 gets Modify permissions on the Entitlement Catalog page.