Micro Focus Fortify Software Security Center (SSC) Connector Guide
Summary: How to set up and use the Micro Focus Fortify Software Security Center (SSC) connector in Ivanti Neurons RBVM/ASPM/VULN KB.
About the Fortify Software Security Center Integration
The Ivanti Neurons RBVM/ASPM/VULN KB platform provides an API-based connector that integrates with Fortify Software Security Center (SSC), enabling customers to bring in their SAST and DAST findings from Fortify Static Code Analyzer (SCA) and Fortify WebInspect products into Neurons RBVM/ASPM/VULN KB. This allows customers to gain visibility into their overall risk due to vulnerabilities in their source code/web applications and enable a simpler, more efficient way to manage those vulnerabilities.
The integration allows security and vulnerability teams to:
-
Understand their exposure to vulnerabilities and threats in their business critical web applications.
-
View top software flaws in their web applications based on mappings such as CWE Top 25, OWASP Top 10, SANS Top 25, etc.
-
Prioritize and remediate top weaknesses and flaws.
Neurons RBVM/ASPM/VULN KB users can configure the connector to pull scan data from Fortify Software Security Center on a periodic basis.
How it Works
The Neurons RBVM/ASPM/VULN KB Fortify connector programmatically connects with Fortify SSC to pull in scan data for either source code or web applications. It is assumed that a user has already setup Fortify SCA, Fortify WebInspect, and Fortify SSC. For the Ivanti Neurons Fortify connector to work properly, the following steps must be performed:
-
The user runs a scan on a project from Fortify SCA for static files, or from Fortify WebInspect for dynamic URLs, and generates a .fpr file.
-
The user then uploads the .fpr file to Fortify SSC.
-
The Neurons RBVM/ASPM/VULN KB Fortify connector should be configured with its Fortify SSC credentials and enabled.
-
The connector establishes a connection with Fortify SSC and pulls scan data via the API.
-
The scan data is parsed and mapped within the Neurons RBVM/ASPM/VULN KB platform and displayed within the Application views.
Fortify Product Overview
Fortify SSC is used for processing .fpr files (scanned results) generated by both Fortify SCA and Fortify Web Inspect.
Download Fortify SSC from the following URL: Fortify Software Security Center
Generating Fortify Scan Files
Fortify Prerequisites
Navigate to the Fortify website and sign up for an account. Download the following products:
Installation and Scan Report Generation
Fortify SCA
Install Fortify SCA by following the Windows installer’s instructions. A static code analysis report must be generated for further processing. This can be done by following these steps.
(Note: Webgoat is an open-source Java application that was deliberately created to have security vulnerabilities that can be scanned by application scanners.)
Performing a Fortify Static Scan
C:\Program Files\Fortify\Fortify_SCA_and_Apps_19.1.0\Samples\advanced\webgoat>sourceanalyzer -b WebGoat5.0 -clean
C:\Program Files\Fortify\Fortify_SCA_and_Apps_19.1.0\Samples\advanced\webgoat>sourceanalyzer -b WebGoat5.0 -source 1.5 -cp "WebGoat5.0/WebContent/WEB-INF/lib/*.jar" WebGoat5.0/JavaSource WebGoat5.0/WebContent
C:\Program Files\Fortify\Fortify_SCA_and_Apps_19.1.0\Samples\advanced\webgoat>sourceanalyzer -b WebGoat5.0 -scan -f C:\Us
Fortify Web Inspect
Install Fortify WebInspect by following the Windows installer’s instructions and use the following steps to perform a dynamic application scan:
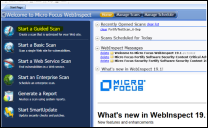
Open the WebInspect launcher.
Select Start a Guided Scan and follow the steps to perform a scan.
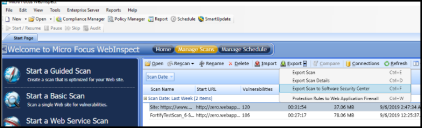
Once the scan is complete, click the Manage Scans tab to view the scans that have been performed. Select a scan and click Export > Export Scan to Software Security Center. This downloads an .fpr file.
Uploading Files in Fortify Software Security Center
Log in to Fortify SSC as a user with upload access. Navigate to the Applications tab and click New Application Version, following the instructions provided in the tab.
Configuring the Fortify Connector in Ivanti Neurons
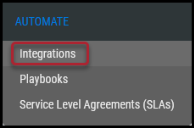
In the Neurons RBVM/ASPM/VULN KB platform, navigate to the Automate > Integrations page.
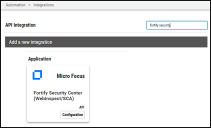
Search for Fortify Security and click the Configuration button on the Micro Focus Fortify Security Center (WebInspect/SCA) connector card.
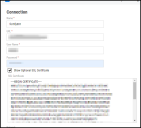
Enter your Fortify credentials in the Create Connector form. The fields include:
-
Name: Connector instance name.
-
URL: Fortify SSC instance URL.
-
User Name and Password: User credentials that can access the Fortify SSC instance.
-
Network: Neurons RBVM/ASPM/VULN KB network name (ingested applications and their findings will be associated with this network).
-
SSL: Fortify SSC instance SSL certificate.
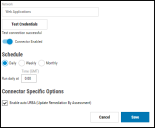
Once the form is complete, click the Test Credentials button to ensure the credentials are valid.
Note: For self-signed Fortify SSC domains, you must upload the SSL certificate for verification.
If the credential test succeeds, the Save button is enabled. Click the Save button to save the connector’s configuration.
Users can schedule the frequency for running the connectors, and Update Remediation by Assessment (URbA) can also be enabled. Neurons RBVM/ASPM/VULN KB then pulls files from Fortify SSC according to the chosen schedule.
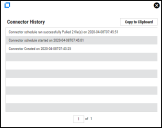
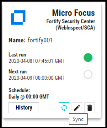
On clicking the Save button, the connector begins pulling data from Fortify SSC into Neurons RBVM/ASPM/VULN KB. Users can monitor the connector status by clicking the History button on the connector card.
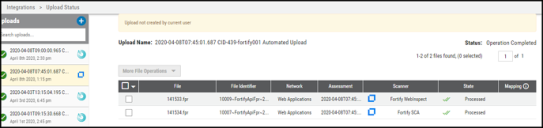
Files pulled from Fortify SSC can be viewed on the Uploads page.
To run the connector on demand, click the Sync button on the connector card.
Data Visualization in Neurons RBVM/ASPM/VULN KB
Once files have been processed on the Uploads page, the user can visualize the ingested data by navigating to either the Applications or Application Findings views.
Applications
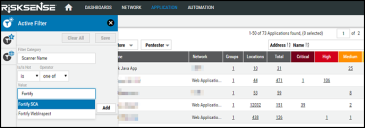
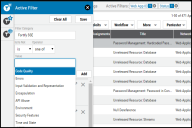
To identify Fortify-related projects, open the filter pane. Select Scanner Name as the filter category and begin typing Fortify in the value field to show related scanners.
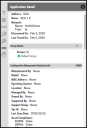
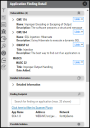
Clicking an individual row brings up the detail pane, showing in-depth information on the project.
Application Findings
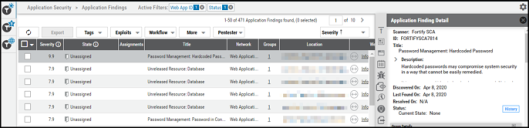
For a given project on the Applications page, the user may click on the value under Total to navigate to the Application Findings view and see findings associated with that project.
Clicking on individual findings brings up the finding detail pane. Data associated with the finding, including vulnerability information, is shown here.
Fortify SSC includes a Kingdom as one of its project properties. This field is mapped into Neurons RBVM/ASPM/VULN KB using a special new filter called Fortify SSE.
Neurons RBVM/ASPM/VULN KB Mapping of Fortify SSC Data
The table below provides the complete mapping between fields in Fortify SSC and the Neurons RBVM/ASPM/VULN KB platform.
|
Section |
Neurons RBVM/ASPM/VULN KB Field |
Fortify SCA |
Fortify WebInspect |
Filterable |
|---|---|---|---|---|
|
Applications |
Name |
Application name and version |
Application name along with the version |
Yes |
|
Total |
Total number of associated findings |
Total number of associated findings |
No |
|
|
Application Findings |
Title |
Category |
Category |
Yes |
|
Url |
Affected File Path |
Affected URL |
Yes |
|
|
Description |
Overview + Details |
Application name along with the version |
No |
|
|
WebApplication |
Application name along with the version |
Application name along with the version |
Yes |
|
|
Severity |
Criticality |
Criticality |
Yes |
|
|
Output → Fortify SSE |
Kingdom |
Kingdom |
Yes |
|
|
Output → Instance ID |
Instance Id |
Instance Id |
Yes |
|
|
Output → Impact |
Impact |
Impact |
No |
|
|
Output → Confidence |
Confidence |
Confidence |
No |
|
|
Output → Probability |
Probability |
Probability |
No |
|
|
Output → Accuracy |
Accuracy |
Accuracy |
No |
|
|
Output → Likelihood |
Likelihood |
Likelihood |
No |
|
|
Output → Implication |
Implication |
Implication |
No |
|
|
Output → References |
References |
References |
No |
Useful Filters
Application Filters
|
Filter Field |
Fortify SCA |
Fortify WebInspect |
|---|---|---|
|
Scanner Name |
A new scanner name Fortify SCA has been added for filtering applications. |
A new scanner name Fortify WebInspect has been added for filtering applications. |
|
Scanner Type |
Scanner type SAST. |
Scanner type DAST. |
Application Finding Filters
|
Filter Field |
Fortify SCA |
Fortify WebInspect |
|---|---|---|
|
Finding Type |
Finding type SAST has been added for application findings. |
Finding type DAST has been added for application findings. |
|
Fortify SSE |
Kingdom of each finding. |
Kingdom of each finding. |