Office 365 inbound mail configuration using OAuth2
You can use Microsoft Office 365 for inbound email, using Microsoft Graph OAuth2. You need to create an app registration for Microsoft Graph in Office 365, restrict the mailbox access, and then configure the Service Desk mailbox.
For details about how to configure a mail box using IMAP4, see Configuring a mail box for each mapping.
The first stage is to create an Ivanti Service Desk Inbound app registration in Azure.
To create the app registration:
- Log in to https://portal.office.com as an administrator and open the Admin shortcut.
- In the Microsoft 365 admin centre, open the Azure Active Directory account associated with your Office 365 tenant.
- Register a new single-tenant application.
Now we need to change some API permissions. - Remove the Delegated User Read permission.
- IMPORTANT: Add Application permission (for Microsoft Graph) for Mail ReadWrite and grant it admin consent.
This provides this application, when it has Admin consent, the permission to use the Microsoft Graph API to read and write emails in all mailboxes in your Office 365 tenant. You restrict this in the next stage.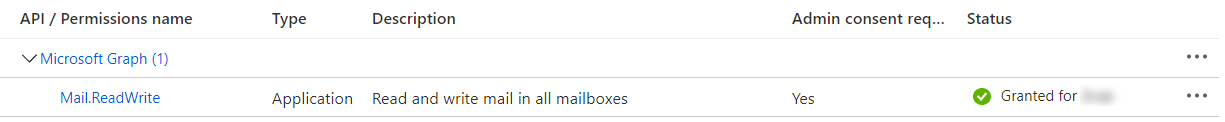
Now that you have registered the Ivanti Service Desk Inbound app, you need to restrict the mailbox access, so that only a single mailbox can be accessed by the Azure app.
For more information, see Limiting application permissions to specific Exchange Online mailboxes on the Microsoft documents site (opens in a new tab).
To restrict the mailbox access:
- Log in to https://portal.office.com as an administrator.
- Create a new mail-enabled security group.
- Add a member to the group.
This is the single user corresponding to the Inbound mailbox in Service Desk.
The next step is to link this group to the App registration in Azure by connecting to Exchange Online using PowerShell, and calling the command New-ApplicationAccessPolicy. - Install the Exchange Online PowerShell module.
See Connect to Exchange Online PowerShell on the Microsoft documents site (opens in a new tab). - Connect to Exchange Online PowerShell by using MFA.
- Configure the ApplicationAccessPolicy to link your group to the Azure App.
If you are using the PowerShell command New-ApplicationAccessPolicy described in Limiting application permissions to specific Exchange Online mailboxes on the Microsoft documents site (opens in a new tab), the parameter AppId is your Azure Application ID (also known as client ID), and the parameter PolicyScopeGroupId is the group email address of the mail-enabled security group you created. - Test the configuration with user(s) that the app should and should not have access to.
For example, if you are using the Microsoft document above, you can use Test-ApplicationAccessPolicy. - Log off.
Wait about 30 minutes for the configuration to complete. Until then, API calls to Microsoft Graph using your app will have access to all users' mail boxes.
When you have created an app registration for Microsoft Graph in Office 365 and restricted the mailbox access, you can configure your Service Desk mailbox to use Office 365 for inbound mail.
To configure a Service Desk mailbox to use Office 365 for inbound mail:
- Using the Configuration Centre, stop the Mail Manager – Inbound Service.
- In the Mail component, on the E-mail Setup tree, expand the Inbound E-mail folder, then select the Mail Boxes folder.
- On the Actions list, click New Mail Box.
The Mail Box window appears. - In the Provider list, select Microsoft Graph (OAuth2).
The dialog updates. - Enter a Title and select a Mapping.
- Under Login Details, set User Name to the User Principal Name for your Office 365 Mailbox.
This looks like an email address. - In the App registration in Azure, create a secret using the Certificates & secrets short-cut and use the Value of the secret (not the Secret ID) in the Secret field under OAuth2 details in the Mailbox settings in Service Desk.
- For the Client Id and Tenant Id under OAuth2 details in the Mailbox settings, use the Application (client) ID and Directory (tenant) ID from the Overview short-cut of your App registration in Azure.
- Click
 on the toolbar to ensure authentication is successful and the Office 365 mail box can be accessed.
on the toolbar to ensure authentication is successful and the Office 365 mail box can be accessed. - Save the new mail box.
- Start the Mail Manager – Inbound Service.
To test that the mailbox has been correctly restricted, stop the inbound service, change the User Name in the Mailbox settings in Service Desk to that of a user who does not belong to your mail security group and then click  .
.
The authentication should succeed, but access to the inbox should fail.
Remember to change the user back to the one who is a member of the mail security group, then start the inbound service.