Microsoft Defender for Endpoint Connector Guide
Overview
The Ivanti Neurons platform provides an API-based connector that integrates with Microsoft Defender for Endpoint, which enables customers to bring in their findings into Ivanti Neurons to gain visibility of their overall risk. Ivanti Neurons users can configure the connector to pull scan data from Microsoft Defender for Endpoint on a periodic basis, as well.
Data from Microsoft Defender for Endpoint is ingested as Hosts and Host Findings in Ivanti Neurons. Refer to the data mapping section below for details.
Microsoft Configuration
Microsoft recommends that automated application processes such as the Ivanti Neurons integration use an application context for accessing the API. It is possible to use a user context for the connector configuration; however, these instructions will specifically relate to the application creation.
- Establish a Microsoft application
- Set permissions to include the following:
- Application Machine.Read.All
- Application Vulnerability.Read.All
- Note the following information to setup the connector:
- Tenant ID
- App ID
- App Secret
- Region
Connector Configuration
Navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type Microsoft to find the connector.
Locate Microsoft Defender for Endpoint on the page and click Configuration.
In the new window under Connection, complete the required fields, as described below.
- Name: The connector’s name.
- URL: The URL to access the specific instance of Microsoft Defender for Endpoint.
- Client Id: Client associated to the Microsoft Application.
- Secret Key: Password used to access the connected system.
- Tenant Id: Tenant associated to the Microsoft Application.
- Network: Network in the platform that will contain the new assets.
After completing the login credentials form, click the Test Credentials button.
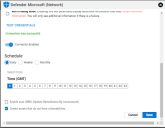
If the credentials test is successful, the Schedule connector wizard will appear.
By default, the connector is enabled. The following schedules are available.
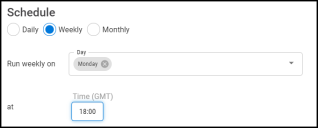
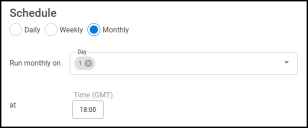
NOTE: All time selections are based on 24-hour GMT time.
Daily: Configures the connector to run at a set daily interval.
Weekly: Configures the connector to run at a set weekly interval.
Monthly: Configures the connector to run on a set date every month.
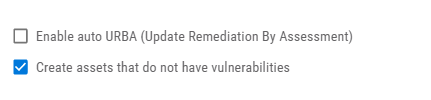
Microsoft Defender for Endpoint has identified assets that have not been scanned for vulnerabilities. These assets will be included on the import to the platform unless this option is unchecked.
Click the Save button to save the configuration and view the configured connector.
Editing a Connector Configuration
Connector configurations can be updated at any time after creation. Go to the Admin > Connectors page and select the specific connector you want to update.
Microsoft Defender for Endpoint Data Mapping in Ivanti Neurons
The data from MDE is ingested into Ivanti Neurons as Hosts and Host Findings. The Scanner Name associated with these scans is Defender Scanner Name can be used as a filter in both the Hosts and Host Findings views.
Hosts View
- Any active assets within the oldest pull date range listed in Microsoft Defender for Endpoint are shown in the Hosts view.
- Both IP address and hostname are extracted from the Microsoft Defender for Endpoint API.
- In the Host Detail, the Scanner is listed as Defender under the Sources section.
This connector includes several scanner-specific fields that are viewable in the detail pane, list view columns, filters, and exports:
- Defender Last IP Address
- Defender Last External IP Address
- Defender Agent Version
- Defender Health Status
- Defender Device Value
- Defender RBAC Group Id
- Defender RBAC Group Name
- Defender Risk Score
- Defender Exposure Level
- Defender Is AAD Joined
- Defender AAD Device Id
Hosts Findings View
All findings from the Microsoft Defender for Endpoint vulnerability database are shown in the Host Findings view in Ivanti Neurons.
This connector includes several scanner-specific fields that are viewable in the detail pane, list view columns, filters, and exports:
- Defender Security Update Available
- Defender Disk Paths
- Defender Registry Paths
- Defender End Of Support Date
- Defender End Of Support Status
- Defender Exploitability Level
- Defender Recommendation Reference
- Defender Software Version
- Defender Software Name
- Defender Software Vendor