Amazon Web Services Amazon Inspector Connector User Guide
Overview
Amazon Inspector allows users to ingest Amazon Inspector data from their AWS cloud instance. Amazon Inspector tests the network accessibility of Amazon EC2 instances and the security of applications that run on those instances. Amazon Inspector assesses applications for exposure, vulnerabilities, and deviations from best practices. After performing an assessment, Amazon Inspector produces a detailed list of security findings organized by severity level. This connector is specifically designed for the latest Amazon Inspector product, not the classic version.
This connector pulls security-findings data based on the assessments configured on the AWS account. The data from Amazon Inspector scans is pulled into Ivanti Neurons for RBVM and can be used to prioritize and remediate those findings.
Connector Configuration
Prerequisites
- An active subscription to Ivanti Neurons for RBVM.
- An active subscription to Amazon Inspector.
- AWS Region of the selected Amazon Inspector instance.
- Access Key and associated Secret Key for AWS User.
More details on Amazon Inspector can be found here: What is Amazon Inspector? - Amazon Inspector
User Setup
To set up the connector, the user needs API access to an AWS account with full access to the Amazon Inspector service. The user needs the following permissions:
- AmazonInspectorFullAccess: Have an AWS admin provide AmazonInspectorFullAccess permissions to your AWS User ID.
AWS Amazon Inspector uses the service-linked role named AWSServiceRoleForAmazonInspector. The AWSServiceRoleForAmazonInspector service-linked role trusts Amazon Inspector to assume the role.
The role’s permissions policy allows Amazon Inspector to complete the following action on the specified resources:
- Action: iam:CreateServiceLinkedRole on arn:aws:iam::*:role/aws-service-role/inspector.amazonaws.com/AWSServiceRoleForAmazonInspector
To successfully create the AWSServiceRoleForAmazonInspector role, the IAM identity (user, role, or group) used when working with Amazon Inspector must have the required permissions. To grant the required permissions, attach the AmazonInspectorFullAccess managed policy to the IAM user, group, or role.
Connections
The following API calls are performed during a connector run to pull security vulnerabilities from Amazon Inspector into Ivanti Neurons.
|
API Type |
Endpoint |
|---|---|
|
Get Vulnerability Details |
/findings/list |
Platform Setup
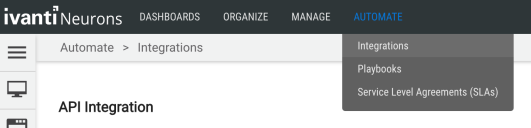
When logged into the platform, navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type Amazon Inspector to find the connector. Choose the one that says Amazon Inspector, not the classic version.
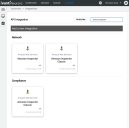
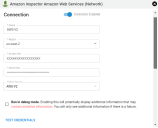
Complete the following fields. These fields include:
- Name: Connector name.
- Region: AWS Amazon region
- Access Key and Secret Key: AWS Amazon Inspector access key and secret key credentials for accessing the Amazon Inspector API endpoints.
- Network: Network name in Ivanti Neurons for RBVM. Ingested data will be associated with this network.
Once the fields are complete, click Test Credentials to verify that the credentials are correct and enable the system to connect to the AWS instance.
Configure the desired schedule for the connector to retrieve results from the Amazon Inspector instance.
Optional Configurations
No optional configurations are available for the Amazon Inspector connector.
Once connector configuration is complete, click Save to create the connector.
As soon as the connector is created, it will begin pulling data from the Amazon Inspector platform. When the connector is set up, a new entry for it appears at the top of the Integrations page. The connector card will also show the next scheduled time and date results will be fetched. Check the connector’s status by clicking the History button.
To run the connector on demand, click the Sync icon.
Editing a Connector Configuration
Connector configurations can be updated at any time after creation. Go to the Automate > Integrations page and select the specific connector you want to update.
Utilizing the Connector
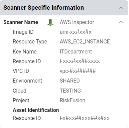
The data from the Amazon Inspector API is ingested into Ivanti Neurons for RBVM as Hosts and Host Findings. The Scanner Name associated with these scans is AWS Inspector. Scanner Name can be used as a filter for Hosts and Host Findings.
Assets
Asset data extracted from Amazon Inspector API is shown on the Hosts page. Project and version details are also extracted from the endpoint.
Findings
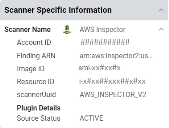
Scan data pulled from AWS via the connector can be viewed on the Network > Hosts and Network > Host Findings pages. The Host Findings page displays all identified vulnerability details, as shown below.
Severity Mapping
|
Score |
Severity |
|---|---|
|
0 |
Informational |
|
0.1–3.9 |
Low |
|
4.0–6.9 |
Medium |
|
7.0–8.9 |
High |
|
9.0–10.0 |
Critical |
Connector Data Mapping
This table maps the high-level fields from Amazon Inspector to those within the Ivanti Neurons for RBVM platform.
|
Section |
Ivanti Neurons Field |
Amazon Inspector Field |
Filterable |
|---|---|---|---|
|
Hosts
|
AWS Image ID |
findings → resources → details → awsEc2Instance → imageID |
Yes |
|
IP Address |
findings → resources → details → awsEc2Instance → ipv4addresses |
Yes |
|
|
IP Addresses |
findings → resources → details → awsEc2Instance → ipv4addresses |
Yes |
|
|
Hostname |
findings → resources → details → tags → Name |
Yes |
|
|
AWS Resource Type |
findings → resources → details → type |
Yes |
|
|
AWS Key Name |
findings → resources → details → awsEc2Instance → keyname |
Yes |
|
|
AWS VPC ID |
findings → resources → details → awsEc2Instance → vpcid |
Yes |
|
|
AWS Project |
findings → resources → details → tags → Project |
Yes |
|
|
AWS Cloud |
findings → resources → details → tags → Cloud |
Yes |
|
|
AWS Environment |
findings → resources → details → tags → Environment |
Yes |
|
|
Possible solution |
findings → remediation → recommendation → text |
Yes |
|
|
Scanner name |
AWS Inspector |
Yes |
|
|
Plugin Details -> Source |
findings → packageVulnerabilityDetails → source |
Yes |
|
|
Plugin Details -> Source Status |
Open |
Yes |
|
|
CVE |
findings → packageVulnerabilityDetails |
Yes |
|
|
First Seen |
findings-> firstObservedAt |
Yes |
|
|
Last Seen |
findings-> lastObservedAt |
Yes |
|
|
Port |
findings → networkReachabilityDetails → openPortRange → begin/end |
Yes |
|
|
Protocol |
findings → networkReachabilityDetails → protocol |
Yes |
|
|
AWS Inspector Account ID |
findings-> awsAccountId |
Yes |
|
|
AWS Inspector Finding ARN |
findings-> findingsARN |
Yes |
|
|
AWS Image ID |
findings → resources → details → awsInstanceProfileARN → imageId |
Yes |
|
|
AWS Instance ID |
findings → resources → id |
Yes |
|
|
Plugin Details ->Instance ID |
findings → resources → id |
Yes |
|
|
Host Findings
|
Title |
findings → title |
Yes |
|
Description |
findings-> description |
Yes |
|
|
Scanner plugin |
findings-> findingsARN minus the first portion up to “findings/” leaving only the ending hash |
Yes |
|
|
Severity |
findings-> inspectorScore |
Yes |
|
|
Scanner reported severity |
findings-> severity |
Yes |
|
|
Possible solution |
findings → remediation → recommendation → text |
Yes |
|
|
Scanner name |
AWS Inspector |
Yes |
|
|
Plugin Details -> Source |
findings → packageVulnerabilityDetails → source |
Yes |
|
|
Plugin Details -> Source Status |
Open |
Yes |
|
|
CVE |
findings → packageVulnerabilityDetails |
Yes |
|
|
First Seen |
findings-> firstObservedAt |
Yes |
|
|
Last Seen |
findings → lastObservedAt |
Yes |
|
|
Port |
findings → networkReachabilityDetails → openPortRange → begin/end |
Yes |
|
|
Protocol |
findings → networkReachabilityDetails → protocol |
Yes |
|
|
AWS Inspector Account ID |
findings-> awsAccountId |
Yes |
|
|
AWS Inspector Finding ARN |
findings-> findingsARN |
Yes |
|
|
AWS Image ID |
findings → resources → details → awsInstanceProfileARN → imageId |
Yes |
|
|
AWS Instance ID |
findings → resources → id |
Yes |