Creating a New Patch Task
A patch task is used to define how and when the target machines will be scanned for missing patches. It can also be used to optionally deploy any patches identified as missing. If you do not create a patch task, then no patch scanning or patch deployment will be performed by agents that are assigned this policy.
Depending on the operating systems supported in your organization, you may create patch tasks for Windows machines, for Linux machines, or both. There are separate patch tasks for contentless and content-based Linux patching. You can create multiple patch tasks for one agent policy. Each task can be expanded and collapsed using the icon (![]() ) that resides on the task title bar. This enables you to view just the task you are working on at any one time.
) that resides on the task title bar. This enables you to view just the task you are working on at any one time.
While there is no theoretical limit to the number of patch tasks you can create for an agent policy, there is a practical limit. For example, it may become difficult to track and manage a policy if it contains too many patch tasks. Also, it may be problematic if you enable patch deployment on several different patch tasks. This is because that while scanning is relatively transparent to the user, deploying patches is not, as it often involves a reboot of the user's machine. In addition, you run the risk of multiple deployments occurring on one machine at the same time.
You configure agent patch tasks on the Patch tab. You can edit an existing patch task, or you can create a new task by clicking either Add a Windows Patch Task or Add a Linux Patch Task. Be sure to give the task a descriptive name because this is the name that will appear within the Windows client program.
Configuring a Windows Patch Task
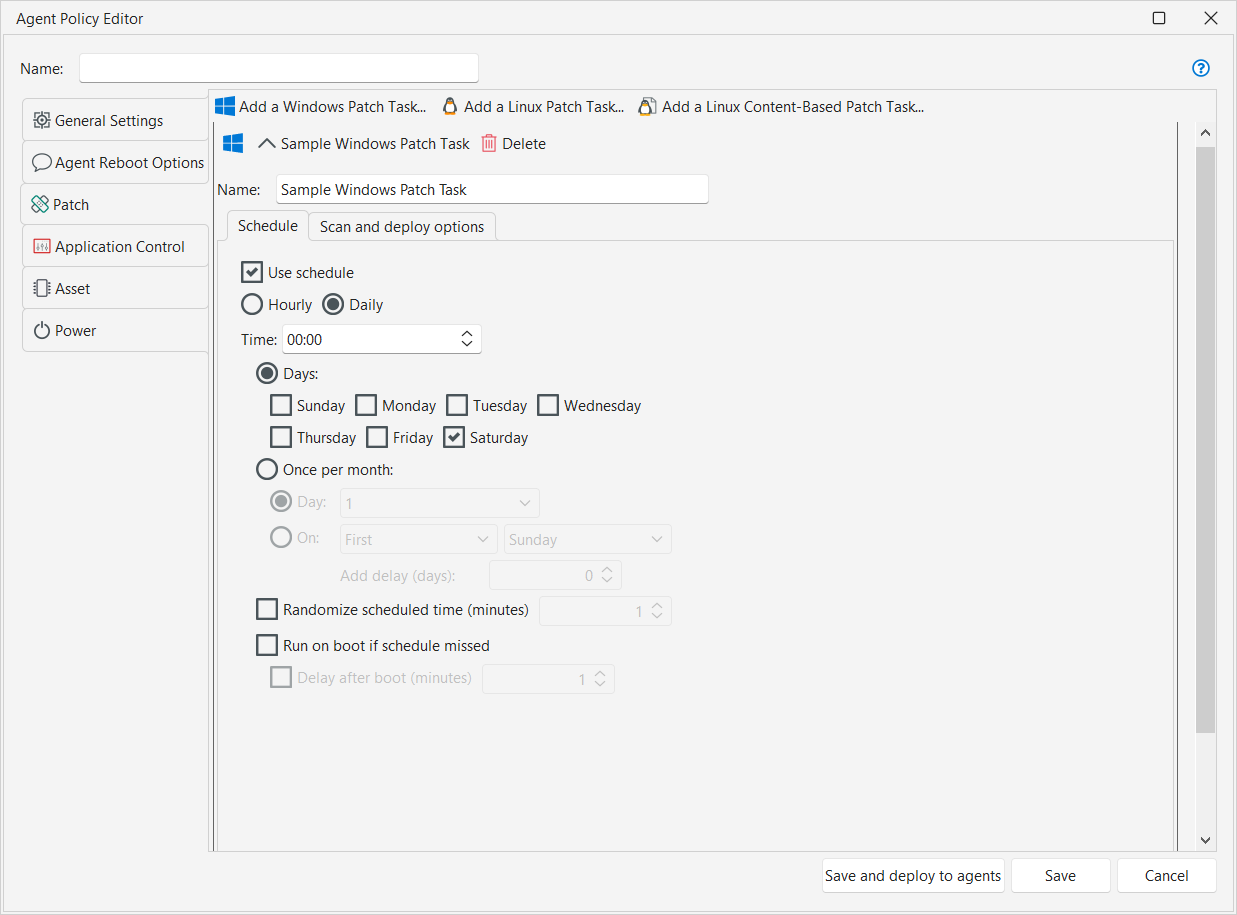
The patch schedule specifies how often the task will run on a target machine. It allows you to regularly run the task at a specific time or using a specified recurrence pattern. A built-in scheduler will be provided for each agent. The scheduler will check for new patch data immediately before starting a scheduled patch task.
The agent scheduler will serialize executions of the same agent engine. For example, if you define a policy with two patch tasks that both start at 1:00 AM, they will not both start at 1:00; rather, they will be serialized (run back-to-back).
|
Field |
Description |
|---|---|
|
Use schedule |
If enabled, the task will run on agent machines on a recurring basis according to the schedule settings. If not enabled, the schedule settings are ignored and the task must be started manually either from the console or on the agent machine. |
|
Hourly |
Allows you to schedule the task to be run on an hourly basis.
|
|
Daily |
Indicates that the task will be run on the specified days, at the time of your choosing. For example, using this option a scan could be run every night at midnight, or every Saturday at 9:00 pm, or at 1:00 am the first Sunday of every month, etc. You can also use the Daily option to schedule a task in conjunction with a regular monthly event such as Microsoft's Patch Tuesday. For example, you might schedule a monthly patch scan to occur the day after Patch Tuesday by specifying The Second Tuesday and then using the Add delay (days) option to delay the task by one day. |
|
Staggers the exact time the task will be performed so as not to overtax the console or designated distribution server with simultaneous requests to download patch files, scan engines, etc. |
|
|
If a scheduled task is missed while a target machine is powered off, this option enables you to force the task to automatically run whenever the machine is restarted. The task will run immediately unless you enable the Delay after boot (minutes) check box, in which case the execution will be delayed by the specified number of minutes. |
|
|
Deploy during the next maintenance window |
Uses the next available maintenance window after the deployment schedule for one or more patches. |
| Field | Description |
|---|---|
|
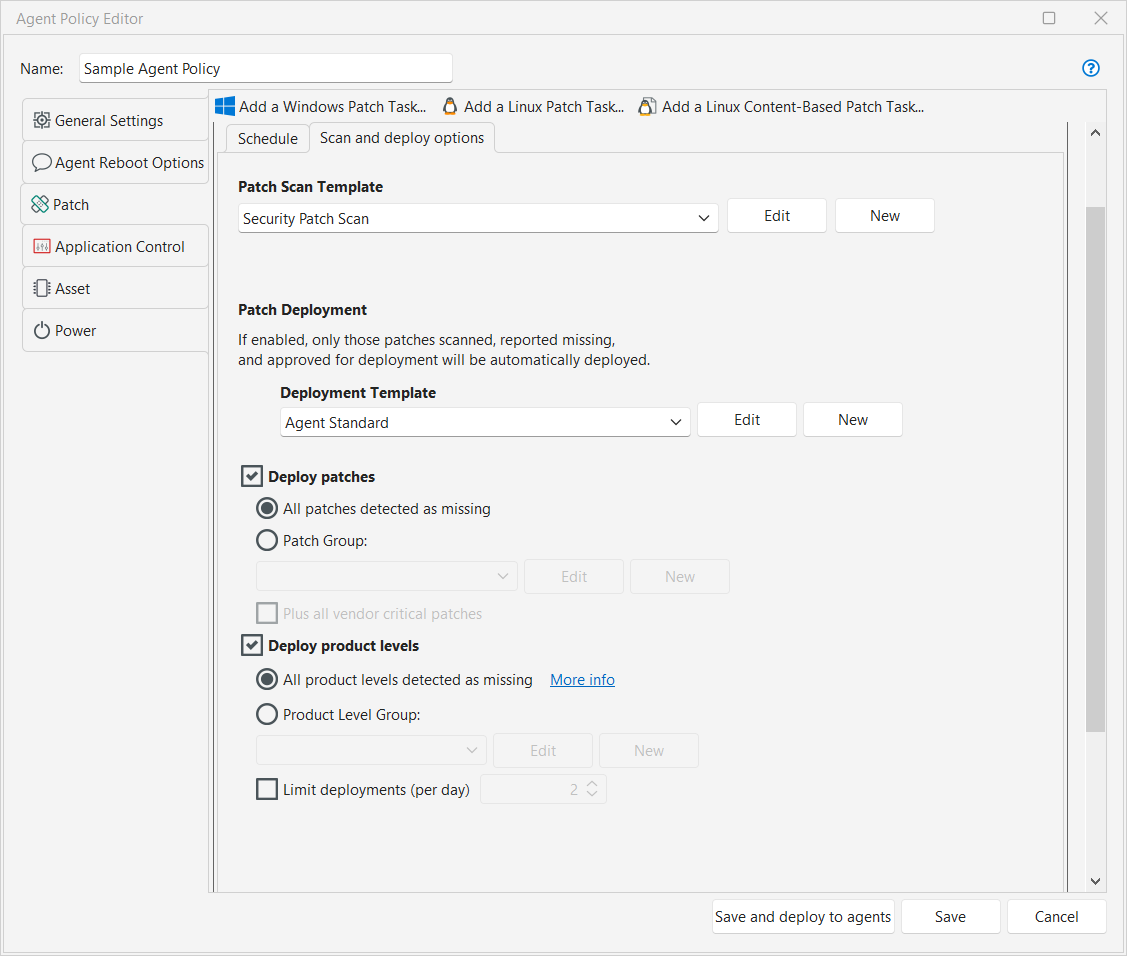
Patch Scan Template |
You must specify the template to use when an agent performs a patch scan. The patch scan template dictates exactly what will be scanned for and what will be ignored during a scan. The list of templates available for selection will include the two predefined templates (Security Patch Scan and All Patches) plus any custom templates you've already defined. You can also do the following:
If you click New or Edit, the Patch Scan Template dialog is displayed. See Creating a New Patch Scan Template for details on configuring the template. The automatic deployment function and the automatic email function on the patch scan template is not supported by Security Controls Agent. If these functions are enabled they will be ignored. |
|
Deployment Template |
You must specify the template to use when an agent performs a patch deployment. The list of templates available for selection will include the predefined deployment templates (Agent Standard, Standard, and Virtual Machine Standard) plus any custom templates you've already defined. You can also do the following:
If you click New or Edit, the Deployment Template dialog is displayed. See Creating a Deployment Template for details on configuring the template. Automatic email notifications, custom actions, and distribution server options that may be specified in the deployment template do not apply to a Security Controls Agent. |
|
Deploy patches |
If you want the agent to be able to automatically deploy patches that are identified as missing by the patch scan, enable this check box. When the agents perform a patch deployment they will deploy only those patches that are: The approved patches can be either all patches detected as missing by a scan, or they can be limited to those patches you define in a patch group and/or to those patches deemed critical by the patch vendor. The list of approved patches defined here is bound to this particular patch task. The list will not be used by other patch tasks within the agent policy.
Plus all vendor critical patches: Specifies that in addition to the patches defined in the patch group, the list of patches approved for deployment should also include any patches identified as critical by the patch vendor. This gives you the security of knowing that if your patch group is out of date you will still always be able to deploy any new critical patches. If you also choose to enable the deployment of product levels (see the Deploy product levels option), on an agent machine that is missing both product levels and patches, product levels are deployed first. Patch Deployment ProcessOnce the list of approved patches is determined, the patches are downloaded and installed according to their priority. Security patches are downloaded first, followed by all other patch types. The downloads occur in the background using idle bandwidth not being used by other applications. Foreground tasks such as Web browsing are not affected by the patch download process. Each patch task is allotted a 60 minute window to download the missing patches. (This is part of a two hour total maintenance window that is allocated for downloading missing product levels and patches.) Only those patches that are successfully downloaded during this 60 minute window will be installed by the active patch task. If the patch task cannot finish downloading all missing patches during the 60 minute window, the remaining patches will be identified, downloaded, and installed the next time the patch task is run. If an agent machine becomes disconnected from the network during a file download, the process will be suspended and will automatically resume where it left off when the network is available again. This technique is called checkpoint/restart and is extremely useful for machines that are frequently disconnected. |
|
Deploy product levels |
If you want the agent to be able to automatically deploy product levels that are identified as missing by the patch scan, enable this check box. When the agents perform a product level deployment they will deploy only those product levels that are:
The approved product levels can be either all product levels detected as missing by a scan, or they can be limited to those product levels you define in a product level group. The list of approved product levels defined here is bound to this particular patch task. The list will not be used by other patch tasks within the agent policy.
TIP: Note that a "day" in this case is considered to be a calendar date and not a 24 hour period. This means the day is reset at midnight. If you were to schedule the patch task to run on an hourly basis (not recommended), it would allow you to maximize an overnight maintenance window by deploying the maximum number of product levels before midnight and then again immediately after midnight. Product Level Deployment ProcessIf an agent machine is missing multiple product levels, only one product level will be installed at a time. The patch task will begin by initiating the download of all missing product levels. Operating system product levels are downloaded at a higher priority, but whichever product level gets downloaded first is the one that is first installed. After the product level is successfully installed, the machine is restarted, rescanned, and the process is repeated until all product levels are deployed or until the daily limit is reached [see the Limit deployments (per day) option]. In addition, each patch task is allotted a 60 minute window to complete the download > install > restart > rescan process. (This is part of a two hour total maintenance window that is allocated for downloading missing product levels and patches.) Only those product levels that are successfully downloaded during this 60 minute window will be installed by the active patch task. If the patch task cannot finish downloading all missing product levels during the 60 minute window, the remaining product levels will be identified, downloaded, and installed the next time the patch task is run. The downloads occur in the background using idle bandwidth not being used by other applications. Foreground tasks such as Web browsing are not affected by the product level download process. If an agent machine becomes disconnected from the network during a file download, the process will be suspended and will automatically resume where it left off when the network is available again. This technique is called checkpoint/restart and is extremely useful for machines that are frequently disconnected. |
Configuring a Linux Patch Task
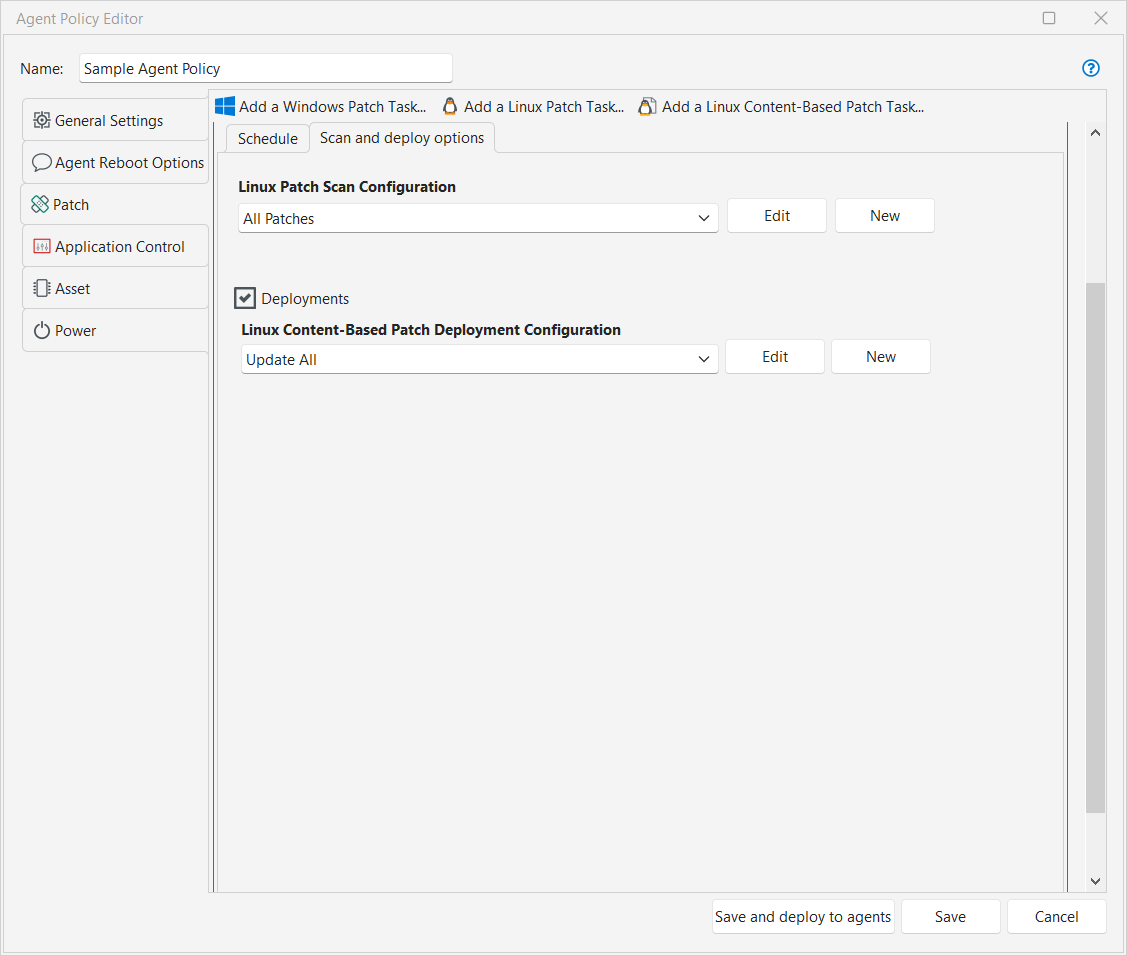
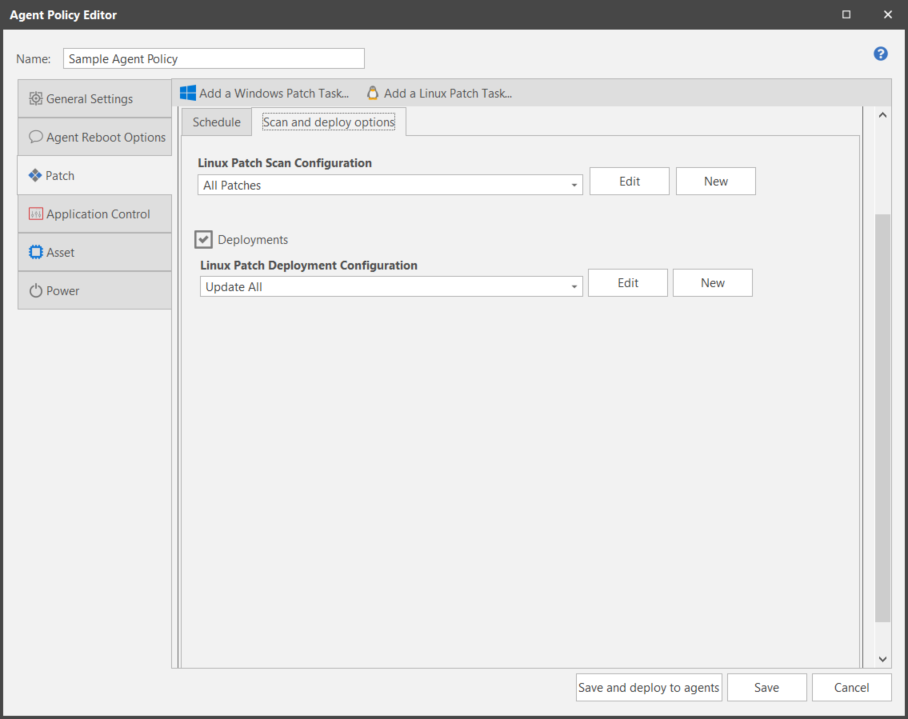
For the contentless Linux patching method, there is no separate Patch Scan Configuration. Whenever a Linux Patch Task runs, it runs a scan for all missing packages and advisories. You can then separately specify Deploy options as part of the Linux Patch Task. For the previous content-based Linux patching method, you need to specify Scan and deploy options.
The patch schedule specifies how often the task will run on a target machine. It allows you to regularly run the task at a specific time or using a specified recurrence pattern.
|
Field |
Description |
|---|---|
|
Use schedule |
If enabled, the task will run on agent machines on a recurring basis according to the schedule settings. If not enabled, the schedule settings are ignored and the task must be started manually on the agent machine using a command-line utility. |
|
Hourly |
Allows you to schedule the task to be run on an hourly basis.
|
|
Daily |
Indicates that the task will be run on the specified days, at the time of your choosing. For example, using this option a scan could be run every night at midnight, or every Saturday at 9:00 pm, or at 1:00 am the first Sunday of every month, etc. You can also use the Daily option to schedule a task in conjunction with a regular monthly event such as Microsoft's Patch Tuesday. For example, you might schedule a monthly patch scan to occur the day after Patch Tuesday by specifying The Second Tuesday and then using the Add delay (days) option to delay the task by one day. |
|
Staggers the exact time the task will be performed so as not to overtax the console or designated distribution server with simultaneous requests to download patch files, scan engines, etc. |
|
|
If a scheduled task is missed while a target machine is powered off, this option enables you to force the task to automatically run whenever the machine is restarted. The task will run immediately unless you enable the Delay after boot (minutes) check box, in which case the execution will be delayed by the specified number of minutes. |
|
Field |
Description |
|---|---|
|
Linux Patch Scan Configuration (Content-Based only) |
For Content-Based Linux patching, you must specify the configuration to use when an agent performs a Linux patch scan. The patch scan configuration dictates exactly what will be scanned for and what will be ignored during a scan. The list of configurations available for selection will include the two predefined configurations (Security Patch Scan and All Patch Scan) plus any custom configurations you've already defined. You can also do the following:
If you click New or Edit, the Linux Patch Scan Configuration dialog is displayed. See Creating and Editing a Linux Patch Scan Configuration for details. |
|
Linux Patch Deployment Configuration |
You must specify the configuration to use when an agent performs a patch deployment. The list of configurations available for selection will include the predefined deployment configuration (Linux Patch Deployment) plus any custom configurations you've already defined. You can also do the following:
If you click New or Edit, the Linux Patch Deployment Configuration dialog is displayed. See Creating and Editing a Linux Patch Deployment Configuration for details. |
Saving an Agent Policy
|
Field |
Description |
|---|---|
|
Save and update Agents |
Saves all changes to the policy file and stores it on the console. Also updates any agent machines that are currently assigned this policy as follows:
The Agent Policy Editor will be closed. |
|
Save |
Saves all changes to the policy file and then closes the Agent Policy Editor. The changes are not pushed out to listening agents. |
|
Cancel |
Indicates you want to exit the Agent Policy Editor without saving your most recent changes. A "Do you want to save your changes?" prompt will appear that gives you a second chance to save your changes. If you click Yes the policy will be saved and the associated agents updated (the same as Save and Update Agents). If you click No the Agent Policy Editor will be closed without saving your changes. |