BitLocker Configuration
The BitLocker hard drive encryption template action is used to encrypt hard drives on 64-bit versions of Microsoft Windows 10, 11, and newer Operating Systems. The management options below represent documented features supported by Microsoft’s BitLocker management utility (manage-bde.exe) and outline how the provisioning workflow interacts with this utilities’ options. For additional information on the Microsoft tool and clarity on the Microsoft option settings, please refer to Microsoft’s documentation.
Provisioning Template Action: BitLocker Hard Drive Encryption
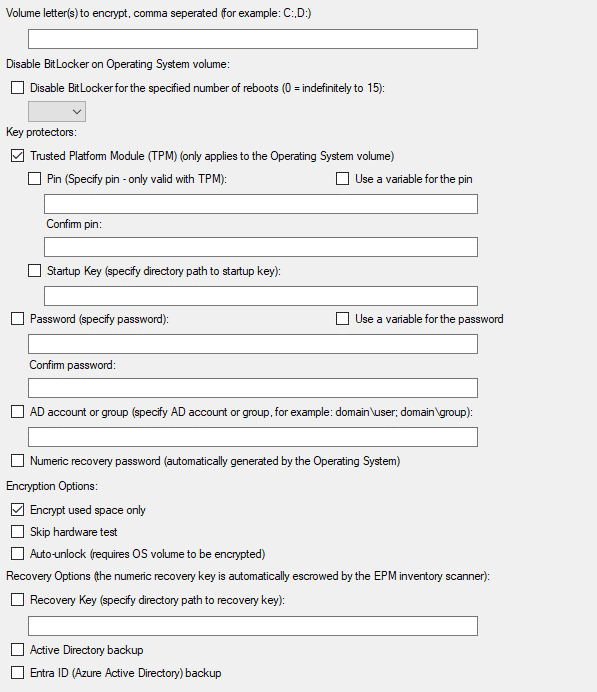
Image Reference – UI Elements Explained
-
Volume letter(s) to encrypt, comma separated (for example: C:,D:): Specify drive letters from A to Z, followed by a colon (e.g., C:). This field is not case-sensitive and accepts a comma-delimited list of drive letters. EPM will attempt to add the key protectors configured below to each of the volume letters specified. Some key protectors can only be added to system volumes.
-
Disable BitLocker on Operating System volume: This option temporarily suspends BitLocker while retaining existing Key Protectors. For the specified number of reboots (1 to 15), BitLocker enforcement is disabled by Microsoft. A value of 0 disables enforcement indefinitely until manually re-enabled. To re-enable, you can either reapply a key protector or run the following command manually: manage-bde -on C: (Replace C: with the appropriate volume letter.)
-
Key protectors:
-
Trusted Platform Module (TPM) (only applies to the Operating System volume): TPM is a hardware component typically integrated into the motherboard. Pin and Startup Key options require TPM and are only applicable to the system volume (where Windows is installed).
-
Pin (Specify pin - only valid with TPM): It's recommended to use a provisioning variable of type sensitive to encrypt and securely store any password.
-
Startup Key (specify directory path to startup key): This is a path (either a local path on an unencrypted drive or a UNC path) where a key file is stored. BitLocker uses this file for authentication during startup.
-
-
Password (specify password): Passwords apply to all specified BitLocker volumes. For example, if you specify C:, D:, E:, the same password is applied to each. To use different passwords per volume, configure a separate BitLocker action for each volume letter. As with PINs, it is recommended to use sensitive provisioning variables for passwords to ensure secure encryption.
-
AD account or group (specify AD account or group, for example: domain \user; domain\group): Enter an Active Directory username or group in the format: domain\user or domain\group.
-
Numeric recovery password (automatically generated by the Operating System): This is a 48-digit key automatically generated by the OS for recovery purposes. If the EPM agent is installed on the managed device, the EPM Inventory Scanner will automatically gather this key and upload it to the EPM Core Server.
-
-
Encryption Options:
-
Encrypt used space only: Only used sectors, the sectors where data is stored, will be encrypted. This is a faster encryption process and recommended by Microsoft for most scenarios. Uncheck this option to encrypt the entire drive for higher security requirements.
-
Skip Hardware Test – This options skips Microsoft’s BitLocker pre-check which ensures all key protectors are properly configured and the system can reboot securely.
-
Auto-unlock (requires OS volume to be encrypted) – This applies only to non-system volumes. The unlock key is stored on the encrypted system volume, so BitLocker must be enabled on the system volume for this option to work.
-
-
Recovery Options (the numeric recovery key is automatically escrowed by the EPM inventory scanner):
-
Recovery Key (specify directory path to recovery key): The EPM Inventory Scanner automatically collects the numeric recovery key if that protector is enabled. Keys can also be backed up as .BEK files to a local (unencrypted) hard drive, a USB drive, or UNC network share.
-
Active Directory backup: can escrow certain key types—PINs, passwords, and numeric keys—into AD container objects.
-
Entra ID (Azure Active Directory) backup: supports similar key backups for supported protector types.
-
Group Policy Object (GPO) settings:
Microsoft BitLocker options are significantly influenced by the Group Policy Object (GPO) settings applied to the managed device, particularly those linked to domain policies. Before deploying BitLocker provisioning templates, it's essential to review and configure the relevant GPO settings to ensure the desired outcomes. Below are key GPO configuration areas that should be aligned with your intended BitLocker settings prior to deploying EPM provisioning templates:
-
Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption
-
Store BitLocker recovery information in Active Directory Domain Services
-
Fixed Data Drive > Choose how BitLocker-protected fixed drives can be recovered
-
Operating System Drives > Choose how BitLocker-protected system drives can be recovered
-
Operating System Drives > Configure use of passwords for operating system drives
-
-
After modifying any GPO settings on the device, run gpupdate /force to ensure the changes are applied immediately before proceeding with any testing.