Netsparker Enterprise Connector Guide
Summary: How to set up the Netsparker Enterprise connector.
Netsparker Enterprise Connector Overview
Netsparker is an automated online web application security scanner that enables users to identify security flaws by exploiting identified vulnerabilities. Netsparker then assigns a severity level to these vulnerabilities to convey the urgency and potential damage of a specific security weakness. Ivanti Neurons RBVM/ASPM/VULN KB offers an API-based connector that integrates the Netsparker module into the Neurons RBVM/ASPM/VULN KB platform for simplicity and flexibility. The Netsparker connector ingests application data from Netsparker and displays the vulnerabilities in the Neurons RBVM/ASPM/VULN KB platform for further prioritization.
Connector Configuration
Setting Up the Netsparker Connector
Navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type Netsparker Enterprise to find the connector.
Locate the Netsparker Enterprise card on the page and click Configuration.
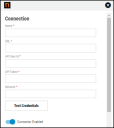
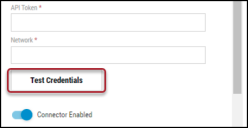
In the new window under Connection, complete the required fields, as described below.
-
Name: The connector’s name.
-
URL: Netsparker URL.
-
API User ID: The user ID that has access to Netsparker.
-
API Token: The user ID’s API token.
-
Network: Neurons RBVM/ASPM/VULN KB network name (ingested applications associated with this network).
Click Test Credentials to verify the credentials are correct and have access to make API calls to the Netsparker Enterprise instance.
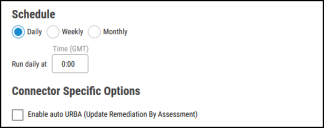
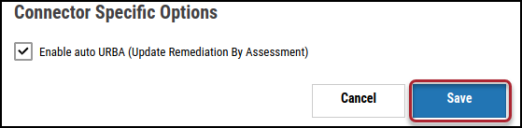
Configure the desired schedule for the connector to retrieve results from the Netsparker Enterprise instance and optionally turn on Enable auto URBA (Update Remediation by Assessment).
Click Save to create the connector.
Once saved, the connector is now visible on the Integrations page under Currently Configured Integrations.
On the Settings ( ) > Uploads page, Netsparker data is parsed from the scan file and displayed on the Applications and Application Findings pages.
) > Uploads page, Netsparker data is parsed from the scan file and displayed on the Applications and Application Findings pages.
Note: The Netsparker Enterprise API connector pulls issues based on the policy, and False Positive, Fixed, and Risk Accepted issues are filtered out. There is also a deduping process that completes before presenting Netsparker data in the Neurons RBVM/ASPM/VULN KB platform. For repeated vulnerabilities with the same URL and plugin ID, Ivanti Neurons presents it as a single finding with multiple requests and responses.
Netsparker Data Mapping in Neurons RBVM/ASPM/VULN KB
Applications Page
Application data extracted from the Netsparker Enterprise scan file is shown on the Applications page as an asset.
-
Address (Domain)
-
URLs
-
Vulnerability Counts by Severity (Total, Critical, High, Medium, Low, Info)
-
Last Scan Date
Other sections, such as Finding Categories, are populated based on information collected from the scan file.
Application Findings Page
Any finding data extracted from the Netsparker Enterprise scan file is shown on the Application Findings page.
|
Section |
Neurons RBVM/ASPM/VULN KB Field |
Netsparker Field |
|---|---|---|
|
Application Finding Details |
Title |
Title |
|
Description |
Description |
|
|
Discovered On |
First Seen Date |
|
|
Last Found On |
Last Seen Date |
|
|
Scanner Severity |
Severity |
|
|
Vulnerabilities |
CVSS 3.0 |
CVSS |
|
CWE |
CWE |
|
|
CAPEC |
CAPEC |
|
|
WASC |
WASC |
|
|
PCI32 |
PCI32 |
|
|
Detailed Information |
URL |
URL |
|
Headers |
HTTP Request |
|
|
Response |
HTTP Response |
|
|
Scanner Output |
Confirmed |
Confirmed |
|
Certainty |
Certainty |