Client certificate-based security
Ivanti® Endpoint Manager uses a client certificate-based security model for Windows-based devices. When this security model is active, only devices with valid certificates can decrypt secure core server data.
Once client certificate-based security is enabled, it can't be disabled.
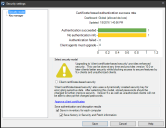
The Security settings dialog box (Configure > Security) includes a chart showing the certificate-based authentication success rate for managed devices. When managed devices attempt a secure connection to the core server or when the security scanner (vulscan.exe) runs, the connection results are saved to the device inventory.
Devices not in an Authentication succeeded state won't be fully manageable after the new security model is enabled. Usually it's older device agents causing devices to be in other states.
The chart in this dialog box summarizes connection attempt results:
- Authentication succeeded: The device has version 2016 agents, is securely connected, and is ready for the new security model. Ideally all devices are here.
- No authentication info: The device hasn't attempted a secure connection or the security scanner hasn't reported connection results back to the core yet. Note that if your core server doesn't have agents installed on it, the core will appear in this list and that's OK.
- Authentication failed: The device tried to authenticate and couldn't for some reason. Usually this happens because the device hasn't received client certificate approval (Configure > Manage client access), as discussed in the next section.
- Client agents must upgrade: The device can't authenticate because it's running older (9.x) agents.
Double-click items in the chart to view associated devices in the network view. The dynamically generated query for an item you double-clicked appears under Queries > My queries > Chart-generated queries. You can use this view to more easily target or troubleshoot devices.
More connection details may be available in the device inventory under Ivanti Management > Client certificate-based security > Authentication status.