Configure Ivanti Firewall settings
The Ivanti Firewall tool is an important component of Endpoint Security that lets you protect managed devices from unauthorized application operations and connections.
With Ivanti Firewall settings, you can create and configure trusted programs (applications), trusted network scopes, and connection rules to protect managed devices from unauthorized intrusions.
IMPORTANT: Ivanti Firewall and Windows Firewall compatibility
The Ivanti Firewall complements the Windows Firewall, and both can be enabled and running at the same time on managed devices.
Component of Endpoint Security
Ivanti Firewall is one of the components of the comprehensive Endpoint Security solution, along with the Application Control and Device Control tools.
Read this chapter to learn about:
Using Ivanti Firewall settings
Firewall settings give you complete control over how the Ivanti Firewall operates hon target devices.
This section describes how to create and manage Firewall settings.
Creating Ivanti Firewall settings
To create Ivanti Firewall settings
- In the Agent Settings tool window, click Security > Endpoint Security, right-click Ivanti Firewall and then click New.
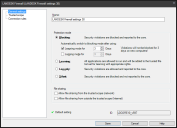
- On the General settings page, enter a name for the settings, enable the Ivanti Firewall service, and then specify the
- On the Connection rules page, define the connection rules (incoming or outgoing, and action) by port, protocol, or IP range.
- Click Save.
Once configured, you can deploy settings to target devices with an installation or update task, or a change settings task.
Ivanti Firewall settings help
Use this dialog to create and edit Ivanti Firewall settings. When creating Firewall settings, you first define the general protection mode, and then add and configure specific trusted file lists, trusted scopes, and connection rules. You can create as many settings as you like and edit them at any time.
If you want to modify the device default settings without reinstalling the Endpoint Security agent or redeploying a full agent configuration, make your desired change to any of the options on the settings dialog, assign the new settings to a change settings task, and then deploy the change settings task to target devices.
This dialog contains the following pages.
About the General settings page
Use this page to enable the Ivanti Firewall and configure the protection mode.
This page contains the following options:
- Name: Identifies the Firewall settings with a unique name.
- Enable Ivanti Firewall: Allows all programs to run except when a program's operation threatens system security as defined by predefined protection rules.
- Protection mode: Specifies protection behavior when security violations occur on managed devices.
- Blocking: All security violations are automatically blocked. In other words, all of the trusted program, trusted scope and connection rules (i.e., permissions) you've created are enforced.
- Learning mode for: Allows the administrator to specify a period of time during which the end user can run any of the applications on their machine. During this period, applications that run are observed.
NOTE: These two time period options are executed successively. In other words, if both are selected, the learning mode period runs first and when it expires the logging mode period runs.
- Logging mode for: Specifies a period of time during which the applications that run are recorded in an action history file on the core server.
- Learning mode for: Allows the administrator to specify a period of time during which the end user can run any of the applications on their machine. During this period, applications that run are observed.
- Learning: All applications are allowed to run. Additionally, all of the applications that are run on the device are learned and added to the trusted file list.
- Log only: Security violations are allowed, but are recorded in an action history file on the core server.
- File sharing: Specifies file sharing privileges allowed by the Ivanti Firewall settings.
- Allow file sharing from the trusted scope (network): Allows files to be shared within the trusted scope you've defined.
- Allow file sharing from outside the trusted scope (Internet): Allows files to be shared outside of the trusted scope you've defined.
About the Trusted scope dialog box
Use this page to configure and manage trusted scopes. A trusted scope is made up of a collection of network addresses, by IP address, IP range, or subnet.
This page contains the following options:
- Trust client's subnet: Adds the target device's subnet range to the trusted scope list. Communication across that subnet range is allowed.
- Trusted scope: Lists all of the trusted scopes.
- Add...: Lets you add a trusted location to the list. Add a trusted location by IP address, IP range, or subnet.
- Edit...: Lets you modify the selected existing trusted location.
- Delete: Removes the selected trusted location.
- Batch import IP address... Lets you select multiple
- Import...: Lets you import subnet ranges from managed devices contained in the core database inventory.
About the Connection rules dialog box
Use this page to view, manage, and prioritize connection rules. Connection rules can allow or prevent connections based on port or IP range, whether the program is trusted, and whether the communication is within the trusted network scope.
This page contains the following options:
- Connection rules: Lists all of the connection rules.
- Move up: Determines the priority of the connection rule. A connection rule higher in the list takes precedence over a rule that is lower in the list.
- Move down: Determines the priority of the connection rule.
- Reset: Restores the rule order.
- Add: Opens a dialog where you can configure a new connection rule.
- Edit: Lets you modify the selected connection rule.
- Delete: Removes the connection rule from the database.
About the Configure connection rule dialog box
Use this page to configure connection rules.
This page contains the following options:
- Name: Identifies the connection rule with a descriptive name.
-
Direction: Indicates whether the connection rule restricts inbound or outbound connections.
- Action: Indicates whether the connection rule allows (accepts) or prevents (drops) connections.
- Protocol: Specifies the communication protocol for the selected ports.
- Ports: Lets you define port restrictions for the connection rule.
- Apply to these local ports: Specifies the local ports to which the direction and action (selected below) are applied. For example, if Incoming is selected and Accept is selected, connections to the local ports specified here are allowed.
- Apply to these remote ports: Specifies the remote ports to which the direction and action (selected below) are applied.
- IP address range: Lets you define IP range restrictions for the connection rule.
- Apply to these remote addresses: Specifies the remote IP address range to which the direction and action (selected below) are applied.
- Allow trusted programs to bypass: Lets you give trusted programs the ability to ignore or bypass this connection rule.
- Only for trusted scope: Limits the trusted programs' ability to bypass the connection rule only if the communication is within the trusted network scope.
- OK: Saves the options and adds the rule to the list of connection rules.
- Cancel: Closes the dialog without saving.