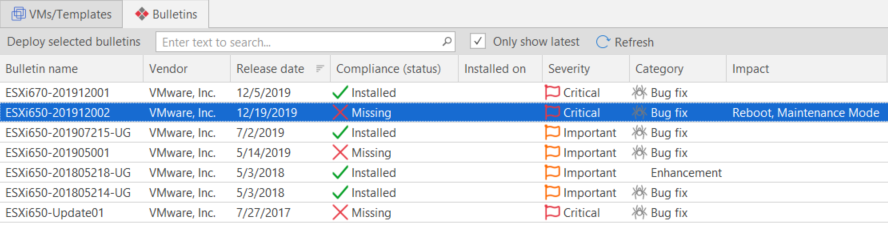
Viewing Bulletin Status
The Bulletins tab displays the status of the security bulletins that have been issued for the ESXi hypervisor(s) selected in the top pane. If multiple hypervisors are selected in the top pane, this tab will display bulletin information for all selected hypervisors.
A bulletin that is scheduled for deployment is considered to be still missing. This status will change after the bulletin is successfully installed and the screen is refreshed.
You can export the bulletins by right-clicking the list, then clicking Export bulletins to CSV.
You can customize the way information is displayed within this tab. See Customizing the Column Headers for information.
|
Field |
Description |
|---|---|
|
Deploy selected bulletins |
|
|
Search |
Enables you to search for bulletins contained on the tab. To initiate a search you simply type the search criteria in the Search box. Only those bulletins that match the search criteria are displayed; all other bulletins are hidden.
|
|
Only show latest |
If enabled, filters the contents of the tab so that the only bulletins displayed are those that are not replaced by newer bulletins. Use this check box to identify the vulnerabilities that have not yet been addressed. |
|
Refresh |
Updates the bulletin information that is displayed on the tab. |
|
ESXi Hypervisor |
The name or IP address of the ESXi hypervisor. |
|
Bulletin Name |
The bulletin name. |
|
Vendor |
Identifies the name of the vendor that released the bulletin. |
|
Release Date |
The original publication date of the bulletin that corrects this vulnerability. |
|
Compliance (Status) |
Indicates the bulletin status at the time the scan was performed. |
|
Installed On |
Shows the date and time that the bulletin was installed. This information will not be available if the bulletin was installed using a different Security Controls database or if the bulletin was not installed by Security Controls. |
|
Installed By |
Shows the name of the user who installed the bulletin. This information will not be available if the bulletin was installed using a different Security Controls database or if the bulletin was not installed by Security Controls. |
|
Severity |
Indicates the severity level of the vulnerability that is corrected by this bulletin. The severity level can be one of the following:
|
|
Category |
The bulletin category can be one of the following:
|
|
Impact |
Indicates the impact that applying the bulletin will have on the virtual machine and hypervisor. |
|
Replaced By |
The bulletin that contains a more recent update for the vulnerability. |
|
Summary |
Provides a short description of the bulletin. |