Application Control Configuration Settings
You configure the Application Control functionality within the Application Control Configuration Editor. This can be accessed from one of a few places within the Security Controls console.
- New >Application Control Configuration
- Application Control configurations right-click New Application Control Configuration
- New > Agent Policy > Application Control > New.
Note this will assign the configuration to the policy once saved.
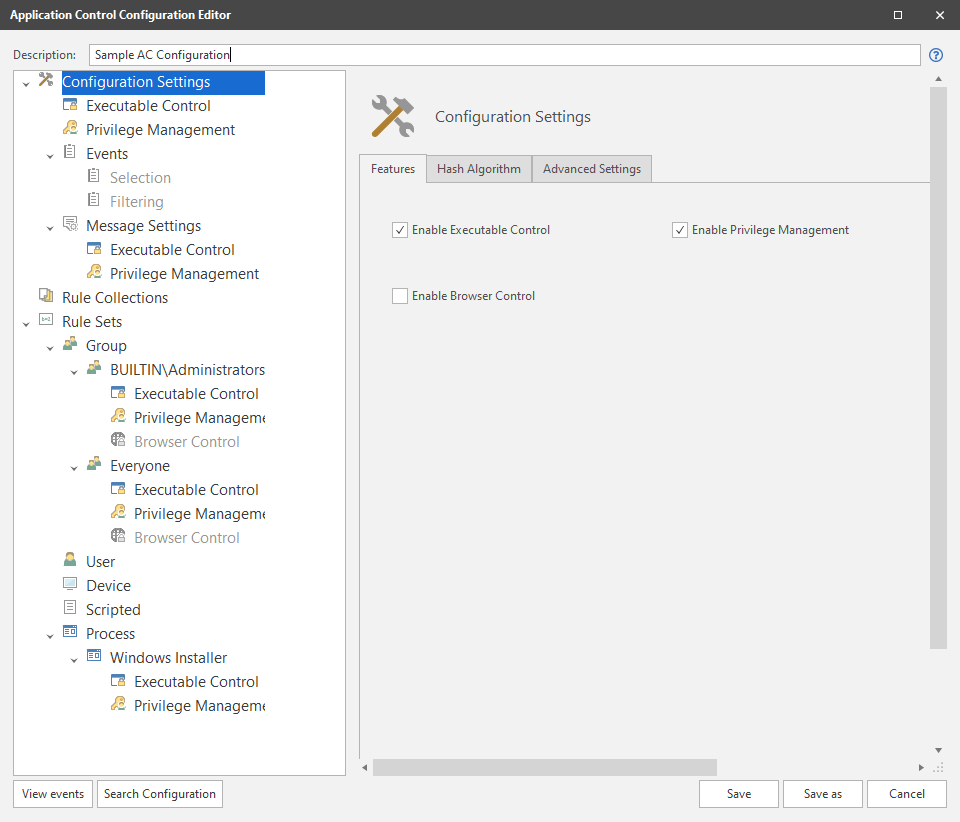
The top level node Configuration Settings has three tabs:
Features
Select to enable the following Application Control functionality for this configuration:
Executable Control
Executable Control covers the following functionality throughout the configuration:
- Trusted Ownership - during the rule process trusted ownership checking is performed on files and folders to ensure that ownership of the items is matched with the list of specified trusted owners specified in the configuration.
- Security levels - specify the levels of restrictions to execute unauthorized files.
- Allowed and Denied Items - grant or deny access to specific items applicable to a rule set.
Privilege Management
Privilege Management allows you to create reusable privilege management policies which can be associated with any rule sets and can elevate or restrict access to files, folders, drives, file hashes, and Control Panel components. A more granular level of control allows you to assign specific privileges for debugging or installing software, or to set integrity levels for managing interoperability between different products, such as Microsoft Outlook and Microsoft Word.
Privilege Management contains four primary functions:
- Elevating privilege management for applications.
- Elevating privilege management for Control Panel components and Management Snapins.
- Reducing privilege management for applications.
- Reducing privilege management for Control Panel components and Management Snapins.
Browser Control
Use this feature to automatically redirect users when they attempt to access a specified URL. By defining a list of prohibited URLs, you redirect any user attempting to access a listed URL to a default warning page or a custom web page. You can also select to allow certain URLs which, when used in conjunction with redirects, gives you further flexibility and control and lets you create an allows list of websites.
Before you configure this feature for Internet Explorer, you must enable third-party browser extensions using Internet Options for each of your endpoints. Alternatively, this can be applied via Group Policy.
URL Redirection is compatible with Internet Explorer 8, 9, 10, and 11. When using Chrome, all managed endpoints must be part of a domain.
Hash Algorithm
File Hash provides a means to accurately identify a file according to the actual contents of the file itself. Each file is examined and according to its contents, a digital hash, which may be likened to a fingerprint, is produced. Application Control makes use of the industry standard SHA-1, SHA-256 and Adler-32 hashes. If the file is altered in any way, then the hash is also altered.
Digital hashing is seen as the ultimate security method because it is accurate. It identifies each file independently of all other factors other than the file itself. For example, an administrator takes a digital hash of all executables on a computer system and records them. A user then tries to execute an application. The digital hash of the application is calculated and then compared to the recorded values. If there is a match the application is granted execution, otherwise it is denied. This methodology also provides zero-day protection because not only does it stop new applications from being introduced, it also blocks any applications that have been infected with malware.
Although file hashing provides a similar protection to Trusted Ownership, you must also consider the time and management involved with respect to maintaining the security systems in place. Applications are constantly being updated with product levels, bug fixes, and vulnerability patches. This means that all associated files are also constantly being updated. So if, for example, a product level is applied to Microsoft Office then for the updated parts to work new digital hashes of the updated files must now be taken. Take care to ensure that these are available when the update is available to eliminate downtime. Additionally, it is recommended that you remove the old hash.
Advanced Settings
Advanced Settings allow you to configure additional settings which will be applied on managed endpoints when an Application Control configuration is deployed. If a new configuration is deployed that contains new advanced settings, any pre-existing advanced settings in place on the end point will be deleted.
On the Advanced Setting tab, right-click in the work area and select Add to display the list of available Advanced Settings. The settings are applied when the configuration is deployed to your managed endpoints.
| Setting | Data Type | Description |
|---|---|---|
| ADComputerGroupMembershipTimeoutSecs | Numeric | Timeout, in seconds, for nested computer group lookups. The default setting is 120 seconds and setting this value to 0 disables the timeout. |
| ADQueriesEnabled | Numeric | This setting controls the types of AD queries used to determine the system's Distinguished Name and computer group membership. A value of 0 disables queries made to AD and the use of computer groups and OU in the configuration. The default value of 1 causes the agent to perform both the Distinguished Name and direct (non-nested) computer group AD queries. Nested computer groups in the configuration are ignored. A value of 2 causes the agent to perform the Distinguished Name, direct and nested computer group AD queries. This setting could cause performance issues on the DC due to high CPU usage. |
| AlternateTOCheck | Numeric | Trusted Ownership checks have occasionally caused excessive CPU usage in the SYSTEM process when third party filter drivers are installed on the system. Enabling this setting, using a value of 1, causes Application Control to use an alternative method of looking up Trusted Ownership, which mitigates this issue in some cases. |
| AMFileSystemFilterFailSafe | Numeric | This setting configures whether the file system filter driver operates in a Fail Safe or Fail Secure mode. If there is a problem with the Agent and it stops responding, the driver disconnects in Fail Safe mode and does not intercept anymore requests. A value of 1 indicates Fail Safe, 0 indicates Fail Secure. Fail Safe is the default. Changing this setting requires an Agent restart to take effect. |
| AppHookDelayLoad | Text | This setting causes the AmAppHook Dll to load after a configurable number of milliseconds (ms) delay. This setting is configured on a per filename basis. The format is <filename+extension>,<delay>. The filename and extension can contain wildcards. Each pair is semi colon delimited. For example 'calc.exe,2000;note*.exe,6000' |
| AppHookEx | Text | Application Control utilizes a Windows hook as
part of the Application Network Access Control (ANAC) feature.
In rare cases, applications can display unexpected behavior when
hooked. This setting is a list of applications in which ANAC specific
functions are not hooked and therefore not subject to the ANAC
rules.
If an application is named in both AppHookEx and UrmHookEx, the AmAppHook.dll is not loaded. Multiple entries are delimited by a semi-colon (;). |
| AppInitDllPosition | Numeric | Use this setting to specify whether the AsModLdr driver or the Appinit registry key is used to inject the Application Control hook. This setting is also used to determine the position of AMLdrAppinit.dll in the AppInit_DLL registry value.
Set one of the following values:
This setting should only be used under the guidance of the Ivanti Support Team. |
|
AssumeActiveSetupDespiteCitrix |
With Citrix clients using published applications, Windows Active Setup is not run as part of the Citrix client log on. By default Application Control detects that the client is using a Citrix protocol and then assumes Active Setup is excluded so that blocked applications will never be allowed under circumstances that may look like Active Setup. In addition, and optionally, Application Control can impose a more stringent check for Citrix being involved: set the value of this setting to 1 so that Application Control imposes the more stringent check if it appears that denied applications are being allowed in these circumstances. Set the value to 2 to stop Application Control from making these 'Citrix' checks at all if applications appear to be blocked during a real Active Setup. |
|
| BrowserAppStorePort | Numeric | Enter the port used to allow the Browser Control Chrome extension to be installed. |
| BrowserCommsPort | Numeric | Enter the port used for communications from browser extensions to the agent. |
| BrowserExtensionInstallHive | Numeric | This engineering setting allows the administrator to choose which registry hive the Application Control Chrome browser extension will be installed in. Options are:
0 is where the administrator must manually configure their own enterprise appstore to deploy the Application Control Chrome Extension. The default behaviour is 2 - for the chrome extension to be installed in HKCU. |
| BrowserHookEx | Text | The value can be set to 'Chrome.exe' to stop the Application Control browser hook (BrowserHook.dll) from being injected into it. The browser hook prevents all network communications until the Chrome Extension has established a connection with the Application Control Agent. No core functionality is affected by this custom setting. |
| BrowserNavigateEx | Text | A pipe (|) delimited list of navigation URLs that bypass the navigate event processing. The URLs in this list are not subject to URL redirection. |
| ComputerOUThrottle | Numeric | This setting limits an Active Directory look-up per connecting client for checking Organizational Unit membership by limiting the number of concurrent queries. This throttling helps reduce the amount of query-traffic on a domain if handling a large volume of connecting clients. Set this value between 0 and 65535. |
| DFSLinkMatching | Numeric | DFS Link paths can be added to the rules. DFS Links and DFS Targets are treated as separate independent items to be matched. There is no conversion from Link to Target before applying the rules. Set this value to 1 to enable DFS Link matching. |
| DirectHookNames | Text | Application Control's Windows hook is loaded into all processes that load user32.dll by default. Applications which do not load this DLL are not hooked. Any applications which do not load user32.dll should be included in this setting as part of a semi-colon delimited list of full paths or filenames. |
| DisableAppV5AppCheck | Numeric | By default, any application launched using AppV5 is exempt from Trusted Ownership checking. Use this setting to disable this behavior with a value of 1. |
| DisableSESecondDesktop | Numeric | By default, the auditing dialog for Self-Elevation displays on a second desktop. Set to 1 to display the dialog on the primary desktop. |
| DoNotWalkTree | Numeric | By default, process rules check the entire parent key for a match. This setting instructs process rules to only look at the direct parent of the process and not check the entire tree. A value of 1 enables this setting. |
| DriverHookEx | Text | A semi-colon delimited list of applications that will not have the Application Control Hook (AMAppHook.Dll) injected. Application Control requires the hook to be loaded for certain functionality to work. This custom setting should only be used under the guidance of the Ivanti Support Team. |
| EnableScriptPreCheck | Numeric | Whilst scripts within scripted rules are
processing, they are treated as though they have returned a false
value. The length of time scripts take, varies according to
their content. This setting provides the best performance during computer
start-up and user logon because anything depending on the result
of a script is not delayed. Set the value to 1 to make processes wait until the relevant script
has finished.
This can significantly slow down computer start-up and user login. Application Control does not wait indefinitely for scripts results - a 30 second timeout is applied. |
| EnableSignatureOptimization | Numeric | This setting improves the performance of rules
checking, when using signatures. Files that do not match the full
path are not hashed as it is assumed they are not the same file.
Set to 1 to enable. Enabling this setting and ExtendedAuditInfo will not show any hashed file name in auditing metadata. |
| ExplicitShellProgram | Text | This setting is used by Application Access Control (AAC). Application Control treats the launch of the shell program (by default explorer.exe) as the trigger for that session to be considered logged on. Different environments and technologies can change the shell application and the agent on occasion can't detect what the shell program is. Application Control uses the applications in this list (in addition to the default shell applications) to determine when a session is deemed to have logged on. This is a semi-colon delimited list of full paths or filenames. |
| ExProcessNames | Text | A list of space separated filenames that should
be excluded from the filter driver.
Changing this setting requires an Agent restart to take effect. |
| ExtendedAuditInfo | Numeric | This setting extends the file information for
audited events. It reports the Secure Hash Algorithm 1 (SHA-1)
hash, file size, file and product version, file description, vendor,
company name, and product name for each file in its audited events.
The information is added immediately after the file name in the
event log. This setting is on by default. To turn it off, enter
a value of 0.
The generation of a hash or checksum is disabled when the EnableSignatureOptimization setting is enabled. |
| ForestRootDNQuery | Numeric | Set the value to 1 to enable the Application Control Agent to perform a forest root query. The query includes chasing referrals to determine the Distinguished Name of connecting devices for the purposes of OU and Computer Group membership in Device Rules. |
| ImageHijackDetectionInclude | Text | A list of process names against which all child processes are verified to ensure the child image is running without corruption or modification and is a match for the one that was initially requested. If the child process is not verified, it is terminated. This is a semi-colon delimited list of full paths or file names. |
| OwnershipChange | Numeric | Application Control detects if a trusted file is changed by a non-trusted owner. In such a case, the file owner is changed to the untrusted user and any execute requests are blocked. Some applications overwrite files in such a way that Application Control does not detect it by default, therefore the owner of the file is not changed. When enabled, Application Control performs additional checks to catch all file changes and overwrites should be caught. Set to a value of 1 to enable. |
| RemoveDFSCheckOne | Numeric | When files are stored on a DFS drive, the Application Control agent uses a number of strategies to evaluate the correct UNC path. One of these strategies can cause delays during login if large numbers of scripts and executables are stored in and replicated by, Active Directory. Set to a value of one to enable, causing Application Control to ignore this strategy and increase performance in this situation. |
| SECancelButtonText | Text | The text displayed by the cancel button on the Self-Elevation dialog. |
| SelfElevatePropertiesEnabled | Numeric | Set this value to '1' to enable self-elevation of properties. This feature is disabled by default. |
| SelfElevatePropertiesMenuText | Text | The text in the context menu option for self-elevation of properties. |
| SEOkButtonText | Text | The text displayed by the OK button on the Self-Elevation dialog. |
|
ShowMessageForBlockedDLLs |
Set the value to 1 to display the Application Control access denied message box for denied DLLs. |
|
| UrlRedirectionSecPolicy | Numeric | By default, the security policy is ignored by the URL Redirection feature. This engineering setting allows the administrator to force URL Redirection to follow the configured security policy. Set to a value of 1 to enable. Self Authorization is not supported. |
| UrmForceMediumIntegrityLevel | Text | A User Privilege Management (UPM) custom setting used to override the integrity level when user privileges are elevated applications, which by default sets the integrity level to high. When this setting is used, the level is reduced to medium. This value should be a semi-colon delimited list of file names. |
| UrmHookEx | Text | Application Control utilizes a Windows hook as
part of the User Privilege Management feature. In rare cases,
applications display unexpected behavior when hooked. This setting
lists the applications where User Privilege Management specific
functions are not hooked.
If an application is named in both AppHookEx and UrmHookEx, the AmAppHook.dll is not loaded Multiple entries are delimited by a semi-colon. |
| UrmPauseConsoleExit | Text | Used by the User Privilege Management feature. When a console application is elevated, a new application can appear in a new console window. The application runs to completion then closes. This is a problem if the user wants to see the output of the program. This setting causes the application to remain until a key is pressed. This is a semi-colon delimited list of full paths or filenames. |
| UrmSecPolicy | Numeric | By default, the security policy is mostly ignored by the User Privilege Management feature. User Privilege Management rules are applied in all cases except for when Audit Only mode is selected. This custom setting allows administrators to force User Privilege Management to follow the configured security policy. For Unrestricted and Self-Authorize security levels, User Privilege Management rules are not applied. For the Restricted level, User Privilege Management rules are applied. Set to a value of 1 to enable this setting. |