Signing Scripts
A script must be signed by an authority trusted by the console in order to be imported or executed by Security Controls. All scripts provided with Security Controls are signed by Ivanti. During the installation of Security Controls, the Ivanti certificate is added to the trusted certificate store on the console machine.
You must sign scripts that you create before importing them into Security Controls. To do this, you need a signing certificate. That certificate must be issued by an authority that is in the trust list for the console(s) that are going to execute the scripts you create.
This section will describe one way to create a signing certificate and add it to the trusted certificates on the console.
Creating a Root Certificate Capable of Issuing a Code Signing Certificate
This step requires the use of Windows 10 or Windows Server 2016 or later.
To create a new root certificate capable of issuing a code signing certificate, use the following command.
PS C:\> $signerRoot = New-SelfSignedCertificate -Subject "CN=PowerShell Local Certificate Root2" -HashAlgorithm Sha256 -CertStoreLocation Cert:\LocalMachine\My -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.3") -KeyUsageProperty None -KeyUsage None
Creating a Signing Certificate
This step requires the use of Windows 10 or Windows Server 2016 or later.
The next step is to create a signing certificate that is issued by the root certificate. To do so, enter the following at the command prompt:
PS C:\> $powershellSignerSigner = New-SelfSignedCertificate -Subject "CN=PowerShell User" -HashAlgorithm Sha256 -CertStoreLocation Cert:\LocalMachine\My -Signer $signerRoot -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.3") -KeyUsageProperty None -KeyUsage None
Verifying the Signing Certificate
You can verify the certificate from within PowerShell by entering the following command:
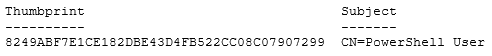
Get-ChildItem cert:\LocalMachine\My -codesigning | Where-Object {$_.Subject -match "CN=PowerShell User"}
If the certificate is found, it will display the thumbprint and subject of the certificate, similar to this:
Move the Signing Certificate to the Trusted Root Certificate Store
You must move the signing certificate from the "My" certificate store into the trusted "Root" certificate store. This builds up the chain of trust to the root store.
PS C:\> Move-Item -Path "Cert:\LocalMachine\My\$($signerRoot.Thumbprint)" -Destination Cert:\LocalMachine\Root
Signing a Script
This section will describe how to sign a script file from a PowerShell prompt or within the PowerShell ISE.
From the PowerShell command prompt, change to the directory containing your script file. In this example, it is named test-script.ps1. Then enter the following two commands:
The first command should be entered on a single line. The CN=PowerShell User should match the name you specified when creating the signing certificate.
$cert = @(Get-ChildItem cert:\LocalMachine\My -codesigning | Where-Object {$_.Subject -match "CN=PowerShell User"})[0]
Set-AuthenticodeSignature .\test-script.ps1 $cert
The first command will locate the certificate in the certificate store. The second command signs the script using that certificate.
Signing the script will add a block at the end of the script that looks similar to this:
# SIG # Begin signature block
# MIIEMwYJKoZIhvcNAQcCoIIEJDCCBCACAQExCzAJBgUrDgMCGgUAMGkGCisGAQQB
# gjcCAQSgWzBZMDQGCisGAQQBgjcCAR4wJgIDAQAABBAfzDtgWUsITrck0sYpfvNR
# AgEAAgEAAgEAAgEAAgEAMCEwCQYFKw4DAhoFAAQU4QyppfQY+5HviH7wuIBvvmRf
……
# SIG # End signature block
If you make any changes to the script, you will need to re-sign it.
Signing a Script Using a PFX File
If you’d like to sign scripts using the same signing certificate on multiple machines without installing the signing certificate on each machine, you can use a PFX (Personal Information Exchange) file.
To create a PFX file:
1.Run CertMgr.exe.
2.On the Personal tab, select the signing certificate.
3.Click Export.
4.On the first export wizard screen, click Next.
5.Select the Personal Information Exchange option.
If there is an Enable strong protection option, choose it.
6.Enter a password when prompted.
This will be required when using this pfx file to sign scripts.
7.When prompted, type a name for the pfx file.
To sign a script using the PFX file, enter the following commands in PowerShell:
$cert = Get-PfxCertificate mycert.pfx
Set-AuthenticodeSignature .\test-script.ps1 $cert
When prompted, supply the password you created in Step 6.