Application behavior script blocking
File protection rules can block the most common way endpoints get infected by malware or ransomware—when a user is tricked (usually by a phishing email) into opening an attachment or downloading a file from the internet that contains the malware. Most of those files users are tricked into opening are from known types, such as Word documents with macros, .JS (JavaScript) files, and other types of scripts.
Using file protection rules, you can set rules that prevent .JS files and other scripts from being used by users (note that this does not limit users from using JavaScript in their browser). By blocking the usage of scripts (which most users do not need to use), a large portion of this attack vector can be eliminated.
It is most likely that users will not need to run scripts on their computers; however, in some cases legitimate third-party applications may need to run scripts. For that reason, it’s recommended that you start using file protection rules in learning mode (i.e., set the application behavior mode to learning). In this mode, the EPS agent learns which applications are running scripts and will not block their usage once you change to blocking mode.
For example, using file protection rules, you can configure the following rule: Don’t allow WSCRIPT and CSCRIPT to run *.JS files. Once enforced, users will not be able to use the Microsoft scripting engine (WSCRIPT/CSCRIPT) to run .JS files. Make sure to enable the Allow trusted files to bypass the rule option to bypass this protection for applications that were discovered using WSCRIPT to run .JS files during the learning period.
Execution chain and internet origin blocking
Two new options were added in 2017.1 to file protection rules that help block users from running scripts from a browser or mail application even though the scripts were downloaded inside a zip file.
- Apply if process is in the execution chain
- Apply only to files downloaded from internet
When the Apply if process is in the execution chain option is enabled, monitored programs are any program in the “chain of execution.” For example, if a user runs Chrome and opens a .JS file downloaded by Chrome (i.e., the user double-clicks the .JS file after it has been downloaded by Chrome), the chain of execution will be Chrome > WSCRIPT > .JS. When this option is enabled, the “monitored program” can be Chrome and the “protected files” can be *.JS. This will ensure any JS file that runs from Chrome is blocked.
In 2017.1 there's also a new out-of-the-box file protection rule that is designed to prevent script execution from a browser or a mail application. This rule prevents a set of defined browsers and mailers from running CMD, CSCRIPT, WSCRIPT, and PowerShell. It will block any attempt to run a script by a browser or a mail app (this applies only to scripts that run “outside” the browser—not JavaScript running in the browser as part of a website).
There is one common case where using Apply if process is in the execution chain will not block the execution of scripts—when the script is packed into a zip file and the user extracts the zip using the native Windows ZIP extractor (not a third-party app). However, this rule will work to block an attachment zip file if a user opens it with WINZIP and then runs a script which was inside the zip file.
To solve the above problem, a second option, Apply only to files downloaded from the Internet, is available. By default, every file that is downloaded by a browser is flagged by the browser as “downloaded from the internet.” This flag is kept with the file even if the file is copied (note that this flag only applies to files on a NTFS file system). When this option is enabled, the rule will only apply to files that have this flag enabled.
A new out-of-the-box rule uses this feature to prevent script execution from files downloaded from the internet by a browser (“Prevent access to downloaded scripts”). When a user downloads a zip file from the internet, if the zip includes a script (.BAT, .CMD, .JS, .VBS), the script will be blocked from executing, even if the zip was extracted using the native Windows zip application and even if the file was saved to disk and extracted at a later stage.
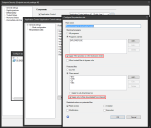
To enable execution chain or internet origin options in a file protection rule
- Click Tools > Security and compliance > Agent settings.
- In the tree under Agent settings > My agent settings > Security > Endpoint Security, right-click and click New, or double-click an existing configuration.
- On the Default policy page, select the application control setting you want to modify and edit it.
- On the File protection rules page, modify or add the rule you want.
- You'll see the Apply if process is in the execution chain option and the Apply only to files downloaded from internet option on the rule configuration page.