Performing an Asset Scan
The asset inventory function enables you to track your software and hardware assets. Performing an asset scan enables you to thoroughly and dynamically discover and catalog your IT assets. You will uncover software applications you didn’t know were installed and discover physical machines you didn’t even know you had. By eliminating these blind spots, you can quickly close the gaps in your security and policy compliance.
Do you want more detailed information? See the Asset Inventory Overview topic in the Security Controls Help.
Try it yourself
- Select New > Agentless Operation.
- In the Select/confirm targets area, select My Machine.
- Select the Asset inventory tab.
- In the Select an asset template box, verify that Full Asset Scan is selected.
- In the Select a schedule area, verify that Now is selected.
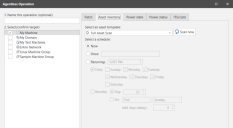
- Click Scan now.
- When the scan is complete, click Close (scan complete).
The scan is performed using the credentials of the currently logged on user. Valid credentials must be specified when performing scans on other machines.
The Operations Monitor dialog shows the status of the asset scan.
Your next step
Go to Machine View and view the asset scan results.
Do you want to perform a more thorough scan?
Scanning just the console machine provides a quick and easy introduction to the asset inventory feature. If you prefer a more realistic demonstration, however, feel free to create a machine group and perform an asset scan of multiple machines in your network. For more information, see Creating Machine Groups in the Security Controls Help.
Scanning many machines at once will obviously take much longer to perform than scanning just a single machine. It might be best to do this after you have completed your first pass through this evaluation guide.