SonarCloud Connector Guide
Summary: How to set up and use the SonarCloud connector in RiskSense.
Overview
SonarCloud is a cloud-based code quality and security service. SonarCloud operates as a static code analyzer that discovers security and quality issues in source code by interacting directly with the repositories.
RiskSense provides an API-based connector that integrates with SonarCloud, enabling customers to bring their SAST findings. This connector allows customers to gain visibility into their overall risk due to vulnerabilities in their source code and enable a simpler, more efficient way to manage those vulnerabilities.
User Prerequisites/SonarCloud Setup
SonarCloud is a cloud-based solution. RiskSense requires a user account with the following access to communicate with and pull data from SonarCloud.
-
Read access to scan results and their associated issues.
-
API access.
SonarCloud Connector API Calls
The following API calls are performed during a connector run to pull security vulnerabilities from SonarCloud into RiskSense.
|
API Type |
Endpoint |
|---|---|
|
Authentication |
https://sonarcloud.io/api/authentication/validate |
|
Fetch List of Projects Keys |
https://sonarcloud.io/api/components/search |
|
Fetch Analysis Date for Each Project |
https://sonarcloud.io/api/components/show |
|
Fetch the list of Directories for Each Project |
https://sonarcloud.io/api/components/tree |
|
Fetch the List of Issues for Each Directory |
https://sonarcloud.io/api/issues/search |
|
Fetch the List of Rules for the Organization |
https://sonarcloud.io/api/rules/search |
Fetching the SonarCloud User Token
First, log in to your SonarCloud instance with the designated user account. Navigate to My Account > Security. Enter the token name and click the Generate button.
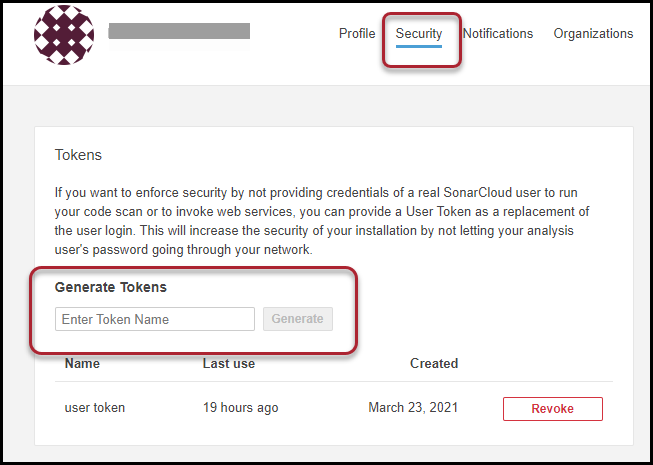
Copy the user token, as it is only displayed once. Use this token for API authentication.
Steps to Fetch the Organization Key
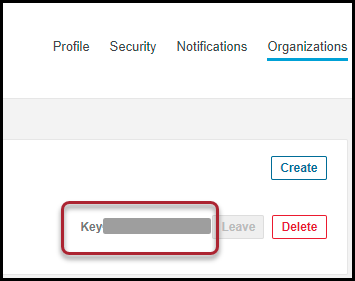
In addition to the user token, the RiskSense connector also needs the SonarCloud Organization Key. This acts as a key indicator for pulling all the associated projects within it.
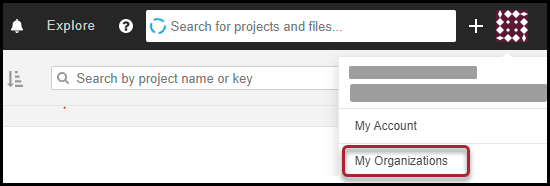
First, navigate to the My Organizations menu option.
Copy the Organization Key.
Configuring the SonarCloud Connector in RiskSense
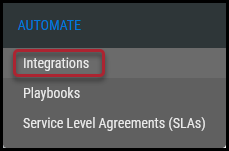
Navigate to the Automate > Integrations page.
Using the search bar in the upper-right corner of the Integrations page, type SonarCloud to find the connector.
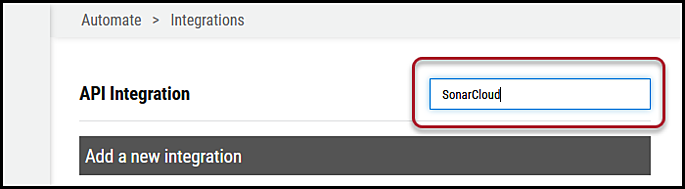
Locate the SonarCloud card on the page and click Configuration.
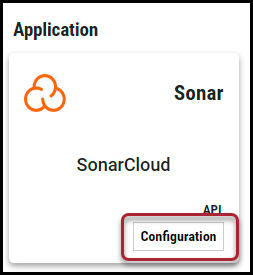
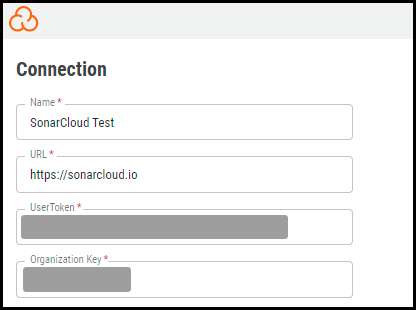
In the new window under Connection, complete the required fields, as described below.
-
Name: The connector’s name.
-
URL: The URL to access SonarCloud instance (https://sonarcloud.io).
-
User Token: User Token retrieved from SonarCloud. Refer to the steps in this section to obtain the User Token.
-
Organization Key: Refer to the steps in this section to obtain the Organization Key.
-
SSL: Optional instance SSL certificate in base64 format.
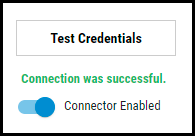
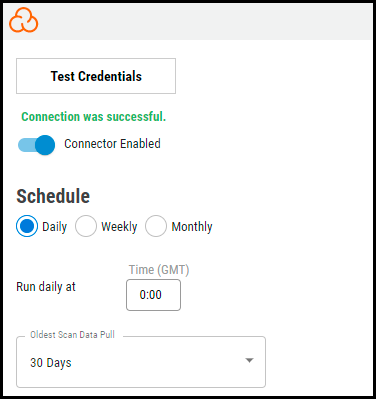
Click the Test Credentials button to ensure the credentials are correct and have the necessary access to make SonarCloud API calls.
Under Schedule, you can configure the desired schedule for the connector to retrieve results from the SonarCloud instance and optionally select the Oldest Scan Data Pull configuration.
The Oldest Scan Data Pull dropdown provides users the flexibility to pull the oldest reports from the last 30, 60, 90, 180 days, and 1 year.
Under Connector Specific Options, select the required options from the list.
Users have the option to ingest the selected SonarCloud findings. RiskSense can ingest more than one finding type.
-
Projects: Clicking the All Projects radio button allows the user to pull all projects under the organization. To pull specific projects, click the Select Projects radio button. Once selected, RiskSense makes a dynamic call to SonarCloud to fetch all associated projects. Users can select more than one project, as well.
-
Ingest Findings: The user can ingest selected findings from SonarCloud. More than one type of finding can also be ingested at once.
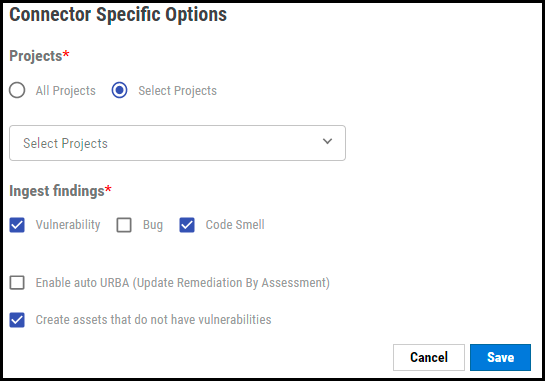
Users can optionally turn on Enable auto URBA (Update Remediation by Assessment).
On marking the Create Assets that do not have vulnerabilities options, RiskSense will create applications with zero findings. This option will be selected by default, and the user can opt to turn it off.
Click the Save button to save the connector’s configuration and create the connector. Once saved, the connector is now visible on the Integrations page under Currently Configured Integrations.
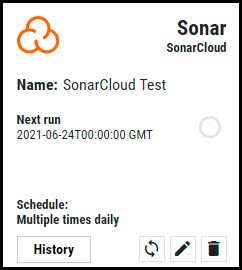
Clicking the History button displays the connector details for each pull. The Sync button allows users to perform on-demand sync. The Edit button allows the user to edit the connector configuration. The Delete button allows the user to delete the connector.
Once files have been processed on the Uploads page, view the ingested data by navigating to the Applications and Application Findings pages.
Mapping SonarCloud fields in RiskSense
This table showcases the high-level mapping of SonarCloud fields in RiskSense.
|
RiskSense Fields |
SonarCloud Fields |
|---|---|
|
Scanner Severity |
rules -> severity |
|
Normalized Severity |
The SonarCloud Severity scale: Blocker, Critical, Major, Minor, and Info. RiskSense converts this Severity scale into a scale from 0-10 using specific logic. Please contact RiskSense Support for more information. |
|
Scanner Plugin |
rules -> key |
|
Application Name |
ProjectName |
|
Plugin Source Status |
issues -> status |
RiskSense Tags
The following fields from SonarCloud are converted into RiskSense tags. Use these tags for searching, playbook automation, and better visualization in RiskSense Dashboards.
-
Organization: This tag name is prefixed with the field name to ease the searching process.
-
SysTags
-
Tags
-
Resolution
Common Fields in RiskSense
The following fields in RiskSense are defined for SonarCloud, along with their default values.
-
The Scanner Name will be SONARCLOUD.
-
The Finding Type will be SAST.
Vulnerability Date Information in RiskSense
Within RiskSense, you will notice several dates on the Findings page. When importing SonarCloud data, RiskSense uses the following criteria to populate these date fields.
-
Discovered On is the Issue Created time in SonarCloud.
-
Last Found On is when the Issue Last updated in SonarCloud.