Engine based agent (2022 and newer)
Ivanti Endpoint Manager 2022 SU3 and newer include a non-beta and fully supported engine based agent installation architecture for Windows devices. Version 2024 makes the engine based agent the only option for new agent installations. The legacy agent architecture is still supported and the engine based agent is backwards compatible with it.
Each engine controls a specific piece of agent functionality, such as patch, software distribution, remote control, and so on. Individual engines have their own installation MSI and are installed to separate subfolders on managed devices.
This new agent architecture has these benefits:
Security
- All agent MSIs and the agent installer are signed at Ivanti by Ivanti. This helps security tools and virus scanners trust the agent installer.
- The agent installer uses the core server's public key to verify the core's authenticity and signed manifest data before downloading agent components.
- The agent installer verifies engine hashes, ensuring downloaded components are authentic.
Manageability
- Modular architecture where each agent component has its own engine. Engines are self-contained as much as possible, so if an engine is having issues, other parts of the agent have a better chance of continuing to function.
- Faster installation and configuration updates.
- Drag-and-drop support for engine based agent configuration changes in Tools > Configuration > Agent configuration. No need to schedule a job or redeploy the agent to make a configuration change take effect. This helps with agent stability since unaffected components stay installed and keep their settings.
- The agent can upgrade itself to a newer version when requested.
Health
- Agent health is built into each engine. It no longer relies on vulnerability scans. When an engine detects an issue, it can automatically uninstall/reinstall itself to fix it.
- New agent health dashboard reports on engine based agent installation, upgrade, and repair failures.
Engine based agent installation
Engine based agent installation is similar to the older "advance agent." When executed, the engine based agent installer downloads individual MSI files and installs them for each agent component the agent configuration requires. The engine based agent installer automatically removes the legacy Endpoint Manager agent during installation.
The engine based agent installs to this path:
- <%ProgramFiles (x86)%>\Ivanti\EPM Agent
At a minimum, these two files are required to install the engine based agent:
- EPMAgentInstaller.exe
- Core's public certificate (.0 file)
A manifest file containing an agent configuration is optional. This file is generated automatically when you create an engine-based installer. Assignments made in the Agent configuration pane override an included manifest. If no manifest is provided, devices will use the default agent configuration for that operating system.
In Tools > Configuration > Agent configuration there are three ways to create an engine based agent installer. These options are available when you right-click a Windows agent configuration. Each option copies files to a folder you specify.
- Create engine based agent install files. Copies EPMAgentInstaller.exe, the core's public certificate (.0 file), a manifest file containing configuration details for the selected agent configuration, and a .txt file with the agent configuration name.
- Create engine based agent install MSI (unsigned). Creates a single MSI file that includes the agent installer, the core's public certificate (.0 file), and the manifest file. In Windows GPO it can be difficult to deploy multiple files. When executed, this single MSI extracts the three files and runs the installer. It is unsigned, so you may encounter issues around that with security tools. GPO installations are generally more trusted though.
- Create self contained agent based agent install MSI. Creates a single MSI containing full versions of all engine MSIs. This MSI is much larger because it includes all engine MSI files as well. It extracts and puts the files into the Endpoint Manager download cache, so when each agent installer wants to download the files it will instead find them in the local cache.
Devices discovered by XDD and UDD also support scheduler-based push installation of the engine based agent. The engine based agent can be installed through the CSA.
Managing engine based agent configurations
Engine based agent configurations are managed in the Agent configuration tool (Tools > Configuration > Agent configuration) and use the same configuration interface as the legacy agent.
Version 2024 adds agent setting enforcement options. When editing an agent configuration, the Start page has two new options:
- Enforce the assigned agent settings: Agent settings assigned in this configuration can only be changed by modifying this agent configuration.
- Don't enforce the assigned agent settings: Agent settings on a device can be modified by a change settings task. For more information, see Create change settings tasks.
In versions prior to 2024, a scheduled task agent push still deploys the legacy agent. If you want the scheduler to deploy engine based agents in versions older than 2024, add this registry key on the core server:
- HKEY_LOCAL_MACHINE\SOFTWARE\Ivanti\ManagementSuite\EnableNewAgentPush="dword:00000001"
As of version 2022 SU3, you can drag and drop items in the Network view onto a Windows agent configuration to reconfigure them.
- Doing this with a device running an engine based agent will update that device's configuration to match the agent configuration profile it is under. This happens the next time the device checks in, which is every 24 hours by default.
- Doing this with a device running the legacy agent requires a scheduled task to apply the update. After dropping legacy agent devices on an agent configuration, the Schedule task dialog box appears so you can configure the task.
Engine based agent configuration changes and order of precedence
An engine based agent manifest file is optional. The manifest can be overridden depending on other agent configuration options and where they happen.
This is the agent configuration order of precedence, from highest to lowest:
- Agent configuration changes made on the core server in the Agent configuration tool.
- Installer command line, if used. You can specify a configuration name that exists on the core.
- Previous configuration from an old agent, if that configuration name still exists on the core. This assumes no manifest is included and no configuration is specified on the command line. If a device has a custom agent configuration, this allows the installer to keep those configuration settings.
- A provided manifest containing an agent configuration.
- Default configuration for the device OS type.
Engine based agent upgrades
For agent compatibility reasons, Endpoint Manager service and version updates cause older agents to pause applying configuration changes. Agent updates on managed devices don't happen automatically.
Devices with engine based agents that aren't running the latest agent have a new Network view right-click menu option, Mark for agent upgrade. Marked agents will upgrade themselves the next time they check in.
For devices that have an engine based agent and that the core can communicate directly with, you can click Force agent check-in to have the upgrade happen right away. This option also applies any agent settings changes that have been made.
Quickly identify devices with older agents in the Network view. Click Devices > Devices with older agents. This list includes devices without the most recent legacy or engine based agent.
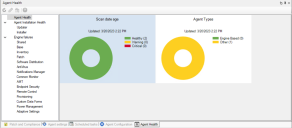
Agent Health
There's a new Agent Health tool in the console (Tools > Administration > Agent Health). It tracks these categories of agent installation issues:
- Agent updater
- Agent installer
- Individual engine failures
Click a category to see affected devices. Devices with engine based agents check their agent health once an hour. If an engine detects it is having issues, the engine will uninstall/reinstall itself. If the agent still has issues on the third hourly check, the core is notified and details will appear in Agent Health.